Bug Bounty File Upload Vulnerabilities Via Pdf Files 2023

Bug Bounty Video Collection Pdf Pdf Hypertext Transfer Protocol Encryption In this video, you will learn how we can upload malicious pdf files to do cross site scriptingw. Find a local file inclusion vulnerability to execute the backdoor. uploading a file with “.”, “ ”, or “ ” as its name. for instance, in apache in windows, if the application saves the uploaded files in “ www uploads ” directory, the “.” filename will create a file called “uploads” in the “ www ” directory.

Bug Bounty Content Pdf Everyone knows what is a “ bad pdf ”, so i found this upload feature for my target website from the uploaded pdf. the most site which uses documents and other sensitive verification process. Hello everyone, one of the most interesting functions is file uploading, vulnerabilities in file uploads usually lead you to critical or high severity, so let’s start with this scenario that i faced while bug bunting. zoom image will be displayed. let’s consider our target domain is target . File upload vulnerabilities represent a critical threat to web servers. these vulnerabilities occur when a web server allows users to upload files without adequately verifying essential. Embark on the first part of a comprehensive guide on file upload attacks. delve into various attack vectors, understand the risks involved, and learn how to identify and exploit vulnerable file upload functionalities to enhance your bug bounty hunting skills.

Bug Bounty Pdf Security Computer Security File upload vulnerabilities represent a critical threat to web servers. these vulnerabilities occur when a web server allows users to upload files without adequately verifying essential. Embark on the first part of a comprehensive guide on file upload attacks. delve into various attack vectors, understand the risks involved, and learn how to identify and exploit vulnerable file upload functionalities to enhance your bug bounty hunting skills. Using a url list for security testing can be painful as there are a lot of urls that have uninteresting duplicate content; uro aims to solve that. this is a simple tool meant to work in a pipeline of other scripts. it takes domains on stdin and outputs them on stdout if they resolve. File uploading vulnerability where an application allows a user to upload a malicious file directly which is then executed. method1:bypassing file uploading restrictions. if the. In conclusion, users and organizations generally do not anticipate malicious scripts within pdf documents. developers should implement robust security checks for pdf files within their. File upload functionality is a common feature in web applications, but it also introduces severe security risks if not implemented correctly. attackers often exploit weak validation mechanisms to upload malicious files, gain unauthorized access, or execute arbitrary code on a server.

Bug Bounty Pdf Using a url list for security testing can be painful as there are a lot of urls that have uninteresting duplicate content; uro aims to solve that. this is a simple tool meant to work in a pipeline of other scripts. it takes domains on stdin and outputs them on stdout if they resolve. File uploading vulnerability where an application allows a user to upload a malicious file directly which is then executed. method1:bypassing file uploading restrictions. if the. In conclusion, users and organizations generally do not anticipate malicious scripts within pdf documents. developers should implement robust security checks for pdf files within their. File upload functionality is a common feature in web applications, but it also introduces severe security risks if not implemented correctly. attackers often exploit weak validation mechanisms to upload malicious files, gain unauthorized access, or execute arbitrary code on a server.
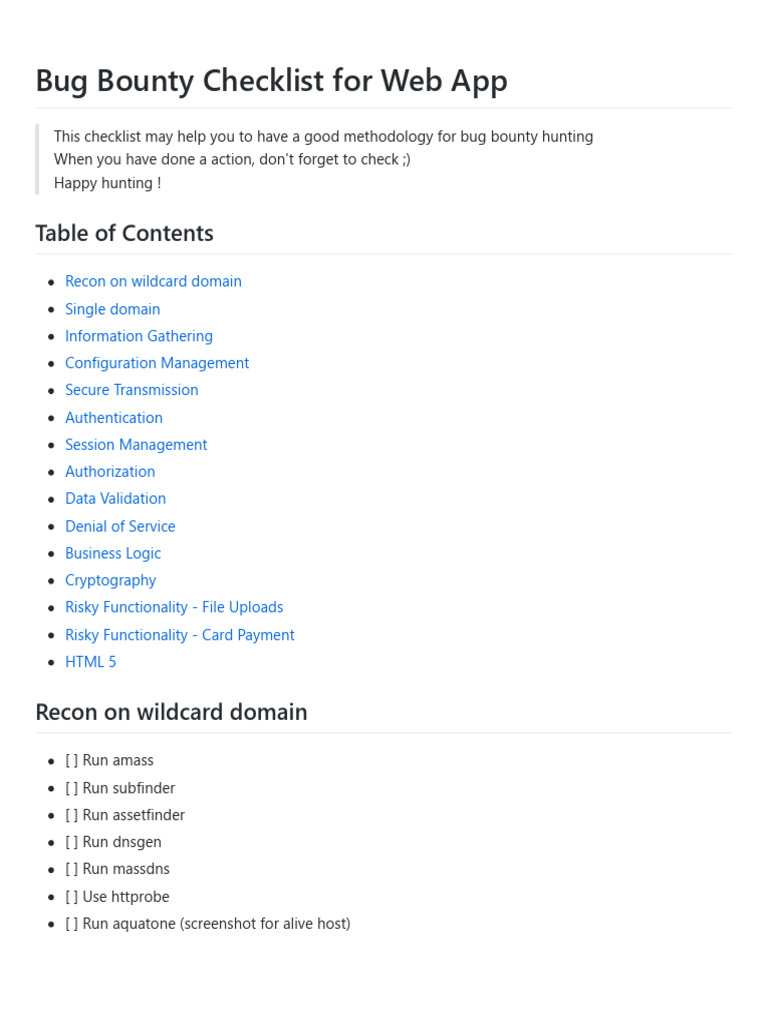
Bug Bounty Checklist Pdf World Wide Web Internet Web In conclusion, users and organizations generally do not anticipate malicious scripts within pdf documents. developers should implement robust security checks for pdf files within their. File upload functionality is a common feature in web applications, but it also introduces severe security risks if not implemented correctly. attackers often exploit weak validation mechanisms to upload malicious files, gain unauthorized access, or execute arbitrary code on a server.
Comments are closed.