Cyber Security Is Not For You If You Fall Into One Of These Categories
7 Cybersecurity Tips Nobody Tells You But Are Easy To Do You receive an e mail marked important from your agency head asking you to call them using a number you do not recognize. the e mail was sent from a personal e mail address that you do not recognize, but it addresses you by name. To help you decide if this is a career you should pursue, we’ve compiled some crucial questions in eight categories, including technical skills, ethics, and work environment.
Cybersecurity Quiz Explore the nist cybersecurity framework (csf) categories, to learn how to improve an organization’s ability to detect anomalous activity, respond to and recover from incidents as they occur, and identify vulnerabilities, such as the risks associated with file transfer software vulnerabilities. To effectively protect against various threats, cybersecurity can be categorized into several key areas, each targeting specific aspects of potential vulnerabilities. Cybersecurity tools are used to identify, protect against, and respond to various cyber threats. they fall into three main categories: prevention, detection, and response. tools in each category play a vital role in an organization’s defensive cybersecurity strategy. Dive into the key categories of cybersecurity including network, application, information, endpoint, and cloud security. learn how each area contributes to a comprehensive defense strategy against digital threats.

Why You Should Not Get Into Cybersecurity Cybersecurity tools are used to identify, protect against, and respond to various cyber threats. they fall into three main categories: prevention, detection, and response. tools in each category play a vital role in an organization’s defensive cybersecurity strategy. Dive into the key categories of cybersecurity including network, application, information, endpoint, and cloud security. learn how each area contributes to a comprehensive defense strategy against digital threats. Different types of cybersecurity categories and solutions are available to ensure the integrity of your network. and yet, what are some of the most prolific it security types you can use to safeguard you from attackers? let’s dive into them. how many types of cyber security are there?. Cybersecurity is a human right ultimately, cybersecurity is about dignity. it’s about preserving our autonomy, our freedom to speak and think and dream without fear of being watched or manipulated. in a world where data is currency and information is power, protecting your digital life is protecting your real life. Broadly speaking, ids systems fall into two categories: host based systems that are placed on a particular device, and network based systems that are placed on the network itself. ids can identify traffic that is universally indicative of malicious or otherwise suspicious activity, such as phishing, as well as browser specific attacks. Users will find that use of this threat taxonomy delivers real time context on malware, phishing, botnets, trojans and other threats, enabling faster, more confident incident investigation and response. 1. cyber threat category. 2. cyber threat type. 3. individual cyber threat.
Cybersecurity Quiz Different types of cybersecurity categories and solutions are available to ensure the integrity of your network. and yet, what are some of the most prolific it security types you can use to safeguard you from attackers? let’s dive into them. how many types of cyber security are there?. Cybersecurity is a human right ultimately, cybersecurity is about dignity. it’s about preserving our autonomy, our freedom to speak and think and dream without fear of being watched or manipulated. in a world where data is currency and information is power, protecting your digital life is protecting your real life. Broadly speaking, ids systems fall into two categories: host based systems that are placed on a particular device, and network based systems that are placed on the network itself. ids can identify traffic that is universally indicative of malicious or otherwise suspicious activity, such as phishing, as well as browser specific attacks. Users will find that use of this threat taxonomy delivers real time context on malware, phishing, botnets, trojans and other threats, enabling faster, more confident incident investigation and response. 1. cyber threat category. 2. cyber threat type. 3. individual cyber threat.
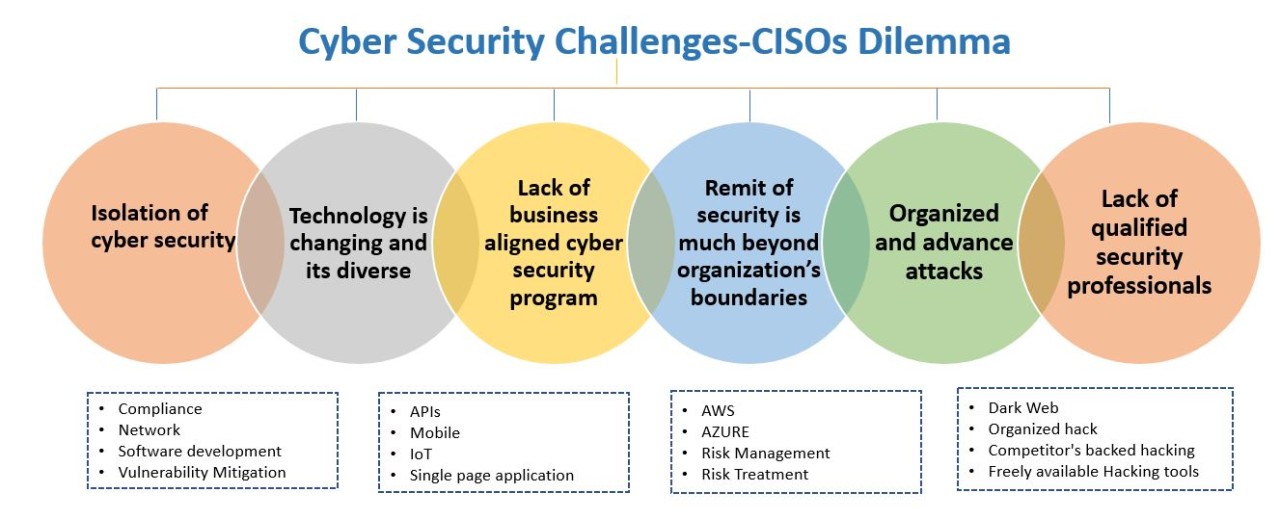
What Is Cyber Security Definition Types And Importance 58 Off Broadly speaking, ids systems fall into two categories: host based systems that are placed on a particular device, and network based systems that are placed on the network itself. ids can identify traffic that is universally indicative of malicious or otherwise suspicious activity, such as phishing, as well as browser specific attacks. Users will find that use of this threat taxonomy delivers real time context on malware, phishing, botnets, trojans and other threats, enabling faster, more confident incident investigation and response. 1. cyber threat category. 2. cyber threat type. 3. individual cyber threat.
Comments are closed.