Aws Supports You Exploring Cloudfront Security Features And Best Practices
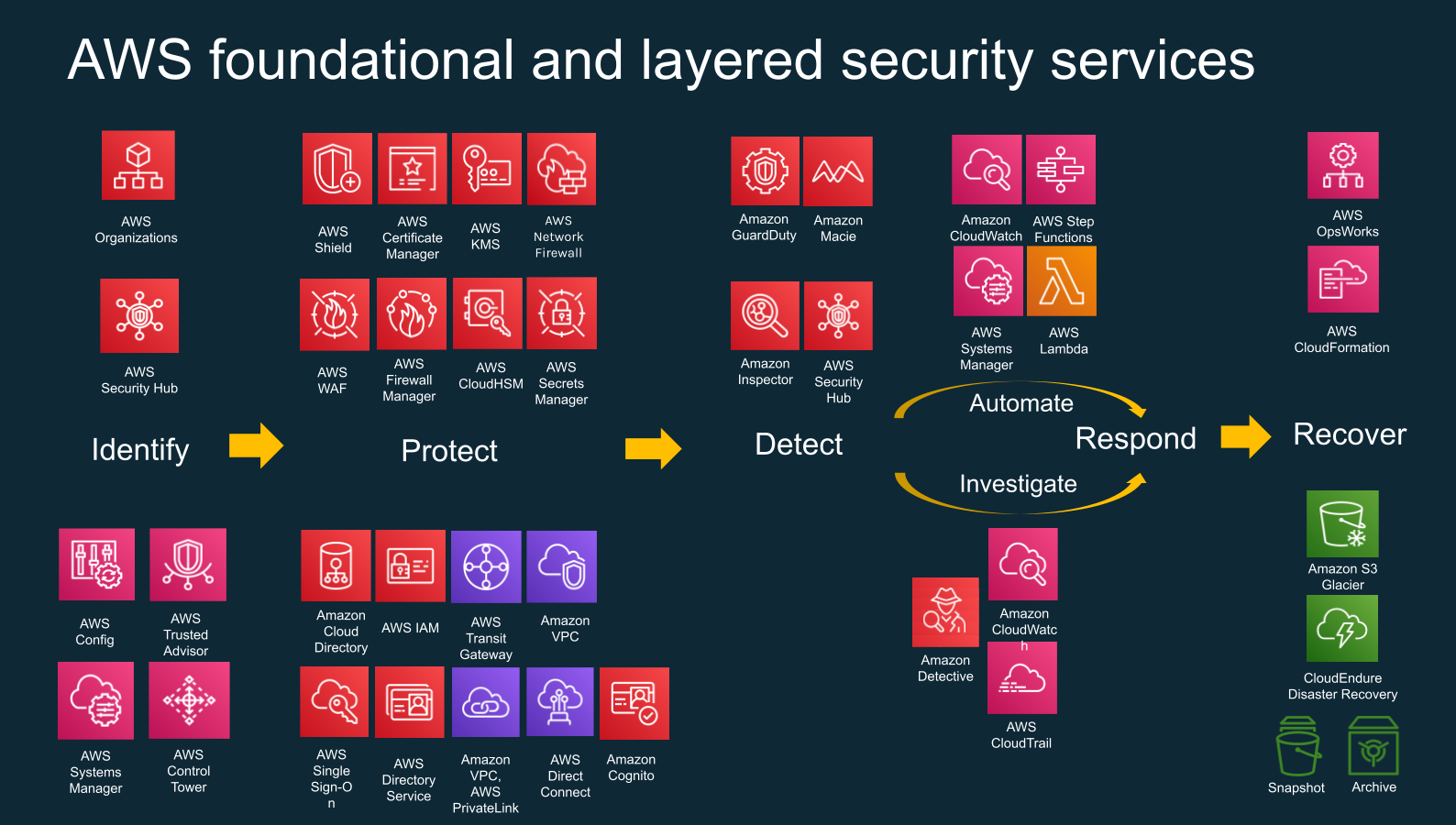
Aws Security Best Practices Cyphere The following topics show you how to configure cloudfront to meet your security and compliance objectives. you also learn how to use other aws services that help you to monitor and secure your cloudfront resources. You can now better protect your cloudfront distributions with aws waf security recommendations in the cloudfront console. cloudfront conveniently displays additional security rules for your distributions based on elements of your cloudfront configuration including path patterns or your origin type.
Aws Cloud Security Best Practices By following these best practices and leveraging the comprehensive security features offered by aws cloudfront, you can confidently deliver your content to the world while safeguarding your valuable data and reputation. This guide provides comprehensive information on amazon cloudfront’s security recommendations and how to implement them effectively. we will cover the new one click security protections, configuration recommendations, and additional techniques to optimize security using cloudfront. In this article, we will explore the security features and best practices that make aws cloudfront a top choice for businesses and organizations looking to protect their data in the cloud. Cloudfront security covers encryption features, restricting access, enforcing https, geo restriction, field level encryption, etc.

Aws Security Best Practices Comprehensive Checklist For Success In this article, we will explore the security features and best practices that make aws cloudfront a top choice for businesses and organizations looking to protect their data in the cloud. Cloudfront security covers encryption features, restricting access, enforcing https, geo restriction, field level encryption, etc. This conformance pack contains aws config rules based on amazon cloudfront. for a list of all managed rules supported by aws config, see list of aws config managed rules. However, ensuring the security of your content on cloudfront is essential to protect your assets from various online threats. in this article, we will discuss some best practices to enhance the security of your aws cloudfront distribution. Your current architecture might work for testing or low traffic environments, but aws recommends some best practices to make it more secure and production ready. Discover how to optimize security with aws cloudfront. learn about https encryption, origin access identity, access restrictions, web application firewall, caching, monitoring, and maintenance best practices.

Aws Foundational Security Best Practices Standard Now Available In Security Hub Aws Security Blog This conformance pack contains aws config rules based on amazon cloudfront. for a list of all managed rules supported by aws config, see list of aws config managed rules. However, ensuring the security of your content on cloudfront is essential to protect your assets from various online threats. in this article, we will discuss some best practices to enhance the security of your aws cloudfront distribution. Your current architecture might work for testing or low traffic environments, but aws recommends some best practices to make it more secure and production ready. Discover how to optimize security with aws cloudfront. learn about https encryption, origin access identity, access restrictions, web application firewall, caching, monitoring, and maintenance best practices.
Comments are closed.