How To Leverage Email Authentication Solutions Spf Dkim And Dmarc To Stop Email Spoofing
Spf Dkim Dmarc How Email Authentication Works 46 Off Ultimately, spf, dkim, and dmarc can work together to help you catapult your organization’s email security to new heights, and stop attackers from spoofing your domain name to safeguard your organization’s reputation and credibility. Admins can learn how email authentication (spf, dkim, dmarc) works and how microsoft 365 uses traditional email authentication and composite email authentication to allow and block spoofed messages.
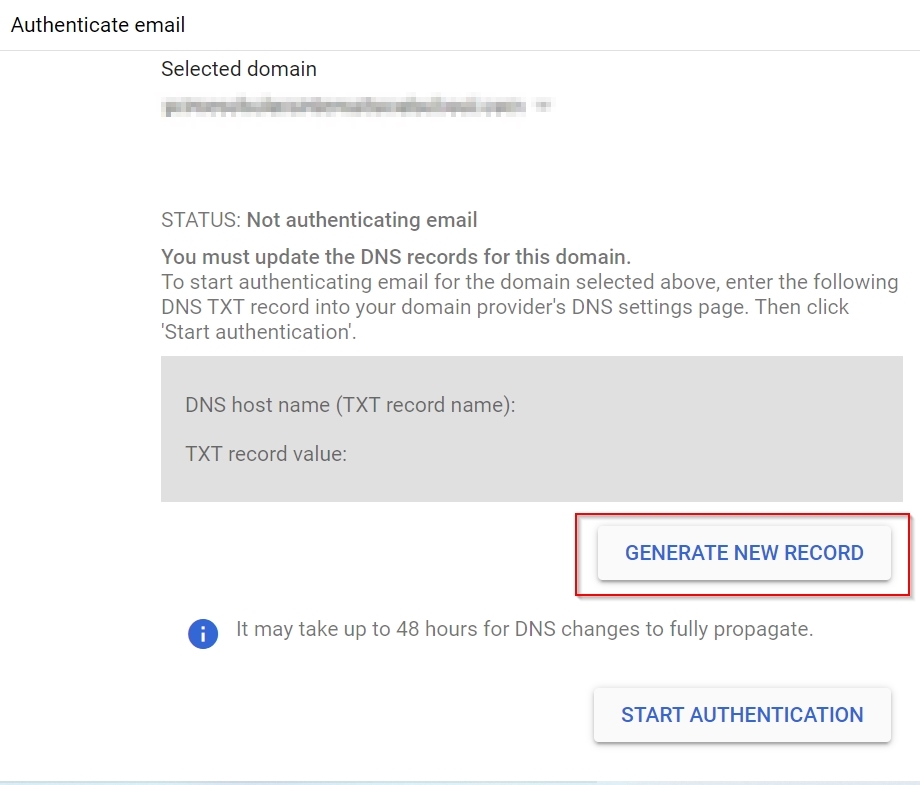
How To Leverage Email Authentication Solutions Spf Dkim And Dmarc To Stop Email Spoofing Email authentication is paramount for businesses running bulk email marketing campaigns for customer communication and transactional messages. without spf, dkim, and dmarc policies, your domain is vulnerable to spoofing attacks, which pose a major threat to email security and sender reputation. Learn how to implement spf, dkim, and dmarc to safeguard your business emails. have you ever wondered what happens to your business emails after you hit "send"? making sure your emails reach your customers — and that they can trust those emails really came from you — isn't as simple as it used to be. To counter these threats, organizations must implement robust email authentication protocols that verify sender legitimacy and protect their domains from misuse. the three pillars of modern email security spf, dkim, and dmarc work together to provide a layered defense against spoofing and unauthorized email delivery. In this post, we will take a deeper dive into how organizations can help stop email spoofing using a combination of three (3) essential tools: sender policy framework (spf), domainkeys identified mail (dkim), and domain based message authentication, reporting and conformance (dmarc).

Dmarc Dkim Spf Email Authentication Diversified Computer Resources To counter these threats, organizations must implement robust email authentication protocols that verify sender legitimacy and protect their domains from misuse. the three pillars of modern email security spf, dkim, and dmarc work together to provide a layered defense against spoofing and unauthorized email delivery. In this post, we will take a deeper dive into how organizations can help stop email spoofing using a combination of three (3) essential tools: sender policy framework (spf), domainkeys identified mail (dkim), and domain based message authentication, reporting and conformance (dmarc). In other words, to prevent email spoofing, it's strongly advised to set up dkim, spf, and dmarc. in this article, we'll go through how these email authentication methods work, using real life examples and digging into email headers. Setting up spf, dkim, and dmarc correctly is your first line of defense against email spoofing and domain impersonation attacks. this guide will explain how these three key technologies work together to verify sender identity and secure your email communications. If you’re struggling with email deliverability issues and want to protect your domain from email spoofing and phishing attacks, implementing proper email authentication protocols is crucial for your success. By implementing spf, dkim, and dmarc together, you protect your domain from spoofing and phishing attacks, enhance your sender reputation, and improve email deliverability.

What Are Dmarc Dkim And Spf In other words, to prevent email spoofing, it's strongly advised to set up dkim, spf, and dmarc. in this article, we'll go through how these email authentication methods work, using real life examples and digging into email headers. Setting up spf, dkim, and dmarc correctly is your first line of defense against email spoofing and domain impersonation attacks. this guide will explain how these three key technologies work together to verify sender identity and secure your email communications. If you’re struggling with email deliverability issues and want to protect your domain from email spoofing and phishing attacks, implementing proper email authentication protocols is crucial for your success. By implementing spf, dkim, and dmarc together, you protect your domain from spoofing and phishing attacks, enhance your sender reputation, and improve email deliverability.

Dmarc Dkim Spf Email Authentication Best Practices Easydmarc If you’re struggling with email deliverability issues and want to protect your domain from email spoofing and phishing attacks, implementing proper email authentication protocols is crucial for your success. By implementing spf, dkim, and dmarc together, you protect your domain from spoofing and phishing attacks, enhance your sender reputation, and improve email deliverability.
Comments are closed.