List The Properties Which A Hashing Function Should Possess To Ensure A Good Search Performance

List The Properties Which A Hashing Function Should Possess To Ensure A Good Search Performance A good hash function should have the following properties: efficiently computable : the function should be fast to compute. uniform distribution of keys : the hash function should distribute the keys evenly across the hash table (each table position should be equally likely for each key). A good hash function has the following properties: given a hash of a message it is computationally infeasible for an attacker to find another message such that their hashes are identical. given a pair of message, m' and m, it is computationally infeasible to find two such that that h(m) = h(m').

List The Properties Which A Hashing Function Should Possess To Ensure A Good Search Performance I’m going to a mention a few properties of good hashing functions that seem to be generally accepted by most of the sources i have found. for simplicity i am assuming that the keys are integers – we will discuss using strings as keys a bit later. a good hashing function should …. Hash tables are very good if you need to perform a lot of search operations on a relatively stable table (i.e. there are a lot fewer insertion and deletion operations than search operations). One great property of hashing is that all the dictionary operations are incredibly easy to implement. to perform a lookup of a key x, simply compute the index i = h(x) and then walk down the list at a[i] until you find it (or walk off the list). There are two general methods to generate hash function that are both simple and for reasonable distribu tions of keys appearing in the real world will satisfy the simple uniform hashing property well. criteria for choosing a good hash function: it should distribute keys roughly uniformly into slots,.

Comparing The Performance Of Hashing Techniques For Similar Function Detection One great property of hashing is that all the dictionary operations are incredibly easy to implement. to perform a lookup of a key x, simply compute the index i = h(x) and then walk down the list at a[i] until you find it (or walk off the list). There are two general methods to generate hash function that are both simple and for reasonable distribu tions of keys appearing in the real world will satisfy the simple uniform hashing property well. criteria for choosing a good hash function: it should distribute keys roughly uniformly into slots,. Unlike most other fundamental algorithms and data structures, there is no universal consensus on what makes a "good" hash function. the remainder of this section is organized by three criteria: simplicity, speed, and strength, and will survey algorithms known to perform well by these criteria. Hash functions: a good hashing function should have the following properties: it should be e ciently computable, say in constant time and using simple arithmetic operations. Ideally, a hash function with an output value of bitlength m m should require at least 2 m 2 2m 2 operations to find a collision. in a birthday attack, given a set of m equally probable values, roughly 2 m 2 2m 2 random samples are needed to find a single collision. Hash fuctions should have the following properties: i fast computation of the hash value (o(1)). i hash values should be distributed (nearly) uniformly: i every has value (cell in the hash table) has equal probabilty. i this should hold even if keys are non uniformly distributed. the goal of a hash function is: i ‘disperse’ the keys in an.
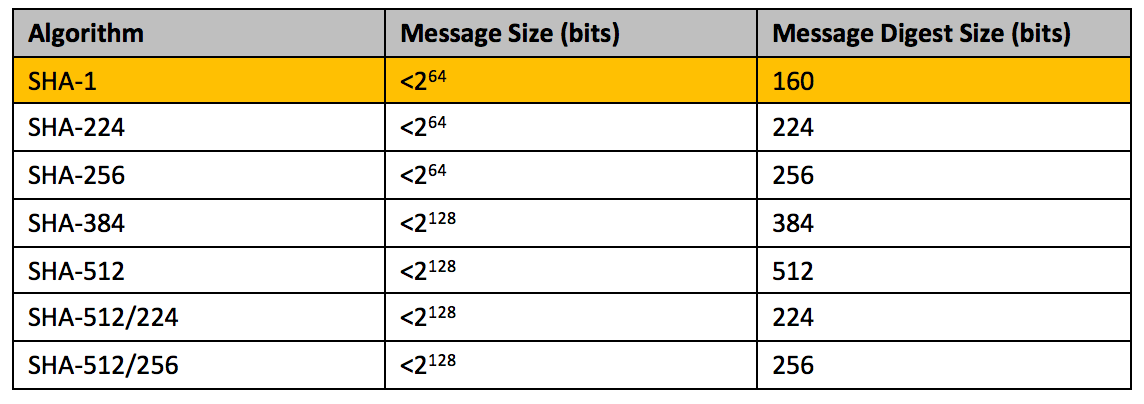
What Is The Hashing Function And Can It Become Vulnerable Venafi Unlike most other fundamental algorithms and data structures, there is no universal consensus on what makes a "good" hash function. the remainder of this section is organized by three criteria: simplicity, speed, and strength, and will survey algorithms known to perform well by these criteria. Hash functions: a good hashing function should have the following properties: it should be e ciently computable, say in constant time and using simple arithmetic operations. Ideally, a hash function with an output value of bitlength m m should require at least 2 m 2 2m 2 operations to find a collision. in a birthday attack, given a set of m equally probable values, roughly 2 m 2 2m 2 random samples are needed to find a single collision. Hash fuctions should have the following properties: i fast computation of the hash value (o(1)). i hash values should be distributed (nearly) uniformly: i every has value (cell in the hash table) has equal probabilty. i this should hold even if keys are non uniformly distributed. the goal of a hash function is: i ‘disperse’ the keys in an.

Hashing Data Structures And Algorithms Interviewbit Ideally, a hash function with an output value of bitlength m m should require at least 2 m 2 2m 2 operations to find a collision. in a birthday attack, given a set of m equally probable values, roughly 2 m 2 2m 2 random samples are needed to find a single collision. Hash fuctions should have the following properties: i fast computation of the hash value (o(1)). i hash values should be distributed (nearly) uniformly: i every has value (cell in the hash table) has equal probabilty. i this should hold even if keys are non uniformly distributed. the goal of a hash function is: i ‘disperse’ the keys in an.
Comments are closed.