Defense In Depth Cyber Security A Multilayered Approach

Defense In Depth Multi Layered Cybersecurity Approach Learn how multi layered security, or defense in depth, protects data with overlapping physical, administrative, and technical measures. druva breaks it down. A defense in depth strategy leverages multiple security measures to protect an organization's assets. learn about the different elements and layers of the defense in depth mechanism.
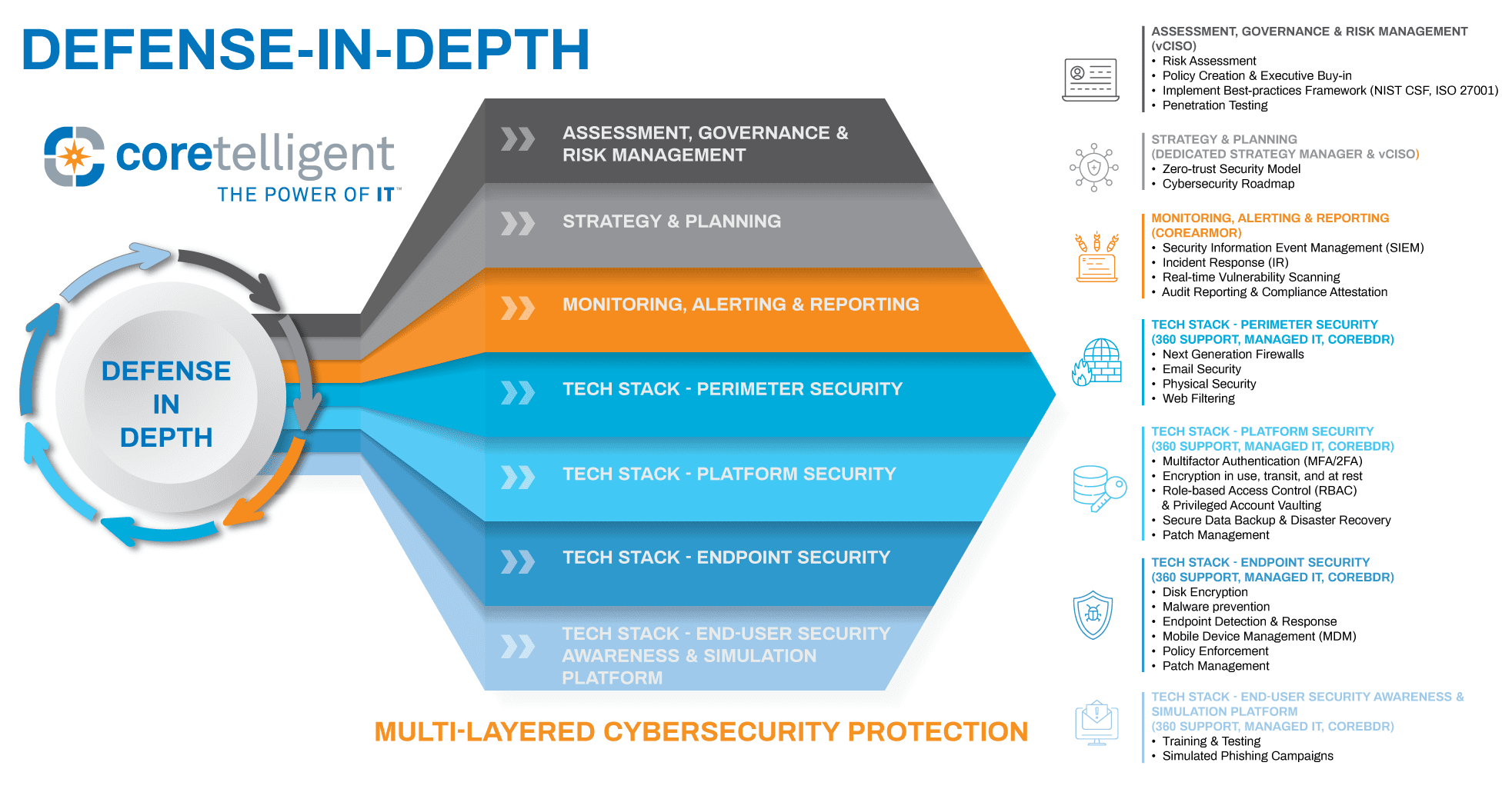
Cyber Security Solutions Coretelligent Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in tandem on the assumption that if one fails, another will hold. Similarly, defense in depth involves deploying multiple security layers, ensuring that if one fails, others remain intact. these layers span technology, processes, and people. Defence in depth is a multi layered cybersecurity strategy. it is designed to protect an organisation’s data, systems, and networks. no single security measure is perfect. Defense in depth is a layered cybersecurity strategy that offers organizations a powerful shield against ransomware and other attacks. defense in depth is a combination of detective and protective measures with the goal of reducing and mitigating the consequences of a data breach.

Cyber Security Solutions Coretelligent Defence in depth is a multi layered cybersecurity strategy. it is designed to protect an organisation’s data, systems, and networks. no single security measure is perfect. Defense in depth is a layered cybersecurity strategy that offers organizations a powerful shield against ransomware and other attacks. defense in depth is a combination of detective and protective measures with the goal of reducing and mitigating the consequences of a data breach. Download this paper and learn how to implement and evolve a defense in depth (did) strategy tailored to your organization’s risk profile, infrastructure, and cloud environment. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. a talented hacker can get through an encryption or two — but defense in depth provides multiple security barriers to prevent and deter would be attackers. Defense in depth is a cybersecurity strategy that implements multiple layers of security to protect against a wide range of threats. this concept is rooted in military defense strategies where fortifications, barriers, and checkpoints are layered to slow down and weaken attackers. Defense in depth (did) is a layered cybersecurity strategy that integrates multiple security measures to safeguard networks, applications, access, endpoints, and data. by deploying multiple defensive layers, organizations minimize risks and enhance resilience, even if one security control fails.

What Is A Defense In Depth Approach To Cybersecurity Connected Platforms Download this paper and learn how to implement and evolve a defense in depth (did) strategy tailored to your organization’s risk profile, infrastructure, and cloud environment. Defense in depth defends your network security using a layered approach to prevent cybersecurity incidents. a talented hacker can get through an encryption or two — but defense in depth provides multiple security barriers to prevent and deter would be attackers. Defense in depth is a cybersecurity strategy that implements multiple layers of security to protect against a wide range of threats. this concept is rooted in military defense strategies where fortifications, barriers, and checkpoints are layered to slow down and weaken attackers. Defense in depth (did) is a layered cybersecurity strategy that integrates multiple security measures to safeguard networks, applications, access, endpoints, and data. by deploying multiple defensive layers, organizations minimize risks and enhance resilience, even if one security control fails.
Comments are closed.