Bypass Otp Verification With Burp Suite Response Manipulation Method Ethical Hacking Itspyguru

Bypass Otp Using Burp Suite Pdf Security Technology Computer Security Discover how to bypass otp (one time password) verification using burp suite's response manipulation method. But what if i told you this trust can be easily broken — not by brute force, but by a simple client side response manipulation? in this article, i’ll walk you through a real world case study.

Otp Bypass Using Response Manipulation Telegraph It includes step by step instructions on intercepting, analyzing, and manipulating otp requests, along with best practices for mitigating these vulnerabilities. this project demonstrates the process of bypassing one time password (otp) authentication using burp suite. This article demonstrates several methods to bypass otp (one time password) verification during account registration or login processes using burpsuite. these techniques can potentially lead to unauthorized access to user accounts, resulting in account takeover. We are now going to use response manipulation here. change the 400 error response to “200 ok” and the incorrect otp response to “otp verified successfully”. To test this method enter any random otp and intercept the request and the response of that request and you will see the response as an error or false. change that into success or true and then forward the request, if it is being processed then you have successfully bypassed the otp verification.
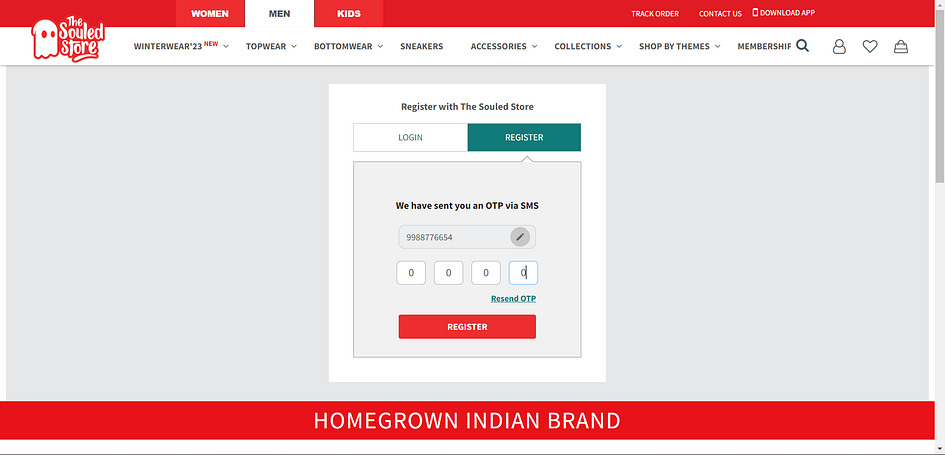
Otp Bypass Using Response Manipulation Telegraph We are now going to use response manipulation here. change the 400 error response to “200 ok” and the incorrect otp response to “otp verified successfully”. To test this method enter any random otp and intercept the request and the response of that request and you will see the response as an error or false. change that into success or true and then forward the request, if it is being processed then you have successfully bypassed the otp verification. One time password (otp) bypass via response manipulation is a critical vulnerability that can allow attackers to bypass authentication mechanisms. this technique involves manipulating the server’s response to trick the system into believing that the correct otp has been entered, even when it hasn’t. This document outlines various otp bypass techniques, including response manipulation, rate limit exploitation, default otp usage, and session validation flaws. Broken authentication vulnerability explained by otp bypass through response manipulation using burp suite. otp bypass is caused due to insecure design and implementation of web. When a user enters their otp, the application sends a request to the server for verification. an attacker can intercept this request using tools like burp suite or postman.
Comments are closed.