How To S Deploy Check Point Identity Awareness Check Point Checkmates

Check Point Identity Awareness Datasheet Pdf Hi there, in this post we’re going to deploy check point identity awareness. first of all, we’re going to integrate our active directory (ldap ad) with check point security solution (cp). This section describes how to configure and work with identity awareness check point software blade on a security gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer.
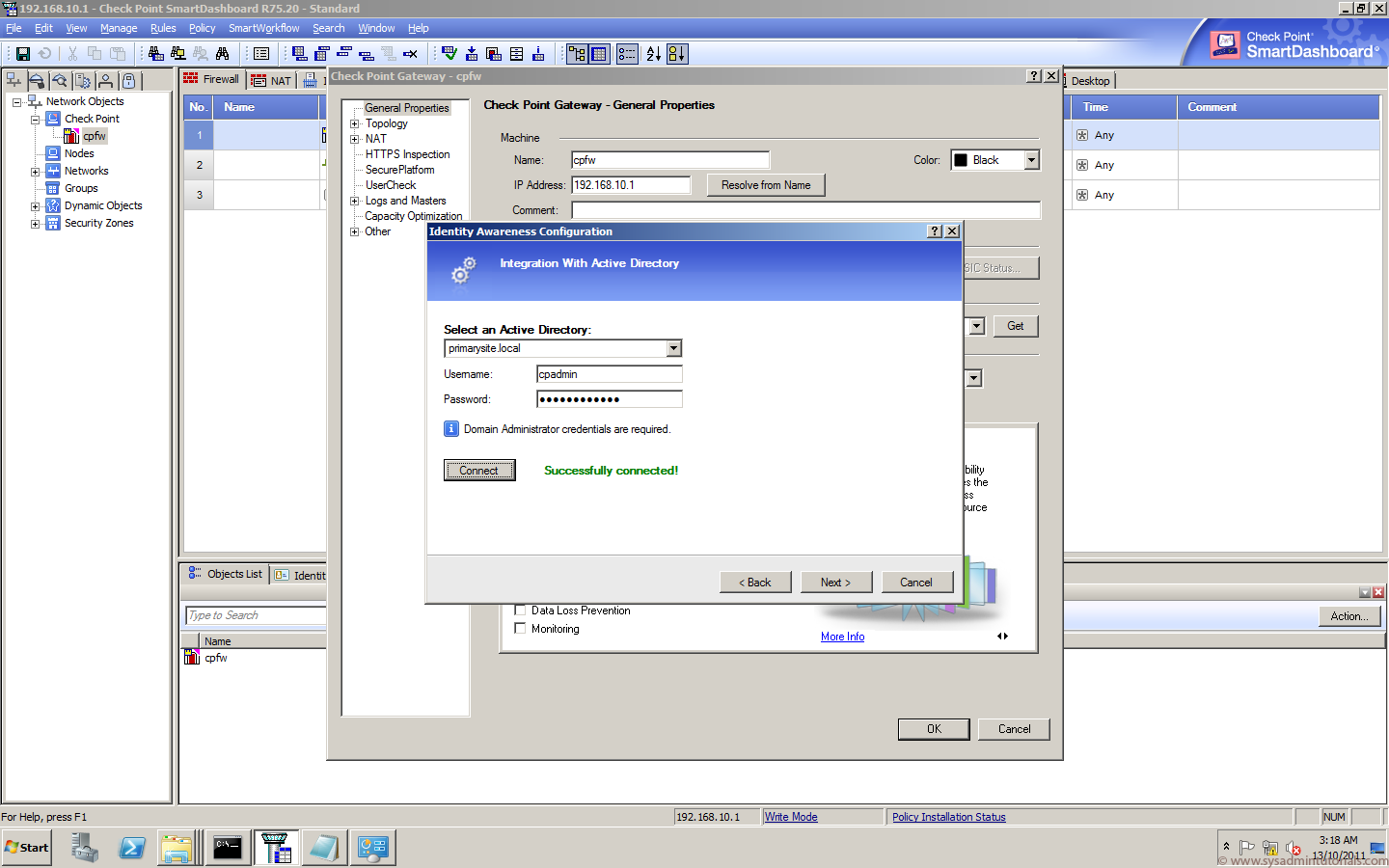
Check Point R75 Identity Awareness Setup How to install and configure active directory and domain name system (dns) for ia in check point. in this playlist, we will cover identity awareness (ia) in check point from the. Identity awareness is integrated into the check point infinity architecture. it can be easily and rapidly deployed on existing check point security gateways to seamlessly integrate with multiple identity sources. Identity awareness maps users and computer identities to ip addresses, allowing you to enforce access and audit data based on identity. ia is an easy to deploy and scalable solution. Identity awareness is an easy to deploy and scalable solution. it works for both active directory and non active directory based networks, and also for employees and guest users. identity awareness uses the source and destination ip addresses of network traffic to identify users and computers.

Check Point R75 Identity Awareness Setup Identity awareness maps users and computer identities to ip addresses, allowing you to enforce access and audit data based on identity. ia is an easy to deploy and scalable solution. Identity awareness is an easy to deploy and scalable solution. it works for both active directory and non active directory based networks, and also for employees and guest users. identity awareness uses the source and destination ip addresses of network traffic to identify users and computers. One of the features that will help us meet this goal, is identity awareness. if you would like to learn how to enable it, read my previous post how “to's deploy check point identity awareness”. Deploy check point security gateways with enabled identity awareness software blade for better security for your network environment and corporate data. this section describes recommended deployments with identity awareness. I would like to share my experience with checkpoint identity awareness (ia) in a large scale deployment over the last two years. the burning ship: since i joined this company it is using ia for many diffrent use cases. Thanks to @royi priov and team, we now have a new guide that consolidates information on the various identity awareness clients into a single guide. this includes identity collector, identity agent, and the multi user host agents.

Check Point R75 Identity Awareness Setup One of the features that will help us meet this goal, is identity awareness. if you would like to learn how to enable it, read my previous post how “to's deploy check point identity awareness”. Deploy check point security gateways with enabled identity awareness software blade for better security for your network environment and corporate data. this section describes recommended deployments with identity awareness. I would like to share my experience with checkpoint identity awareness (ia) in a large scale deployment over the last two years. the burning ship: since i joined this company it is using ia for many diffrent use cases. Thanks to @royi priov and team, we now have a new guide that consolidates information on the various identity awareness clients into a single guide. this includes identity collector, identity agent, and the multi user host agents.

Check Point R75 Identity Awareness Setup I would like to share my experience with checkpoint identity awareness (ia) in a large scale deployment over the last two years. the burning ship: since i joined this company it is using ia for many diffrent use cases. Thanks to @royi priov and team, we now have a new guide that consolidates information on the various identity awareness clients into a single guide. this includes identity collector, identity agent, and the multi user host agents.

Check Point R75 Identity Awareness Setup
Comments are closed.