Ipsec Encryption Aes 256 Virtual Private Network Gateway Telecommunications

Configuring Ipsec Virtual Private Networks Pdf Virtual Private Network Cryptography The recent nsa publication “securing ipsec virtual private networks” [1] lays out the importance of ip security (ipsec) virtual private networks (vpns) and outlines specific recommendations for securing those connections. Create the virtual networks, vpn gateways, or local network gateways for your connectivity topology as described in other how to documents. create an ipsec ike policy. you can apply the policy when you create a s2s or vnet to vnet connection.

Ikev2 Ipsec Virtual Private Networks Pdf Radius Virtual Private Network The it department of a company has just rolled out a virtual private network (vpn) solution that offers greater flexibility, delegation of management, and added security over the previous implementation. Per cnssp 15, as of june 2020, minimum recommended settings for isakmp ike are diffie hellman group 16, aes 256 encryption, and sha 384 hash, while those for ipsec are aes 256 encryption, sha 384 hash, and cbc block cipher mode. Ikev2 is supported in pan os 7.1.4 and newer versions, and fully supports the necessary route based vpn and crypto profiles to connect to ms azure’s dynamic vpn architecture. this document discusses the basic configuration on a palo alto networks firewall for the same. Internet protocol security (ipsec) is a suite of open standards for ensuring private communications over public networks. it is the most common network layer security control, typically used to encrypt internet protocol (ip) traffic between hosts in a network and to create a virtual private network (vpn).

Ipsec Vpn Pdf Virtual Private Network Gateway Telecommunications Ikev2 is supported in pan os 7.1.4 and newer versions, and fully supports the necessary route based vpn and crypto profiles to connect to ms azure’s dynamic vpn architecture. this document discusses the basic configuration on a palo alto networks firewall for the same. Internet protocol security (ipsec) is a suite of open standards for ensuring private communications over public networks. it is the most common network layer security control, typically used to encrypt internet protocol (ip) traffic between hosts in a network and to create a virtual private network (vpn). The ipsec vpn virtual private network connections on this sophos utm always use the tunnel mode. in transport mode, the original ip packet is not encapsulated in another packet. the original ip header is retained, and the rest of the packet is sent either in clear text (ah) or encrypted (esp). Isakmp and ipsec accomplish the following: the asa functions as a bidirectional tunnel endpoint. it can receive plain packets from the private network, encapsulate them, create a tunnel, and send them to the other end of the tunnel where they are unencapsulated and sent to their final destination. When working with default policies, azure can act as both initiator and responder during an ipsec tunnel setup. while virtual wan vpn supports many algorithm combinations, our recommendation is gcmaes256 for both ipsec encryption and integrity for optimal performance. Ipsec vpn gateway products used in commercial solutions for classified (csfc) solutions (as defined in the csfc capability packages (cps)) shall be validated by national information assurance partnership.

Ipsec Encryption Aes 256 Virtual Private Network Gateway Telecommunications The ipsec vpn virtual private network connections on this sophos utm always use the tunnel mode. in transport mode, the original ip packet is not encapsulated in another packet. the original ip header is retained, and the rest of the packet is sent either in clear text (ah) or encrypted (esp). Isakmp and ipsec accomplish the following: the asa functions as a bidirectional tunnel endpoint. it can receive plain packets from the private network, encapsulate them, create a tunnel, and send them to the other end of the tunnel where they are unencapsulated and sent to their final destination. When working with default policies, azure can act as both initiator and responder during an ipsec tunnel setup. while virtual wan vpn supports many algorithm combinations, our recommendation is gcmaes256 for both ipsec encryption and integrity for optimal performance. Ipsec vpn gateway products used in commercial solutions for classified (csfc) solutions (as defined in the csfc capability packages (cps)) shall be validated by national information assurance partnership.
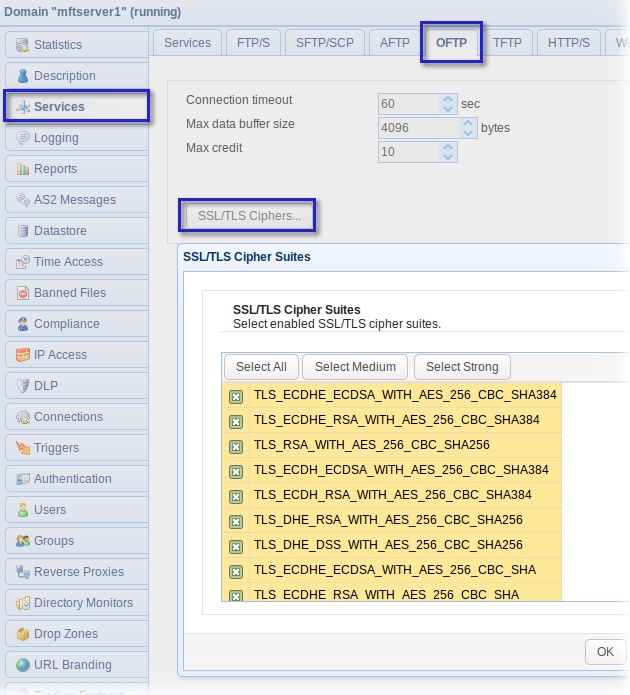
Choosing Ssl Tls With Aes 256 Cipher Suites For Oftp When working with default policies, azure can act as both initiator and responder during an ipsec tunnel setup. while virtual wan vpn supports many algorithm combinations, our recommendation is gcmaes256 for both ipsec encryption and integrity for optimal performance. Ipsec vpn gateway products used in commercial solutions for classified (csfc) solutions (as defined in the csfc capability packages (cps)) shall be validated by national information assurance partnership.
Virtual Private Network Tunneling Protocol Computer Security Encryption Ipsec Png 725x348px
Comments are closed.