Electronics Free Full Text Ddos Attack Detection In Iot Based Networks Using Machine

Pdf Iot Ddos Attack Detection Using Machine Learning To identify and detect whether such attacks have occurred or not in a network, there must be a reliable mechanism of detection based on adequate techniques. the most common technique for. Ddos attack detection in iot based networks using machine learning models: a survey and research directions. electronics, 12(14), 3103. doi.org 10.3390 electronics12143103.

Pdf Ddos Attack Detection And Classification Using Machine Learning • propose three efficient ml models (rf, xgb, and mlp) for the classification of fifteen types of dos ddos attacks using the ciciot2023 dataset, which is the latest real time dataset and benchmark for large scale attacks in the iot environment. Traditional detection methods often rely on computationally intensive models, rendering them unsuitable for resource constrained iot environments. to address this limitation, this study. This study introduces a federated learning based approach, named federated learning for decentralized ddos attack detection (fl dad), which utilizes convolutional neural networks (cnn) to efficiently identify ddos attacks at the source. In this paper, three prominent datasets: unsw nb 15, unsw 2018 iot botnet and recent edge iiot are using in an anomaly based intrusion detection system (aids) to detect and mitigate ddos.

Pdf A Ddos Detection And Prevention System For Iot Devices And Its Application To Smart Home This study introduces a federated learning based approach, named federated learning for decentralized ddos attack detection (fl dad), which utilizes convolutional neural networks (cnn) to efficiently identify ddos attacks at the source. In this paper, three prominent datasets: unsw nb 15, unsw 2018 iot botnet and recent edge iiot are using in an anomaly based intrusion detection system (aids) to detect and mitigate ddos. The present survey is a comprehensive survey on the taxonomy of iot based ddos attacks, a comparative study of machine learning and deep learning methodologies used for the detection of iot based ddos attacks. Machine learning (ml) based ids have emerged as promising alternatives due to their ability to learn from data, detect unknown attack patterns, and provide high detection accuracy with minimal false alerts. The goal of this paper is to review selected studies and publications relevant to the topic of ddos detection in iot based networks using machine learning relevant publications. it offers a wealth of references for academics looking to define or expand the scope of their research in this area. Cloud computing, or fog computing, is the most convenient solution for tackling the restrictions of iot devices. this paper investigates this aspect by reviewing the related work on iot based ddos.
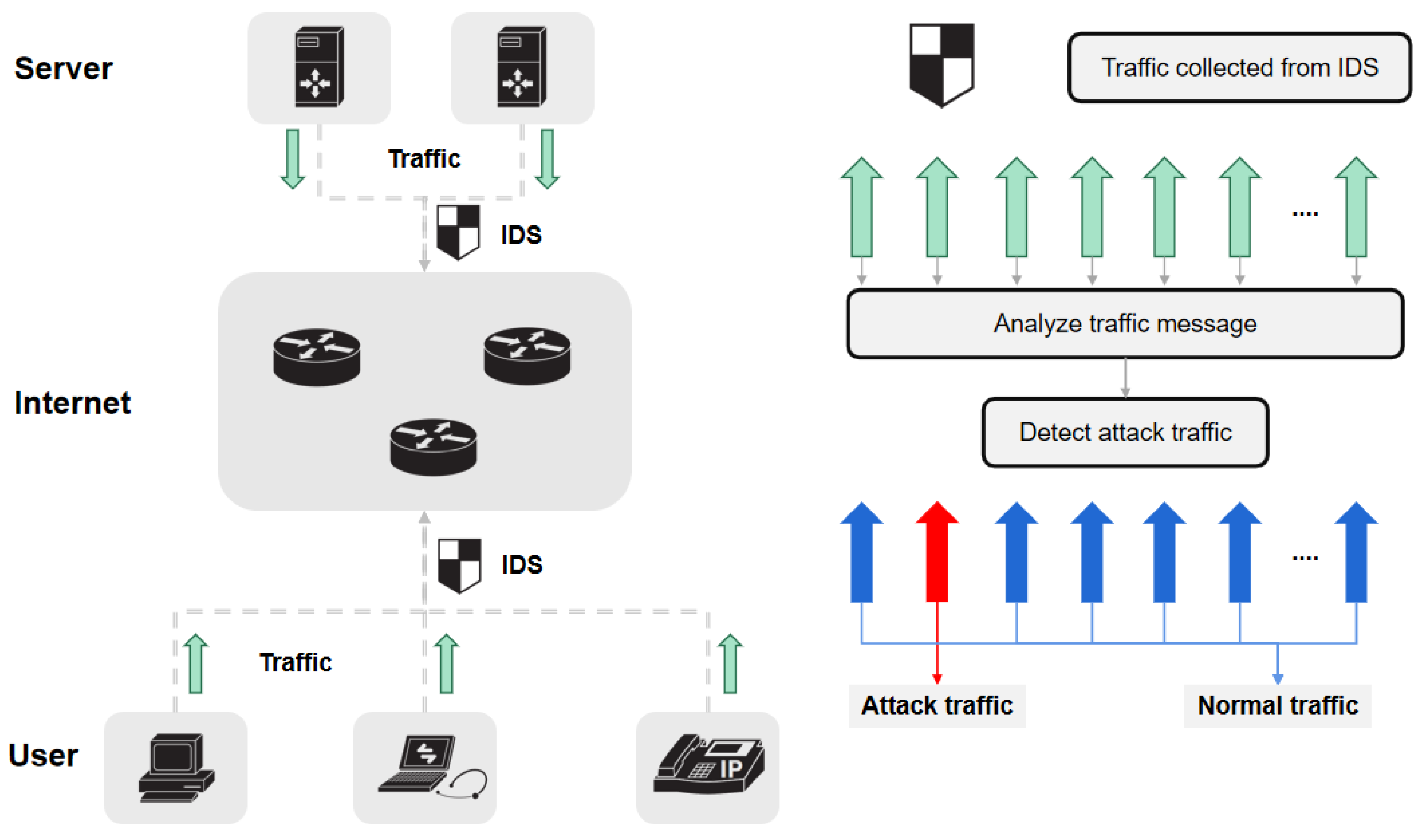
A Ddos Attack Detection Method Using Conditional Entropy Based On Sdn Traffic The present survey is a comprehensive survey on the taxonomy of iot based ddos attacks, a comparative study of machine learning and deep learning methodologies used for the detection of iot based ddos attacks. Machine learning (ml) based ids have emerged as promising alternatives due to their ability to learn from data, detect unknown attack patterns, and provide high detection accuracy with minimal false alerts. The goal of this paper is to review selected studies and publications relevant to the topic of ddos detection in iot based networks using machine learning relevant publications. it offers a wealth of references for academics looking to define or expand the scope of their research in this area. Cloud computing, or fog computing, is the most convenient solution for tackling the restrictions of iot devices. this paper investigates this aspect by reviewing the related work on iot based ddos.

Pdf A Novel Ddos Attack Detection Framework For Software Defined Iot Sd Iot Networks Using The goal of this paper is to review selected studies and publications relevant to the topic of ddos detection in iot based networks using machine learning relevant publications. it offers a wealth of references for academics looking to define or expand the scope of their research in this area. Cloud computing, or fog computing, is the most convenient solution for tackling the restrictions of iot devices. this paper investigates this aspect by reviewing the related work on iot based ddos.
Comments are closed.