Cyber Security Minute How Does Defense In Depth Work

Cyber Defence In Depth Pdf Security Computer Security Complete this online customer service request form to address cyber technical issues, and questions regarding clinical, billing, eligibility, and reporting issues. you will need your provider agency id available to submit a request. The meaning of cyber is of, relating to, or involving computers or computer networks (such as the internet). how to use cyber in a sentence.

Cybersecurity Defense In Depth Cybersecurity is the art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information. Cyber is a prefix that denotes a relationship with information technology (it). anything relating to computing, such as the internet, falls under the cyber category. it’s worth noting cyber carries a connotation of a relationship with modern computing and technology. Cyber definition: 1. involving, using, or relating to computers, especially the internet: 2. computers, especially…. learn more. Cyber extortion can have devastating financial and reputational consequences for businesses and individuals. there are two main types of ransomware attacks: commodity based ransomware and human operated ransomware. commodity based attacks are typically automated and indiscriminate, targeting a wide range of victims using mass distributed.
Defensive In Depth Did Cybersecurity Strategy 7 Elements Cyber definition: 1. involving, using, or relating to computers, especially the internet: 2. computers, especially…. learn more. Cyber extortion can have devastating financial and reputational consequences for businesses and individuals. there are two main types of ransomware attacks: commodity based ransomware and human operated ransomware. commodity based attacks are typically automated and indiscriminate, targeting a wide range of victims using mass distributed. Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. these cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users through ransomware; or interrupting normal business processes. Cyber threats come in many forms. some are direct and brutal. others are subtle, sneaky, and hard to trace. to grasp the full scope of cybersecurity, you must first understand what you’re up against. one of the oldest and most persistent threats is malware—a portmanteau of “malicious software.” these are programs designed to damage or. Cybersecurity is “the art of protecting networks, devices, and data from unauthorized access or criminal use.” cybersecurity has become especially relevant, with attacks increasing in both frequency and severity. Cyber (not comparable) of, or having to do with, the internet; alternative spelling of cyber . 2021, charles p. pierce, “vladimir putin is a king bullshit artist,” esquire, june 17 [quoting joe biden]: i pointed out to him we have significant cyber capability and he knows it. he doesn’t know exactly what it is, but it’s significant.
Defense In Depth Cybersecurity Automation World Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. these cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users through ransomware; or interrupting normal business processes. Cyber threats come in many forms. some are direct and brutal. others are subtle, sneaky, and hard to trace. to grasp the full scope of cybersecurity, you must first understand what you’re up against. one of the oldest and most persistent threats is malware—a portmanteau of “malicious software.” these are programs designed to damage or. Cybersecurity is “the art of protecting networks, devices, and data from unauthorized access or criminal use.” cybersecurity has become especially relevant, with attacks increasing in both frequency and severity. Cyber (not comparable) of, or having to do with, the internet; alternative spelling of cyber . 2021, charles p. pierce, “vladimir putin is a king bullshit artist,” esquire, june 17 [quoting joe biden]: i pointed out to him we have significant cyber capability and he knows it. he doesn’t know exactly what it is, but it’s significant.

How Can A Defense In Depth Approach Improve Your Cybersecurity Geek911 Cybersecurity is “the art of protecting networks, devices, and data from unauthorized access or criminal use.” cybersecurity has become especially relevant, with attacks increasing in both frequency and severity. Cyber (not comparable) of, or having to do with, the internet; alternative spelling of cyber . 2021, charles p. pierce, “vladimir putin is a king bullshit artist,” esquire, june 17 [quoting joe biden]: i pointed out to him we have significant cyber capability and he knows it. he doesn’t know exactly what it is, but it’s significant.
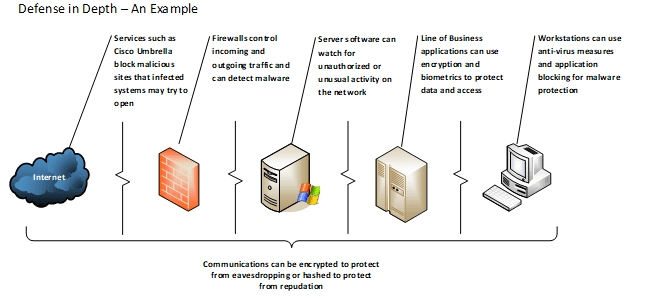
Defense In Depth
Comments are closed.