How Can A Defense In Depth Approach Improve Your Cybersecurity Geek911

A Defense In Depth Approach To Government Cybersecurity A defense in depth approach is a proven strategy that involves positioning multi layer security controls to protect against a wide range of cyber threats. this approach provides overlapping layers of security, making it challenging for attackers to penetrate the network and steal data. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in tandem on the assumption that if one fails, another will hold.
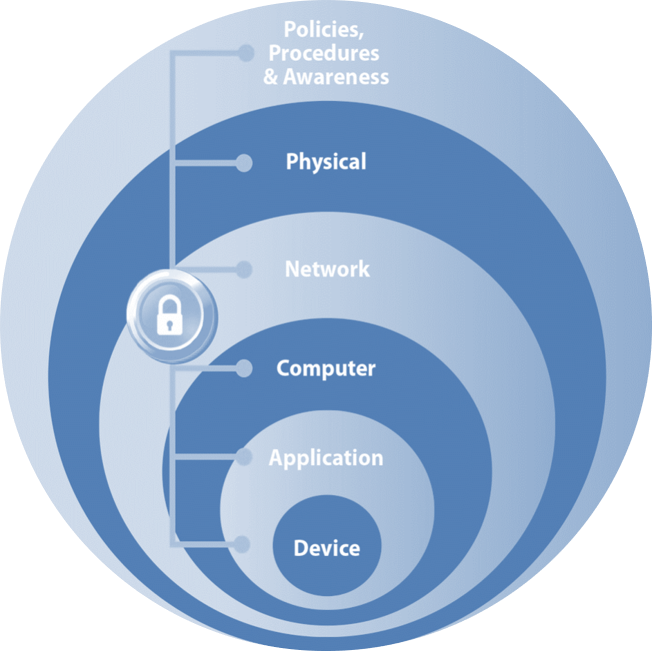
Cyber Attacks Develop A Defense In Depth Approach Polytron Different types of threats demand different approaches for detection and prevention. the defense in depth strategy rises to this challenge by deploying a range of security measures across multiple levels, including network security, endpoint protection, application security and data encryption. Defense in depth helps you accomplish your security objectives. when you employ a defense in depth strategy, you implement multiple security measures to minimize the risk of cyber threat, thereby keeping your network safe. Layered security, also known as defense in depth, is a cybersecurity strategy that uses multiple layers of protection to defend against threats at every stage of an attack. Defense in depth is a common terminology in modern day cybersecurity practices. it is a strategy that employs a series of mechanisms, also known as controls, to stop an attack on your organization.

What Is A Defense In Depth Approach To Cybersecurity Connected Platforms Layered security, also known as defense in depth, is a cybersecurity strategy that uses multiple layers of protection to defend against threats at every stage of an attack. Defense in depth is a common terminology in modern day cybersecurity practices. it is a strategy that employs a series of mechanisms, also known as controls, to stop an attack on your organization. What is defense in depth (did)? defense in depth (did) is a cybersecurity approach that utilizes multiple layers of security measures, integrating technical, administrative, and physical controls to create a robust defense framework. this strategy effectively minimizes risks to it systems and data. how has defense in depth evolved over time?. What are the main benefits of implementing defense in depth (did) in cybersecurity? the main benefits include reduced risk of data breaches and increased resilience against a variety of cyber threats. To safeguard critical assets and data, a proactive and comprehensive approach to cybersecurity is essential. one such approach is defense in depth, which involves deploying multiple layers of security controls to provide overlapping protection and minimize the potential impact of cyber attacks. Defense in depth (did) is a layered cybersecurity strategy that integrates multiple security measures to safeguard networks, applications, access, endpoints, and data. by deploying multiple defensive layers, organizations minimize risks and enhance resilience, even if one security control fails.

Defense In Depth Got Your Six Cybersecurity What is defense in depth (did)? defense in depth (did) is a cybersecurity approach that utilizes multiple layers of security measures, integrating technical, administrative, and physical controls to create a robust defense framework. this strategy effectively minimizes risks to it systems and data. how has defense in depth evolved over time?. What are the main benefits of implementing defense in depth (did) in cybersecurity? the main benefits include reduced risk of data breaches and increased resilience against a variety of cyber threats. To safeguard critical assets and data, a proactive and comprehensive approach to cybersecurity is essential. one such approach is defense in depth, which involves deploying multiple layers of security controls to provide overlapping protection and minimize the potential impact of cyber attacks. Defense in depth (did) is a layered cybersecurity strategy that integrates multiple security measures to safeguard networks, applications, access, endpoints, and data. by deploying multiple defensive layers, organizations minimize risks and enhance resilience, even if one security control fails.
Comments are closed.