Lab 4 Performing A Vulnerability Assessment Docx Lab 4 Performing A Vulnerability Assessment

Lab 7 Vulnerability Assessment Nessus Pdf Lab 4 vulnerability analysis free download as word doc (.doc .docx), pdf file (.pdf), text file (.txt) or read online for free. the document describes how to perform vulnerability research using vulnerability scoring systems and databases. For each vulnerability, identify the severity, describe the issue, and recommend a remediation. the recent penetration test uncovered several critical vulnerabilities that pose significant risks to the security of the client’s systems.
Solved Lab 2 Assessment Worksheet Performing A Vulnerability Assessment 5 Can Zenmap Detect Study with quizlet and memorize flashcards containing terms like default passwords used on admin accounts, unused user accounts still enabled, misconfigured firewall settings and more. Information systems document from post university, 2 pages, lab 4 assessment worksheet using ethical hacking techniques to exploit a vulnerable workstation course name and number: issc262: red and blue team security student name: beverly b. baxter instructor name: dr. amir alipour fanid lab due date: april 14,. Performing a vulnerability assessment (4e)fundamentals of information systems security, fourth edition lab 02 your solution’s ready to go! enhanced with ai, our expert help has broken down your problem into an easy to learn solution you can count on. Performing a vulnerability assessment (4e) fundamentals of information systems security, fourth edition lab 02 in this part of the lab, you will use nessus to continue your vulnerability assessment of the secure labs on demand office lan.
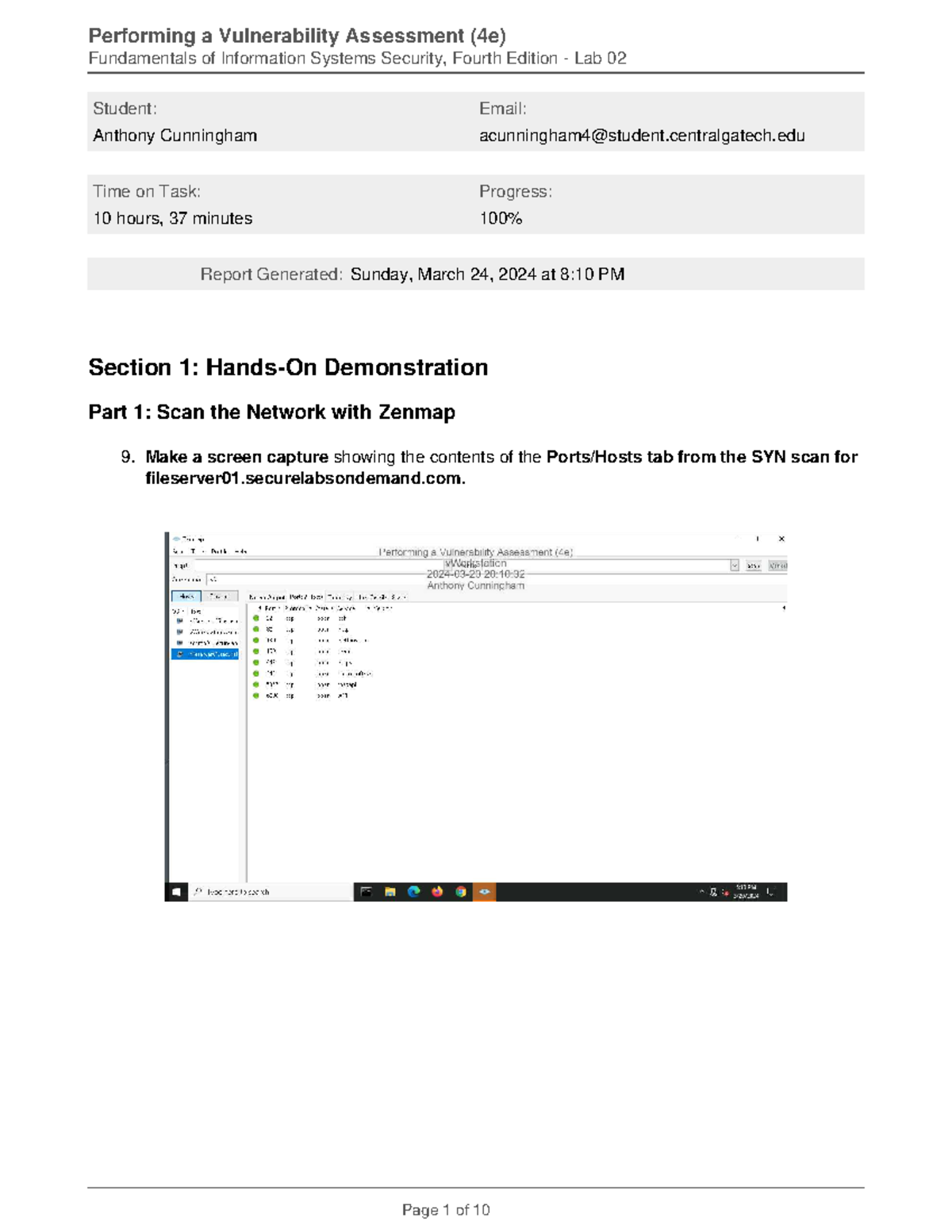
Performing A Vulnerability Assessment 4e Anthony Cunningham Fundamentals Of Information Performing a vulnerability assessment (4e)fundamentals of information systems security, fourth edition lab 02 your solution’s ready to go! enhanced with ai, our expert help has broken down your problem into an easy to learn solution you can count on. Performing a vulnerability assessment (4e) fundamentals of information systems security, fourth edition lab 02 in this part of the lab, you will use nessus to continue your vulnerability assessment of the secure labs on demand office lan. Itp 125 lab vulnerability assessment overview in this lab, students will use us cyber range perform a vulnerability scan against the vulnerable windows 7 system. students will get more hands on experience with nmap and nmap scripts. the case study informs you of several breaches. Identify and summarize each of the three high severity vulnerabilities identified during your penetration test. for each vulnerability, identify the severity, describe the issue, and recommend a remediation. mysql mariadb weak password [severity: 10] (high)description: the mysql or mariadb database server is using a weak password. The document describes a qualitative risk assessment performed for an it infrastructure. it identifies risks, threats, and vulnerabilities across seven domains: user, workstation, lan, lan to wan, wan, remote access, and systems applications. each risk was assigned a risk impact factor of 1 3. Performing a vulnerability assessment (4e) fundamentals of information systems security, fourth edition lab 02 section 2 of this lab allows you to apply what you learned in section 1 with less guidance and different deliverables, as well as some expanded tasks and alternative methods.

Guide To Vulnerability Assessment Scans And Analysis For Course Hero Itp 125 lab vulnerability assessment overview in this lab, students will use us cyber range perform a vulnerability scan against the vulnerable windows 7 system. students will get more hands on experience with nmap and nmap scripts. the case study informs you of several breaches. Identify and summarize each of the three high severity vulnerabilities identified during your penetration test. for each vulnerability, identify the severity, describe the issue, and recommend a remediation. mysql mariadb weak password [severity: 10] (high)description: the mysql or mariadb database server is using a weak password. The document describes a qualitative risk assessment performed for an it infrastructure. it identifies risks, threats, and vulnerabilities across seven domains: user, workstation, lan, lan to wan, wan, remote access, and systems applications. each risk was assigned a risk impact factor of 1 3. Performing a vulnerability assessment (4e) fundamentals of information systems security, fourth edition lab 02 section 2 of this lab allows you to apply what you learned in section 1 with less guidance and different deliverables, as well as some expanded tasks and alternative methods.
Comments are closed.