How Hackers Bypass Otp To Login Register In Any Website %f0%9f%98%b1 You Need To Know This%f0%9f%ab%a3

Otp Login Page Figma Once a list of valid usernames is identified, it can be used to perform a brute force attack on the login page. this attack automates the process of testing common password combinations against each username. In this blog, we will explore various otp bypass techniques used by security researchers and ethical hackers to uncover security flaws.

How Hackers Bypass Mfa Stratejm An authentication bypass vulnerability is a weakness in a system that’s supposed to check who a user is. it allows attackers to slip past these security measures and gain unauthorized access to…. Authentication bypass vulnerabilities are among the most severe security flaws in web applications, enabling attackers to bypass login mechanisms and access sensitive systems without providing valid credentials. In this article we'll have a look at an example of tools and techniques attackers can use to bypass two factor authentication (2fa) methods, from sms otp code to encrypted push notifications to a mobile app. These techniques exploit vulnerabilities in the login mechanism, such as weak or default passwords, insecure password recovery mechanisms, and insecure application logic. here is a simple example of a login bypass technique: sql injection in login form. username: admin' password: any.

How Hackers Bypass Mfa Stratejm In this article we'll have a look at an example of tools and techniques attackers can use to bypass two factor authentication (2fa) methods, from sms otp code to encrypted push notifications to a mobile app. These techniques exploit vulnerabilities in the login mechanism, such as weak or default passwords, insecure password recovery mechanisms, and insecure application logic. here is a simple example of a login bypass technique: sql injection in login form. username: admin' password: any. But, there are several ways one can bypass this otp authentication as well and eventually cause damage to your account. if you are thinking how it can be done, then here we are going to look into it in detail to help you with complete clarity. read on. Hackers have devised several tactics to bypass otp and 2fa mechanisms, allowing them to access accounts with ease. understanding these methods can help users and organizations strengthen their defenses against these sophisticated attacks. Hackers can bypass mfa in much the same way as they would for two factor authentication, where there is just a username and password. below are some of the most common ways that mfa can be bypassed: social engineering techniques, such as phishing, is a common way for attackers to obtain credentials. In an otp bypass attack, cybercriminals exploit vulnerabilities in a web application or communication channel to intercept the otp code sent to the victim's phone number.
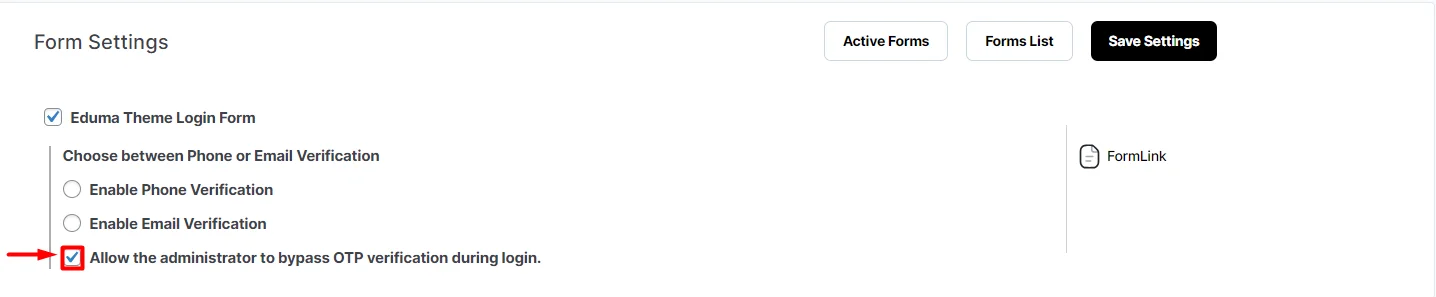
Otp Verification For Eduma Theme Login Form Wordpress But, there are several ways one can bypass this otp authentication as well and eventually cause damage to your account. if you are thinking how it can be done, then here we are going to look into it in detail to help you with complete clarity. read on. Hackers have devised several tactics to bypass otp and 2fa mechanisms, allowing them to access accounts with ease. understanding these methods can help users and organizations strengthen their defenses against these sophisticated attacks. Hackers can bypass mfa in much the same way as they would for two factor authentication, where there is just a username and password. below are some of the most common ways that mfa can be bypassed: social engineering techniques, such as phishing, is a common way for attackers to obtain credentials. In an otp bypass attack, cybercriminals exploit vulnerabilities in a web application or communication channel to intercept the otp code sent to the victim's phone number.
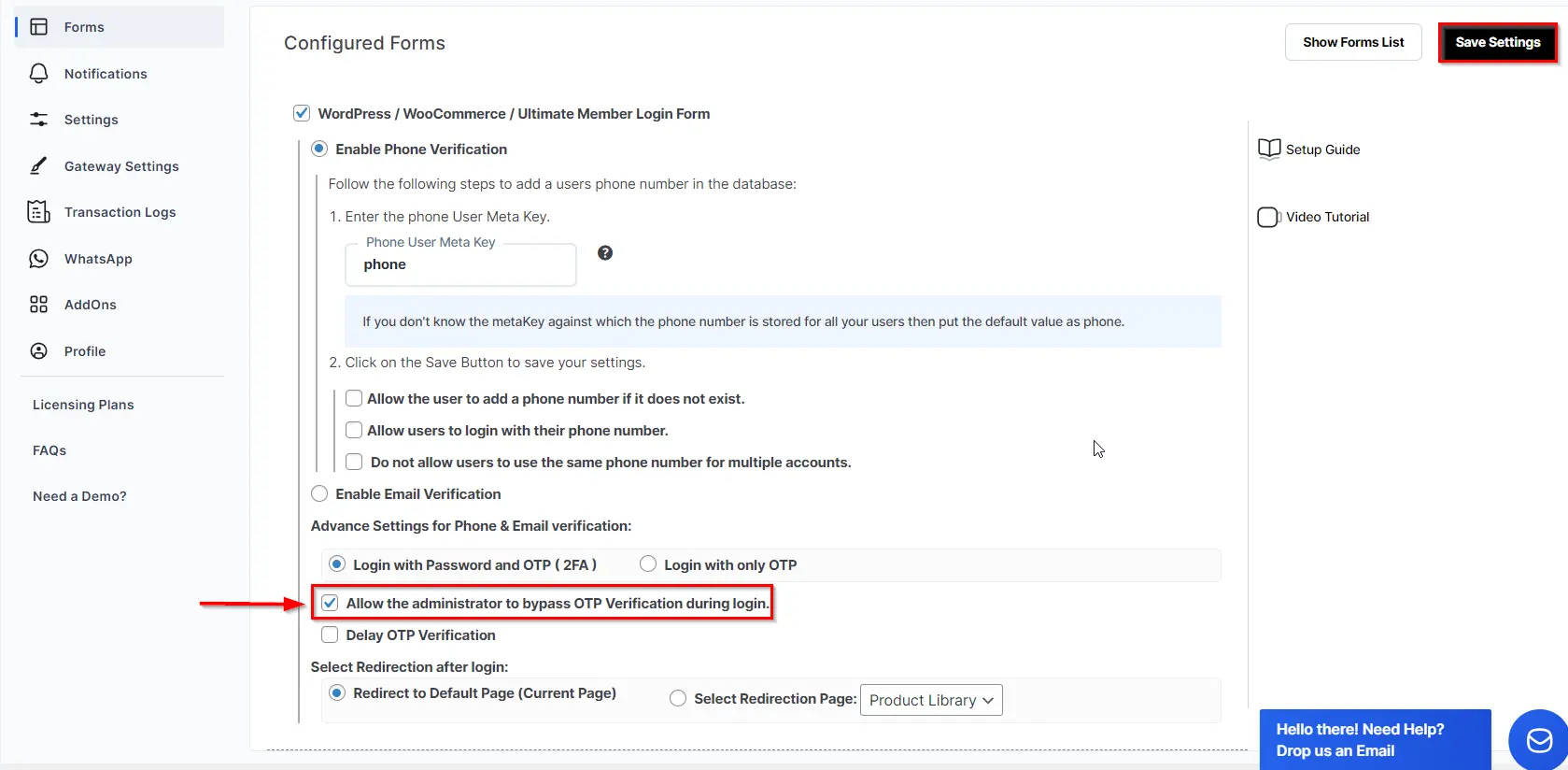
Guide For Wordpress Default Login Forms With Otp Verification Hackers can bypass mfa in much the same way as they would for two factor authentication, where there is just a username and password. below are some of the most common ways that mfa can be bypassed: social engineering techniques, such as phishing, is a common way for attackers to obtain credentials. In an otp bypass attack, cybercriminals exploit vulnerabilities in a web application or communication channel to intercept the otp code sent to the victim's phone number.
Comments are closed.