Hack Blog Transmission Control Protocol Tcp

What Is Tcp Transmission Control Protocol Over the years, several vulnerabilities have been identified in the tcp ip protocol suite. some of the most notable include: ip spoofing: attackers send packets with a forged source ip address to impersonate another system. After hijacking a tcp ip session, an attacker is able to easily read and modify the transferred packets and the hacker is also able to send its own requests to the user. for tcp ip hijacking, attackers use dos attacks and ip spoofing.

What Is Transmission Control Protocol Tcp Web Hosting Geeks Blog Tcp works by transmitting data on ports, which range between 1 65,535. ports 1 1023 are standard ports (like port 80 for http falls within this category), and ports 1024 65535 are ephemeral. Master tcp ip for ethical hacking. discover its importance, essential hacking techniques, and how to protect against tcp ip attacks. Tcp ip hijacking is a type of cyber attack that exploits vulnerabilities in the transmission control protocol internet protocol (tcp ip) communication protocol to gain unauthorized access to a network. Tcp ip (transmission control protocol internet protocol) is the fundamental protocol suite used for data transmission across the internet. as an ethical hacker, you must understand how data travels between systems in order to detect, exploit, and patch vulnerabilities.
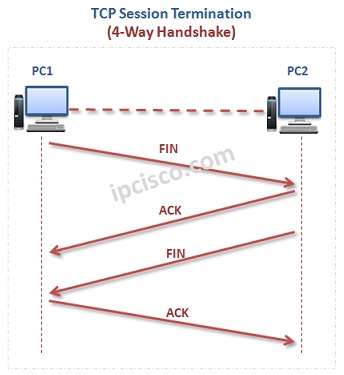
Tcp Transmission Control Protocol тлж Ipcisco Tcp ip hijacking is a type of cyber attack that exploits vulnerabilities in the transmission control protocol internet protocol (tcp ip) communication protocol to gain unauthorized access to a network. Tcp ip (transmission control protocol internet protocol) is the fundamental protocol suite used for data transmission across the internet. as an ethical hacker, you must understand how data travels between systems in order to detect, exploit, and patch vulnerabilities. It was created by vivek, the founder of the blog hack w0rm. the e book covers topics like tcp, ip, http, https, ftp, smtp, pop3, ssh, ssl, and more across 7 pages. it provides definitions, examples, and explanations of these various networking protocols and how they work together using the tcp ip model. Transmission control protocol (tcp) is amongst the most important protocols of the internet protocols suite. it is a comprehensively used protocol for the transmission of data in communication networks such as the internet. over a network, tcp is the default method of communication of data between different devices. The answer lies in two fundamental protocols that power internet communications: tcp (transmission control protocol) and udp (user datagram protocol). in this deep dive, we'll unravel these protocols, understand their differences, and learn when to use each one. A malicious party has discovered the ip address of a host inside a network she wants to hack. she employs a form of port scanning, attempting to establish a connection with the host using multiple different ports.

Free Video Tcp 12 Simple Ideas To Explain The Transmission Control Protocol From Practical It was created by vivek, the founder of the blog hack w0rm. the e book covers topics like tcp, ip, http, https, ftp, smtp, pop3, ssh, ssl, and more across 7 pages. it provides definitions, examples, and explanations of these various networking protocols and how they work together using the tcp ip model. Transmission control protocol (tcp) is amongst the most important protocols of the internet protocols suite. it is a comprehensively used protocol for the transmission of data in communication networks such as the internet. over a network, tcp is the default method of communication of data between different devices. The answer lies in two fundamental protocols that power internet communications: tcp (transmission control protocol) and udp (user datagram protocol). in this deep dive, we'll unravel these protocols, understand their differences, and learn when to use each one. A malicious party has discovered the ip address of a host inside a network she wants to hack. she employs a form of port scanning, attempting to establish a connection with the host using multiple different ports.
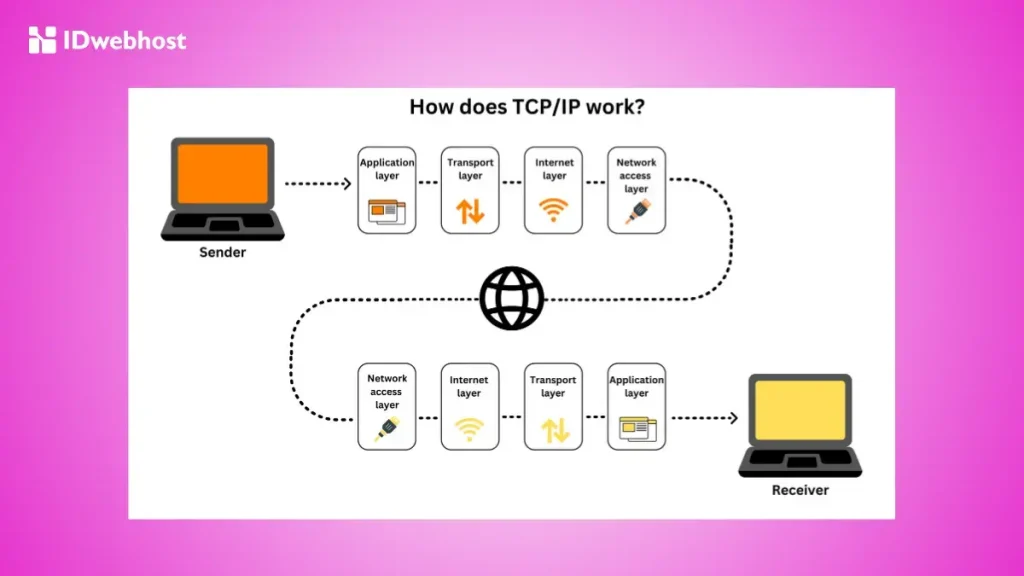
Transmission Control Protocol Tcp Fungsi Dan Cara Kerja The answer lies in two fundamental protocols that power internet communications: tcp (transmission control protocol) and udp (user datagram protocol). in this deep dive, we'll unravel these protocols, understand their differences, and learn when to use each one. A malicious party has discovered the ip address of a host inside a network she wants to hack. she employs a form of port scanning, attempting to establish a connection with the host using multiple different ports.
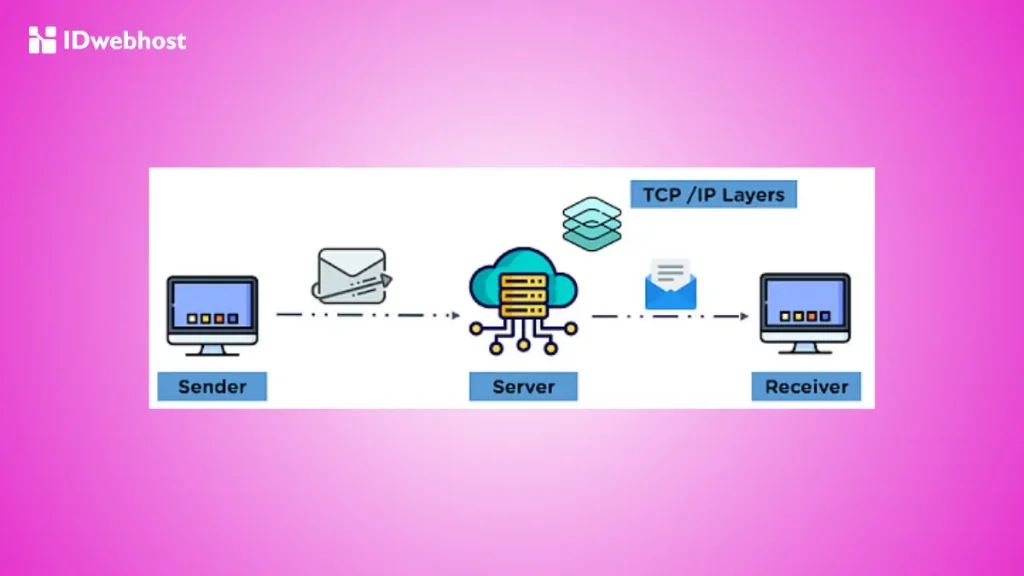
Transmission Control Protocol Tcp Fungsi Dan Cara Kerja
Comments are closed.