A Clever Phishing Campaign Is Targeting Office 365 Users Help Net Security
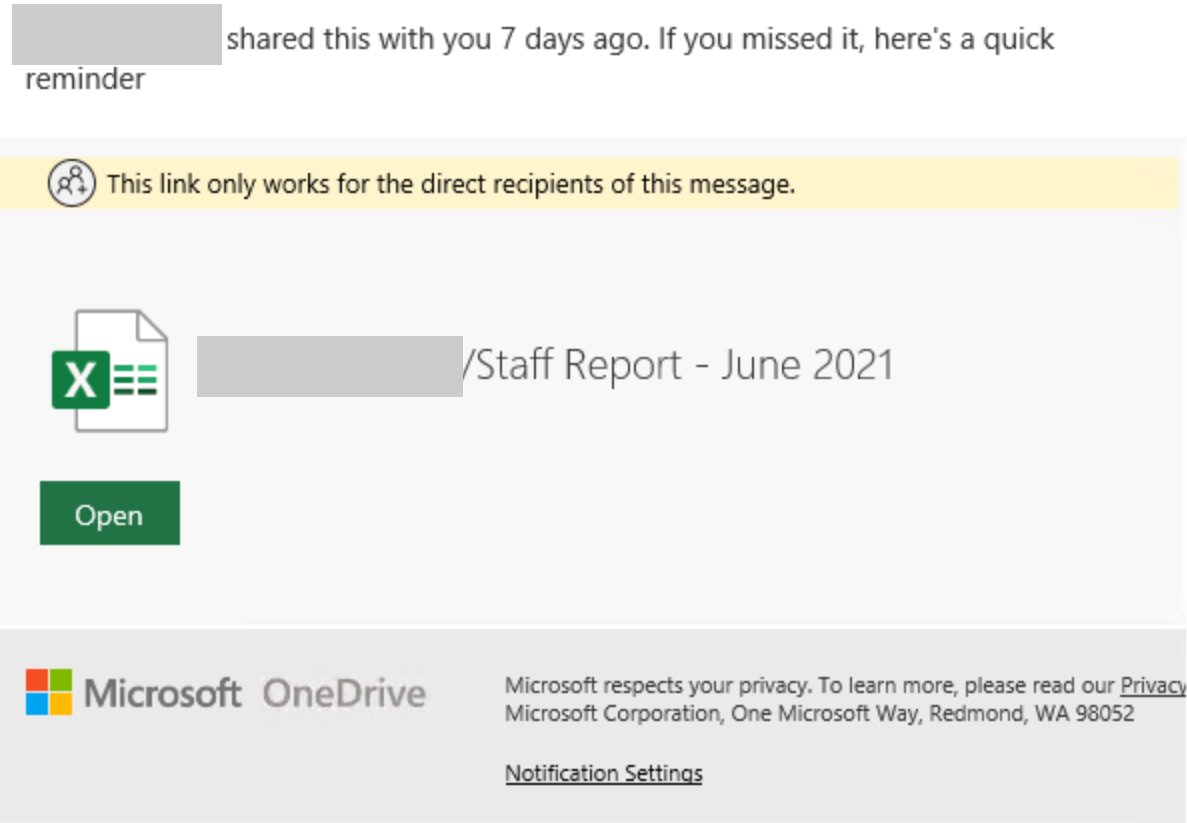
A Clever Phishing Campaign Is Targeting Office 365 Users Help Net Security Tl;dr: we introduce clever, a hand curated benchmark for verified code generation in lean. it requires full formal specs and proofs. no few shot method solves all stages, making it a strong testbed for synthesis and formal reasoning. Tl;dr: we propose the first attack independent robustness metric, a.k.a clever, that can be applied to any neural network classifier.

Corporate Office 365 Users Hit With Clever Phishing Attack Help Net Security Leaving the barn door open for clever hans: simple features predict llm benchmark answers lorenzo pacchiardi , marko tesic , lucy g cheke , jose hernandez orallo 27 sept 2024 (modified: 05 feb 2025). 016 namely clever, which is augmentation free 017 and mitigates biases on the inference stage. 018 specifically, we train a claim evidence fusion 019 model and a claim only model independently. 020 then, we obtain the final prediction via sub 021 tracting output of the claim only model from 022 output of the claim evidence fusion model,. 4clever: curated lean verified code generation bench mark microkernel. however, writing formal specifications and correctness proofs for software systems can take tremen dous effort — for example, the development of sel4 was reported to take 20 person years. these costs are a key impediment to the broad deployment of itp based formal. Functionally, mambano achieves a clever balance between global integration, facilitated by state space model of mamba that scans the entire function, and local integration, engaged with an alias free architecture.

Ongoing Office 365 Themed Phishing Campaign Targets Executives Assistants Financial 4clever: curated lean verified code generation bench mark microkernel. however, writing formal specifications and correctness proofs for software systems can take tremen dous effort — for example, the development of sel4 was reported to take 20 person years. these costs are a key impediment to the broad deployment of itp based formal. Functionally, mambano achieves a clever balance between global integration, facilitated by state space model of mamba that scans the entire function, and local integration, engaged with an alias free architecture. This is where safety alignment comes in. one common approach is training models to refuse unsafe queries, but this strategy can be vulnerable to clever prompts, often referred to as jailbreak attacks, which can trick the ai into providing harmful responses. Composed query image retrieval task aims to retrieve the target image in the database by a query that composes two different modalities: a reference image and a sentence declaring that some details of the reference image need to be modified and replaced by new elements. Super deep contrastive information bottleneck for multi modal clustering zhengzheng lou 1ke zhang yucong wu shizhe hu1. Tl;dr: we provably optimally approximate full fine tuning in low rank subspaces throughout the entire training process using a clever initialization scheme, achieving significant gains in parameter efficiency.

How Can Office 365 Phishing Threats Be Addressed Help Net Security This is where safety alignment comes in. one common approach is training models to refuse unsafe queries, but this strategy can be vulnerable to clever prompts, often referred to as jailbreak attacks, which can trick the ai into providing harmful responses. Composed query image retrieval task aims to retrieve the target image in the database by a query that composes two different modalities: a reference image and a sentence declaring that some details of the reference image need to be modified and replaced by new elements. Super deep contrastive information bottleneck for multi modal clustering zhengzheng lou 1ke zhang yucong wu shizhe hu1. Tl;dr: we provably optimally approximate full fine tuning in low rank subspaces throughout the entire training process using a clever initialization scheme, achieving significant gains in parameter efficiency.

How Can Office 365 Phishing Threats Be Addressed Help Net Security Super deep contrastive information bottleneck for multi modal clustering zhengzheng lou 1ke zhang yucong wu shizhe hu1. Tl;dr: we provably optimally approximate full fine tuning in low rank subspaces throughout the entire training process using a clever initialization scheme, achieving significant gains in parameter efficiency.

Phishing Attacks Targeting Office 365 Users Cybersecurity Products And Consulting
Comments are closed.