Checkpoint Zone Based Policy Networkershome

Lab 05 Configuring Zone Based Policy Firewalls Pdf Computer Network Router Computing Join live networking trainings with lab access at networkers home networkershome in this video, we dive into the fundamentals of checkpoint'. Security zones let you to create a strong access control policy that controls the traffic between parts of the network. a security zone object represents a part of the network (for example, the internal network or the external network).
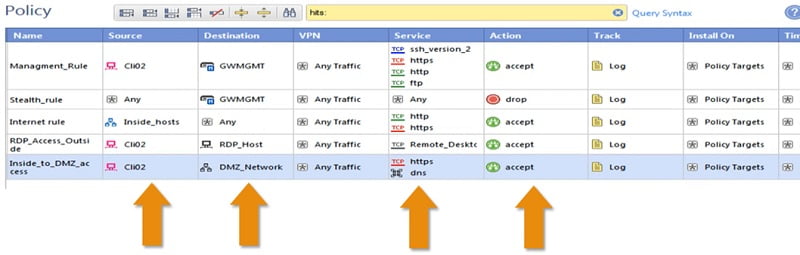
Checkpoint Firewall Policy Rules Configuration Network Interview Join live networking trainings with lab access at networkers home networkershome welcome to our checkpoint firewall training! in this video,. In a zone based firewall i can say "everything that comes from this interface should be treated this way" without worrying about the ip addresses at all. you can achieve the same thing in an interface based firewall, but you have to know (and define) every ip address reachable from that firewall. Check point r81 lab guides for beginners:this is a check point r81 lab guide on how to configure security zone based access control policy in check point fir. Join live networking trainings with lab access at networkers home networkershome in this video, we dive into the fundamentals of zone based.
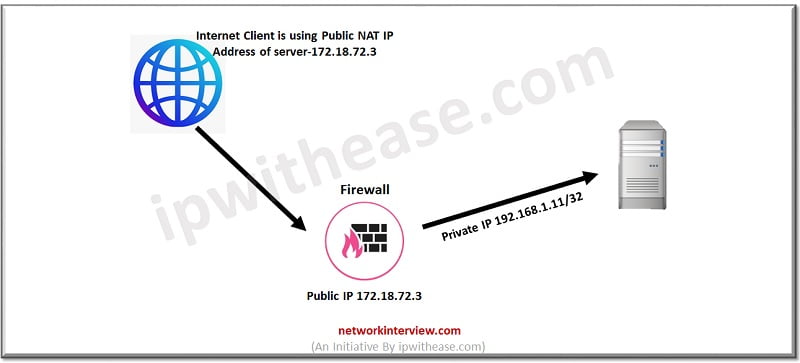
Checkpoint Nat Policy Types Configuration Network Interview Check point r81 lab guides for beginners:this is a check point r81 lab guide on how to configure security zone based access control policy in check point fir. Join live networking trainings with lab access at networkers home networkershome in this video, we dive into the fundamentals of zone based. The main component of the access zones policy rule is the definition of the trusted zone. all objects that are not in the trusted zone are automatically in the internet zone . if necessary, you can create new trusted zone objects to use in different policy rules. Day 07 destination nat, zone based, firewalling (21:35) day 08 manage multi policies and layers on check point firewall (18:29). With security zones you can create a strong access control policy that controls the traffic between parts of the network. a security zone object represents a part of the network (for example, the internal network or the external network). Security zones let you create a strong firewall policy that controls the traffic between parts of the network. a security zone object represents a part of the network (for example, the internal network or the external network).
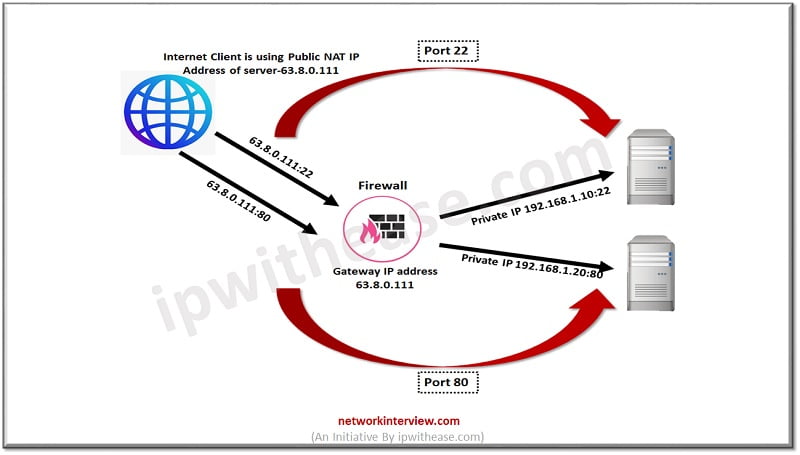
Checkpoint Nat Policy Types Configuration Network Interview The main component of the access zones policy rule is the definition of the trusted zone. all objects that are not in the trusted zone are automatically in the internet zone . if necessary, you can create new trusted zone objects to use in different policy rules. Day 07 destination nat, zone based, firewalling (21:35) day 08 manage multi policies and layers on check point firewall (18:29). With security zones you can create a strong access control policy that controls the traffic between parts of the network. a security zone object represents a part of the network (for example, the internal network or the external network). Security zones let you create a strong firewall policy that controls the traffic between parts of the network. a security zone object represents a part of the network (for example, the internal network or the external network).
Comments are closed.