Defense In Depth Security Strategy Based On Data Encryption Cossack Labs
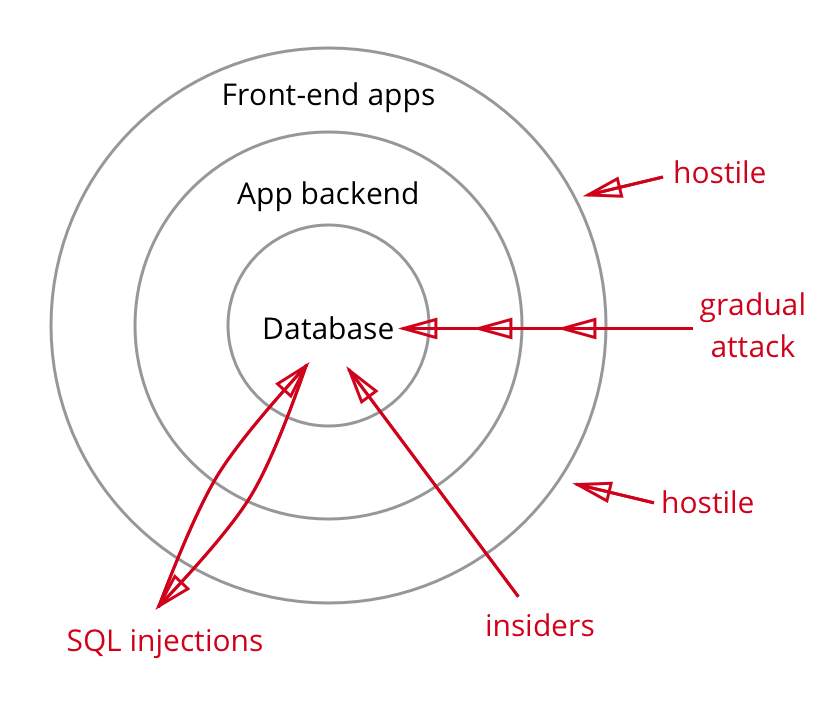
Defense In Depth Security Strategy Based On Data Encryption Cossack Labs For over six decades, Defense in Depth has been a cornerstone of security strategy Now, AI is going far beyond that — delivering intelligent, layered responses that evolve in real time with the Tom Ruff, vice president of public sector at Cambridge, Massachusetts-based content delivery network and cloud services provider Akamai Technologies (Nasdaq: AKAM), has said government agencies
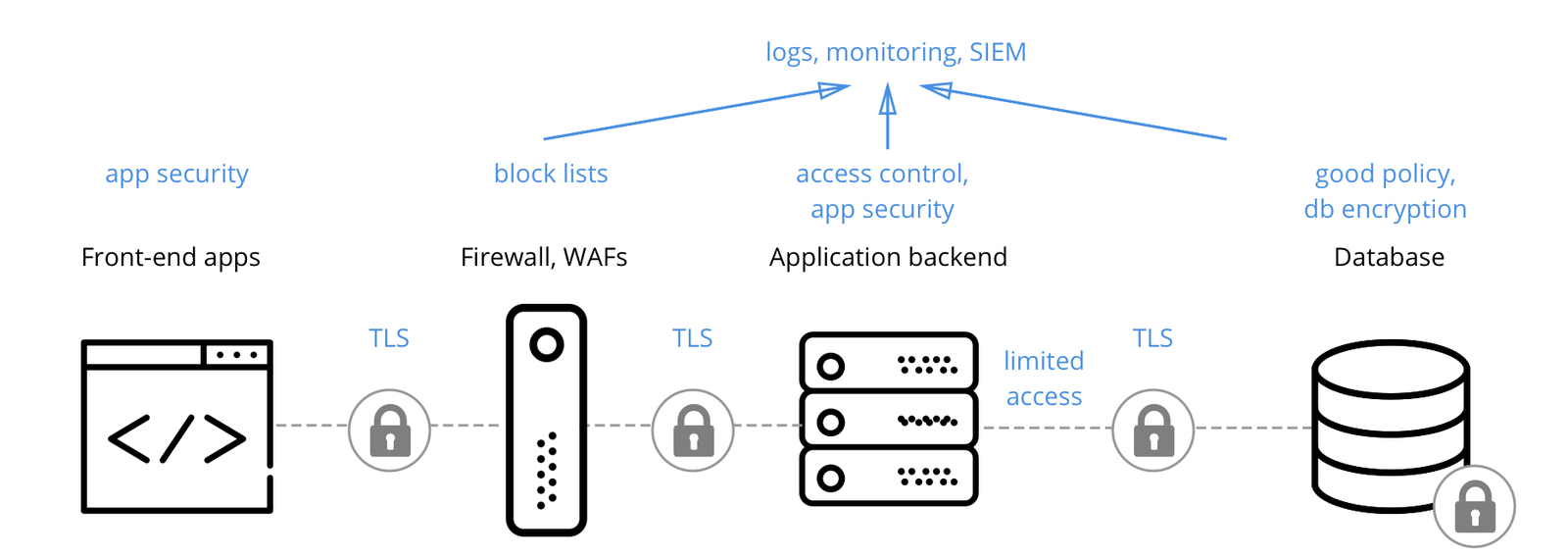
Defense In Depth Security Strategy Based On Data Encryption Cossack Labs The article discusses five cybersecurity pillars to improve data protection: risk management, AI, encryption, optimal cloud environments, and incident response
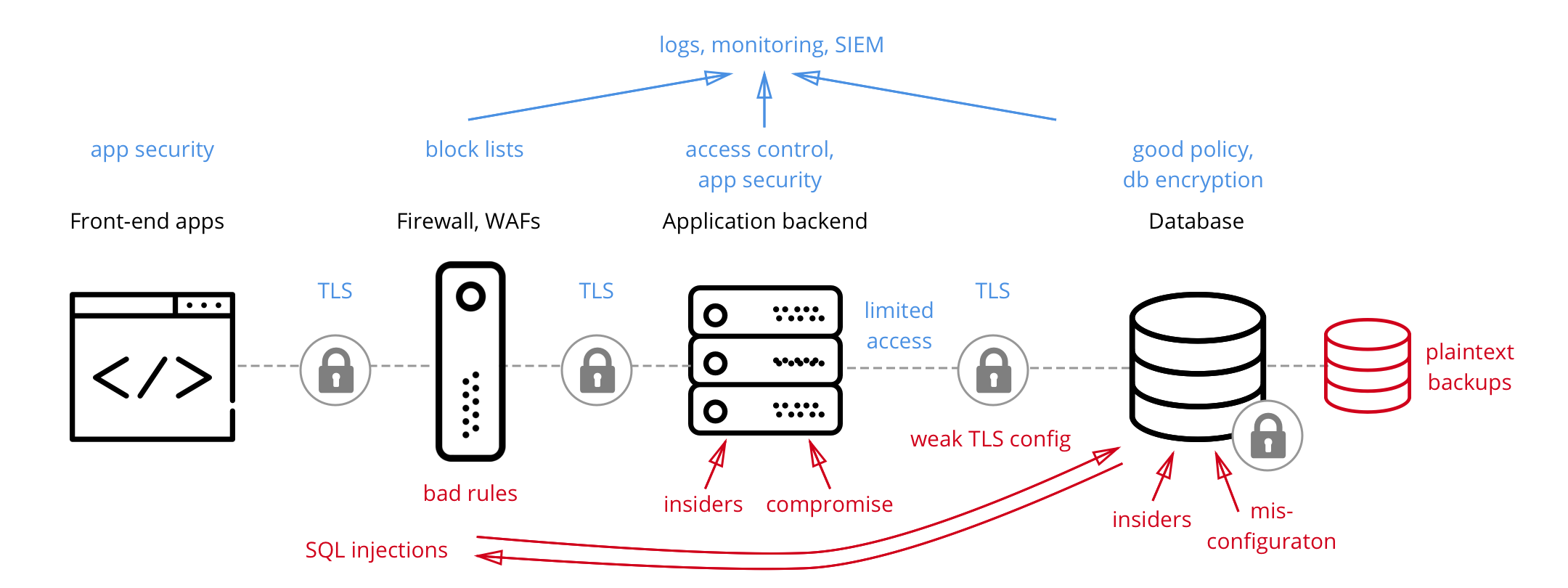
Defense In Depth Security Strategy Based On Data Encryption Cossack Labs
Comments are closed.