Cloud Native Security Part 2

Cloud Native Security Part 2 This webcast supports content and knowledge from sec540: cloud native security and devsecops automation™. to learn more about this course, explore upcoming sessions, and access your free demo, click here. In the first part of this series, we introduced some concepts specific to cloud native security, in particular the “4 c’s of cloud native security”. we gave a number of leads and insights about securing kubernetes as a platform.

Cloud Native Security Part 2 Next up, we will use gitops and ci cd to build and deploy the cloud infrastructure. for now, here’s my demo video for this part 2: cisco secure cloud native security – part 2.1 – setting up the dev environment. if you are reading this, it means you are interested to learn the details of this set up. let’s jump right in!. In this chapter, we will review how to secure cloud native applications. due to the dynamic nature of the cloud native application, we need to begin securing our application stack from the initial steps of the ci cd pipeline. Coupled with the 700% increase in the number of enterprise users connecting remotely due to covid 19, we immediately understand the importance of securing the cloud native stack. this stack is composed of all the elements described below and every single part of it should be protected. It took a while to get back , but i hope i make it worthwhile for the wait 🙂 this week we will read about how to secure resource during runtime and obtain security assurance in our environment.
.png)
Cncf Cloud Native Security India Coupled with the 700% increase in the number of enterprise users connecting remotely due to covid 19, we immediately understand the importance of securing the cloud native stack. this stack is composed of all the elements described below and every single part of it should be protected. It took a while to get back , but i hope i make it worthwhile for the wait 🙂 this week we will read about how to secure resource during runtime and obtain security assurance in our environment. In this chapter, we will review security considerations when building cloud native applications. identity and access management plays a crucial role when designing new applications. we need to ask ourselves – who are our customers?. An outline of the corresponding security mechanisms, monitoring, observability, and security tooling is depicted in the figure below. let’s take a closer look at how the infrastructure security, security of workload deployment at each stage, and security within devops process are achieved. Implementing the native security features of kubernetes is critical. while there is no way to discover all the vulnerabilities within a container environment without dedicated kubernetes security tools, you can apply several best practices to start using kubernetes’ native security features. These conversations cover the state of cloud native security, getting a holistic view of your cloud native environment, security challenges for kubernetes, and the state of the software supply chain.
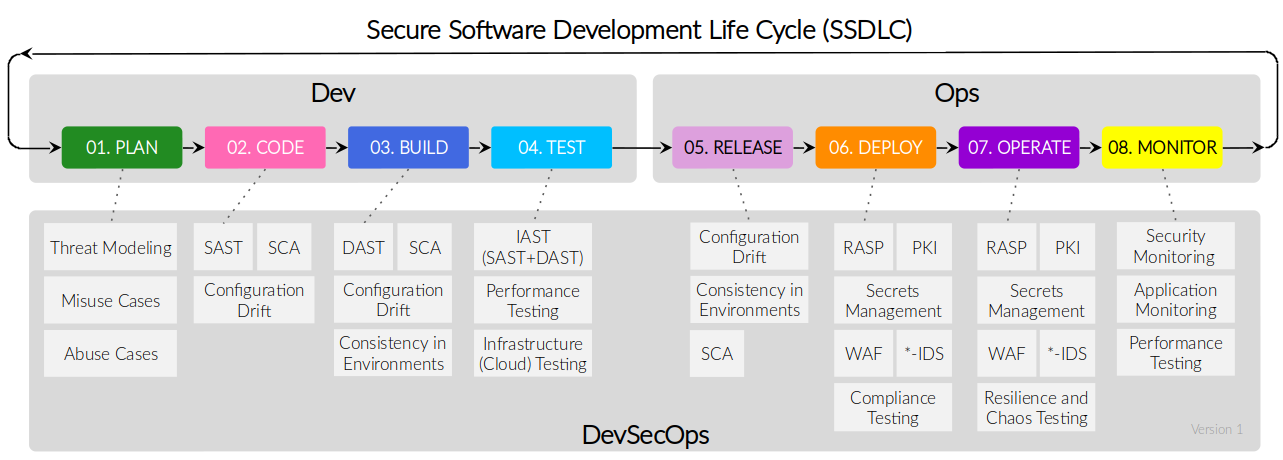
Security Cloud Native Workshop Workshop Cloud Native Security In this chapter, we will review security considerations when building cloud native applications. identity and access management plays a crucial role when designing new applications. we need to ask ourselves – who are our customers?. An outline of the corresponding security mechanisms, monitoring, observability, and security tooling is depicted in the figure below. let’s take a closer look at how the infrastructure security, security of workload deployment at each stage, and security within devops process are achieved. Implementing the native security features of kubernetes is critical. while there is no way to discover all the vulnerabilities within a container environment without dedicated kubernetes security tools, you can apply several best practices to start using kubernetes’ native security features. These conversations cover the state of cloud native security, getting a holistic view of your cloud native environment, security challenges for kubernetes, and the state of the software supply chain.

Cloud Native Security With Michael Isbitski Implementing the native security features of kubernetes is critical. while there is no way to discover all the vulnerabilities within a container environment without dedicated kubernetes security tools, you can apply several best practices to start using kubernetes’ native security features. These conversations cover the state of cloud native security, getting a holistic view of your cloud native environment, security challenges for kubernetes, and the state of the software supply chain.

Cloud Native Security Model
Comments are closed.