Cyber Security Introduction Cyber Security Part 1

Cyber Security Introduction Pdf Malware Security Cyber physical convergence scenarios. physical impacts resulting from a cyber threat vector, or cyber impacts resulting from a physical threat vector. while cteps within the cyber and physical sections may touch on these subjects, convergence cteps are designed to further explore the impacts of convergence and how to enhance one’s resiliency. Cybersecurity advisory: in depth reports covering a specific cybersecurity issue, often including threat actor tactics, techniques, and procedures; indicators of compromise; and mitigations.

Introduction To Cyber Security Pdf Computer Security Security This diverse team proactively gathers, analyzes, and shares actionable cyber risk information to enable synchronized, holistic cybersecurity planning, cyber defense, and response. view resources stopransomware.gov is the u.s. government's official one stop location for resources to tackle ransomware more effectively. Authentication is a process used to validate a user's identity. attackers commonly exploit weak authentication processes. mfa uses at least two identity components to authenticate a user's identity, minimizing the risk of a cyber attacker gaining access to an account if they know the username and password. (supplementing passwords.) install a. Summary. the federal bureau of investigation (fbi), cybersecurity and infrastructure security agency (cisa), royal canadian mounted police (rcmp), australian signals directorate’s (asd’s) australian cyber security centre (acsc), australian federal police (afp), canadian centre for cyber security (cccs), and united kingdom’s national cyber security centre (ncsc uk)—hereafter referred to. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild. organizations should use the kev catalog as an input to their vulnerability management prioritization framework.how to use the kev.

Chapter 1 Introduction Overview Pdf Security Computer Security In this role, he leads the department's enterprise wide it strategy, cybersecurity operations, and digital modernization efforts. with over 18 years of experience in cyber operations and national security, mr. mccord is committed to enhancing cyber resilience and operational effectiveness to support core dhs missions and activities. Bulletins provide weekly summaries of new vulnerabilities. patch information is provided when available. Cybersecurity best practices, organizations and cyber safety, industrial control systems cisa offers free industrial control systems (ics) cybersecurity training to protect against cyberattacks on critical infrastructure, such as power grids and water treatment facilities. There are 16 critical infrastructure sectors whose assets, systems, and networks, whether physical or virtual, are considered so vital to the united states that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.

Introduction To Cyber Security Cybersecurity best practices, organizations and cyber safety, industrial control systems cisa offers free industrial control systems (ics) cybersecurity training to protect against cyberattacks on critical infrastructure, such as power grids and water treatment facilities. There are 16 critical infrastructure sectors whose assets, systems, and networks, whether physical or virtual, are considered so vital to the united states that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.

Introduction To Cyber Security Pdf

Introduction To Cyber Security Pdf

Introduction To Cyber Security Pdf Computer Security Security

Day 18 Introduction To Cyber Security Pdf Computer File Directory Computing

Introduction To Cyber Security Part 1 2 Notexchange

Introduction To Cyber Security

Section 1 Cyber Security Introduction And Overview Pdf Threat Computer Computer Security

Cyber Security Introduction Pdf Malware Security

Introduction To Cybersecurity Pdf

Cyber Security Chapter 1 Pdf Cybercrime Spamming

Ch1 Introduction Pdf Computer Security Security

Introduction To Cyber Security

Introduction To Cyber Security

Cyber Security Introduction Pdf Security Computer Security

Introduction To Cyber Security Pdf Security Computer Security

How Much Cybersecurity Expertise Does A Board Need The Mccormick Group

Intro To Cyber 1 Pdf Security Computer Security

Introduction To Cybersecurity Tps
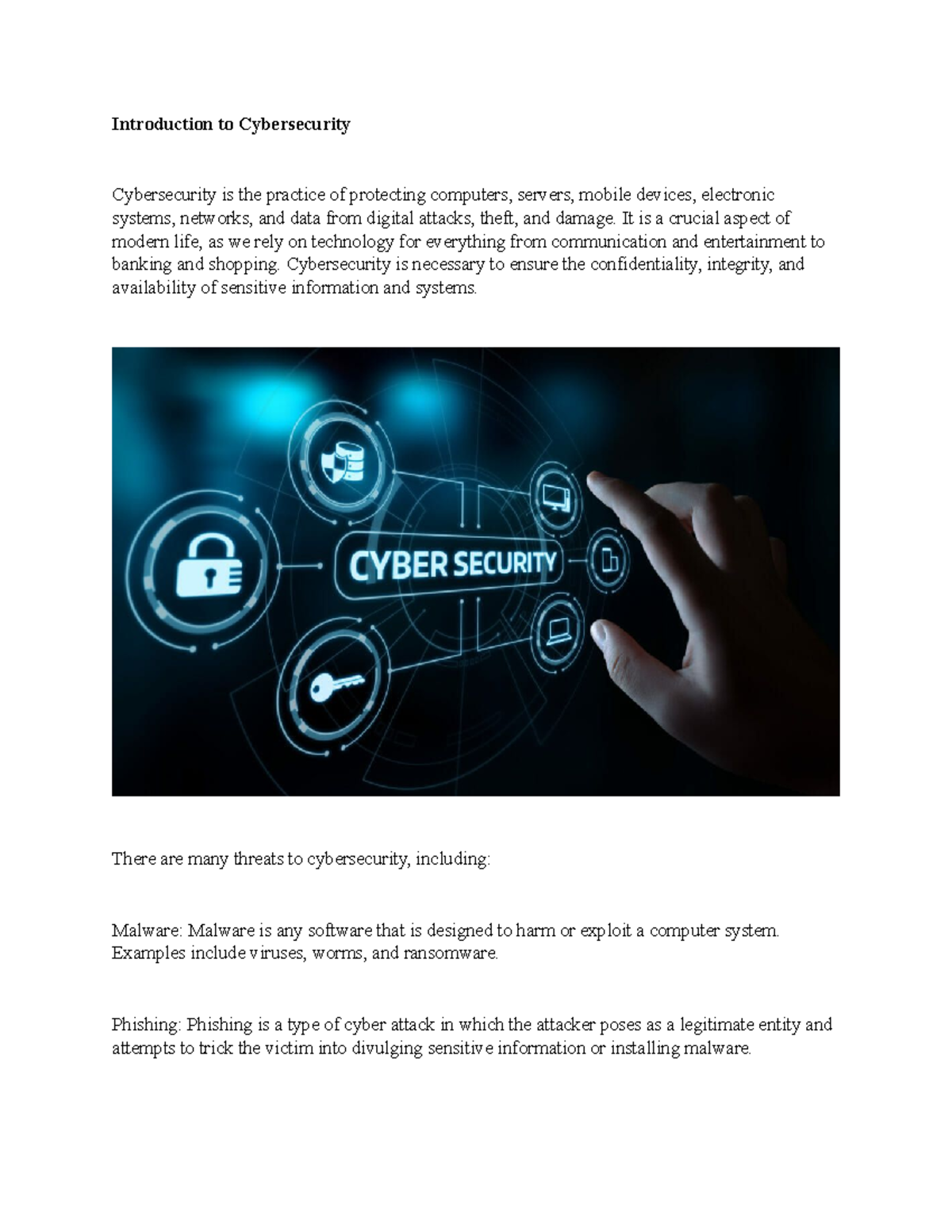
Introduction To Cybersecurity Introduction To Cybersecurity Cybersecurity Is The Practice Of

Introduction To Cyber Security

Introduction To Cyber Security Pdf

W1 2 Module 1 Introduction To Cyber Security Pdf Security Computer Security

Introduction To Cyber Security By Cyber Security Infotech Csi

Introduction To Cyber Security Introduction To Cyber Security Cybersecurity Is The Practice Of
Introduction To Cybersecurity Pdf Security Computer Security

Introduction To Cyber Security Pdf Security Computer Security

Cyber Security Introduction Part 1 Dev Community Bank2home

Introduction To Cybersecurity Ministry Of Security

Introduction To Cybersecurity Ciso2ciso Com Cyber Security Group

Bab 1 Pengantar Cyber Security Pdf

Introduction To Cyber Security
Comments are closed.