How To Protect Your Data From Unauthorized Access By Neuralstrikes Inc Issuu

How To Protect Your Data From Unauthorized Access By Neuralstrikes Inc Issuu Protecting data from unauthorized access is essential to safeguard sensitive information and maintain the privacy and security of individuals, organizations, and institutions. We secure your cloud environments with advanced protection against breaches, misconfigurations, and unauthorized access. our solutions ensure data integrity, compliance, and safe cloud operations around the clock.

How To Protect Your Data From Unauthorized Access By Neuralstrikes Inc Issuu Is your data secure? read on to discover how your organization can prevent hackers from gaining unauthorized data access to disrupt your business operations. Protect your data with strong passwords, mfa, and network monitoring. learn key strategies to safeguard against unauthorized access!. Therefore, it’s critical for organizations to establish a robust cybersecurity strategy and implement best practices to effectively detect and respond to unauthorized access. in this article, we explore the dangers behind unauthorized access and its key attack vectors. In this article, you will learn some practical tips on how to secure your data from unauthorized access using problem solving skills. selected by the community from 7 contributions .

How To Protect Your Data From Unauthorized Access By Neuralstrikes Inc Issuu Therefore, it’s critical for organizations to establish a robust cybersecurity strategy and implement best practices to effectively detect and respond to unauthorized access. in this article, we explore the dangers behind unauthorized access and its key attack vectors. In this article, you will learn some practical tips on how to secure your data from unauthorized access using problem solving skills. selected by the community from 7 contributions . Secure your cloud environments with advanced tools to monitor, encrypt, and protect data from unauthorized access. solutions should include identity based access controls, activity tracking, and real time threat prevention. Unauthorized access to sensitive documents poses significant risks to organizations, including data theft, operational disruptions, and compliance issues. with increasing sophistication in cyber threats, it is essential to adopt effective strategies to fortify your document security. From mfa to edr, these 6 security controls help close access gaps and reduce exposure to real world attack scenarios. Learn how to prevent unauthorized access with our guide. secure your business's sensitive data with easy to follow strategies for enhanced data protection.
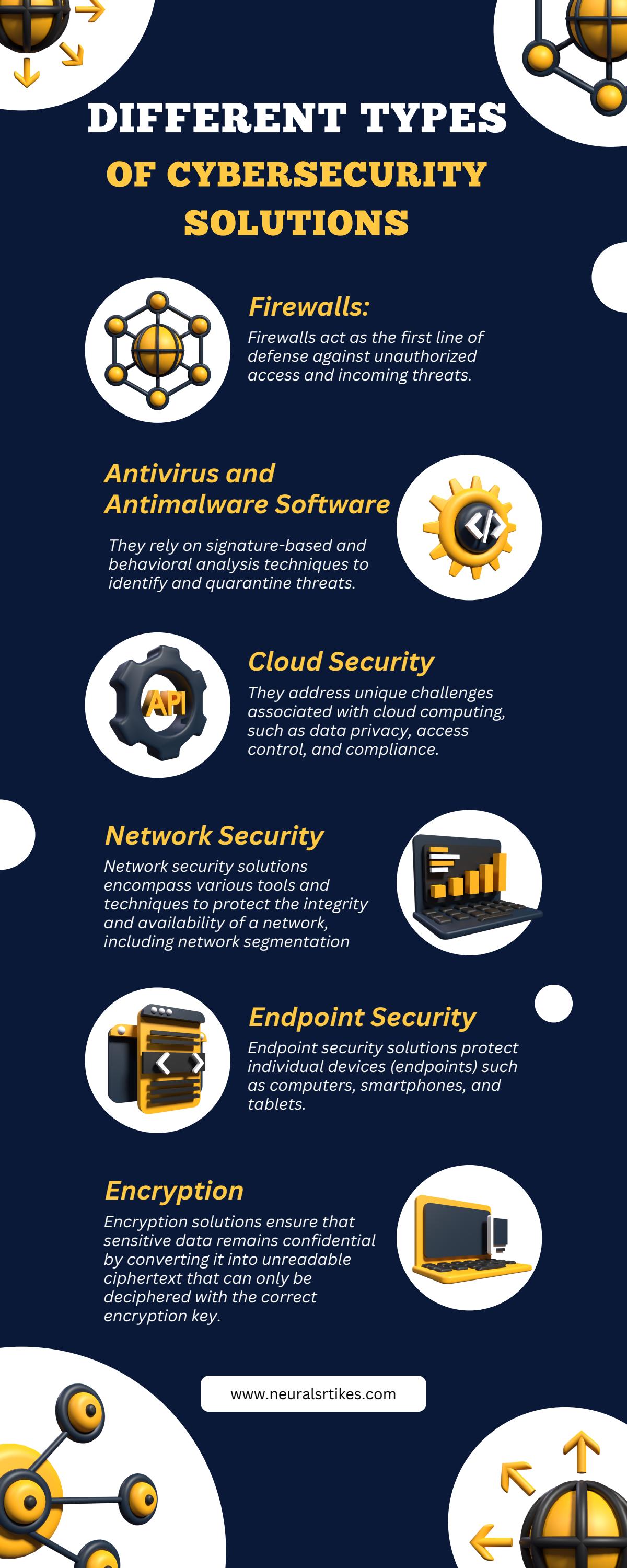
Various Types Of Cybersecurity Solutions By Neuralstrikes Inc Issuu Secure your cloud environments with advanced tools to monitor, encrypt, and protect data from unauthorized access. solutions should include identity based access controls, activity tracking, and real time threat prevention. Unauthorized access to sensitive documents poses significant risks to organizations, including data theft, operational disruptions, and compliance issues. with increasing sophistication in cyber threats, it is essential to adopt effective strategies to fortify your document security. From mfa to edr, these 6 security controls help close access gaps and reduce exposure to real world attack scenarios. Learn how to prevent unauthorized access with our guide. secure your business's sensitive data with easy to follow strategies for enhanced data protection.
Comments are closed.