Hacker Demonstrates Security Risks Of Free Public Wi Fi

5 Ways Hackers Use Public Wi Fi To Steal Your Identity To begin, start typing on your keyboard and your hacker code will immediately appear! you can also enter full screen in your browser. to enhance your experience, press shift or alt (or option for mac) three times. Hackerrank is the market leading coding test and interview solution for hiring developers. start hiring at the pace of innovation!.

Public Wi Fi Security Risks Is It Safe To Use Clario Security hackers are people involved with circumvention of computer security. there are several types, including: hackers who work to keep data safe from other hackers by finding system vulnerabilities that can be mitigated. Learn to hack with our free video lessons, guides, and resources, plus join the discord community and chat with thousands of other learners. put your skills into practice with our 24x7 available capture the flag (ctf) levels inspired by real world vulnerabilities. Hacking refers to activities that seek to compromise digital devices, such as computers, smartphones, tablets, and even entire networks. Hacker, information technology professionals or enthusiasts who compromise (or “hack”) the security of computers.

The Hidden Public Wi Fi Security Risks Clario Hacking refers to activities that seek to compromise digital devices, such as computers, smartphones, tablets, and even entire networks. Hacker, information technology professionals or enthusiasts who compromise (or “hack”) the security of computers. A hacker is an individual who uses computer, networking or other skills to overcome a technical problem. the term also refers to anyone who uses such abilities to gain unauthorized access to systems or networks for illegal or unethical purposes. A hacker is a person who breaks into a computer system. the reasons for hacking can be many: installing malware, stealing or destroying data, disrupting service, and more. hacking can also be done for ethical reasons, such as trying to find software vulnerabilities so they can be fixed. What is a hacker? a hacker is someone who uses their computer, networking, or other skills to solve technical problems. the term can also refer to individuals who use their abilities to access systems or networks without permission to commit crimes. By “hacker” we mean a computer hardware, software, or programming enthusiast. a hacker likes to push boundaries, pick locks (for fun), and find ways to control hardware and make it do things that it wasn’t intended to do.

The Risks Of Using Public Wi Fi How To Stay Safe Fbi John A hacker is an individual who uses computer, networking or other skills to overcome a technical problem. the term also refers to anyone who uses such abilities to gain unauthorized access to systems or networks for illegal or unethical purposes. A hacker is a person who breaks into a computer system. the reasons for hacking can be many: installing malware, stealing or destroying data, disrupting service, and more. hacking can also be done for ethical reasons, such as trying to find software vulnerabilities so they can be fixed. What is a hacker? a hacker is someone who uses their computer, networking, or other skills to solve technical problems. the term can also refer to individuals who use their abilities to access systems or networks without permission to commit crimes. By “hacker” we mean a computer hardware, software, or programming enthusiast. a hacker likes to push boundaries, pick locks (for fun), and find ways to control hardware and make it do things that it wasn’t intended to do.
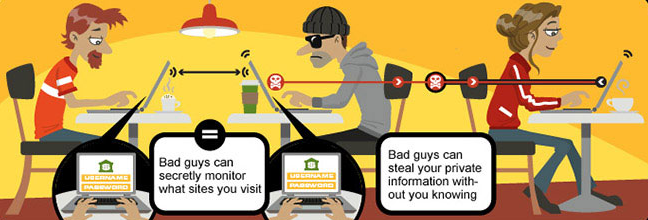
How To Protect Yourself From Risks Surrounding Public Wifi Network What is a hacker? a hacker is someone who uses their computer, networking, or other skills to solve technical problems. the term can also refer to individuals who use their abilities to access systems or networks without permission to commit crimes. By “hacker” we mean a computer hardware, software, or programming enthusiast. a hacker likes to push boundaries, pick locks (for fun), and find ways to control hardware and make it do things that it wasn’t intended to do.
Comments are closed.