How To Secure Your Tcp Ip Ports Techradar
How To Secure Your Tcp Ip Ports Techradar Close them off: closing the ports you don't need is a good place to start on the road to a secure pc. the tcp ip system running on the internet today uses a series of handshakes to ensure. Learn how to secure your open ports on your computer or network and protect yourself from cyber attacks.
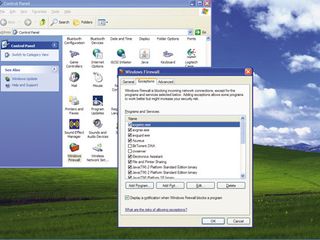
How To Secure Your Tcp Ip Ports Techradar To secure tcp ip networks against cyber threats, it’s essential to understand the common types of attacks they face. cyber threats to tcp ip networks include malware, phishing attacks, distributed denial of service (ddos) attacks, and man in the middle attacks. In the transport layer of the tcp ip model, we have two types of protocols: tcp and udp. both are constantly used by different application layer programs and protocols, such as port 80 and 443 for browsing the web, port 22 for the ssh protocol, or the popular port 1194 for openvpn vpns. Both tcp and udp use the ip protocol to address and route data on the internet. ports can be open, closed, or filtered depending on their ability to respond to connection requests. this article will focus on the vulnerabilities that come with open ports, as well as tips to help secure them. Opening network ports can be risky, but with the right security measures in place, you can minimize the vulnerabilities and protect your network from unauthorized access and attacks.
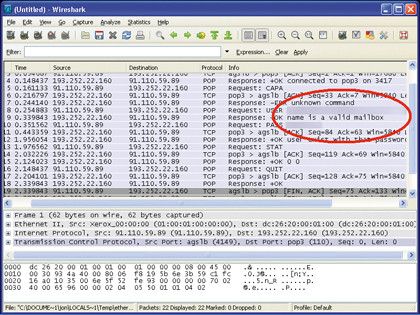
Tcp Ip S Vulnerabilities How To Secure Your Tcp Ip Ports Page 2 Techradar Both tcp and udp use the ip protocol to address and route data on the internet. ports can be open, closed, or filtered depending on their ability to respond to connection requests. this article will focus on the vulnerabilities that come with open ports, as well as tips to help secure them. Opening network ports can be risky, but with the right security measures in place, you can minimize the vulnerabilities and protect your network from unauthorized access and attacks. Learn how to secure your tcp connections and protect your network from attacks with encryption, firewalls, authentication, patches and updates, and monitoring and auditing. Limiting your attack surface by only having what you need running, and only having things listening on interfaces and ports you need, is the first and best thing. other common options include. Let's look at some of the important points to secure open ports. At the same time, many businesses are not adequately protected, with some not taking the most basic steps to secure their networks from the inside. but protecting yourself is as easy as.

Tcp Ip Ports And Protocols Learn how to secure your tcp connections and protect your network from attacks with encryption, firewalls, authentication, patches and updates, and monitoring and auditing. Limiting your attack surface by only having what you need running, and only having things listening on interfaces and ports you need, is the first and best thing. other common options include. Let's look at some of the important points to secure open ports. At the same time, many businesses are not adequately protected, with some not taking the most basic steps to secure their networks from the inside. but protecting yourself is as easy as.
Comments are closed.