Managed Security Faqs All About Vulnerability Management

Guide To Vulnerability Management 1668341881 Pdf Security Computer Security What is vulnerability management? vulnerability management refers to the proactive approach and ongoing process that focuses on identifying, assessing, and mitigating vulnerabilities in an organization’s it infrastructure. This guide explains managed vulnerability management and covers its core functions, benefits, challenges, and best practices. we also talk about the benefits of outsourcing vulnerability management.
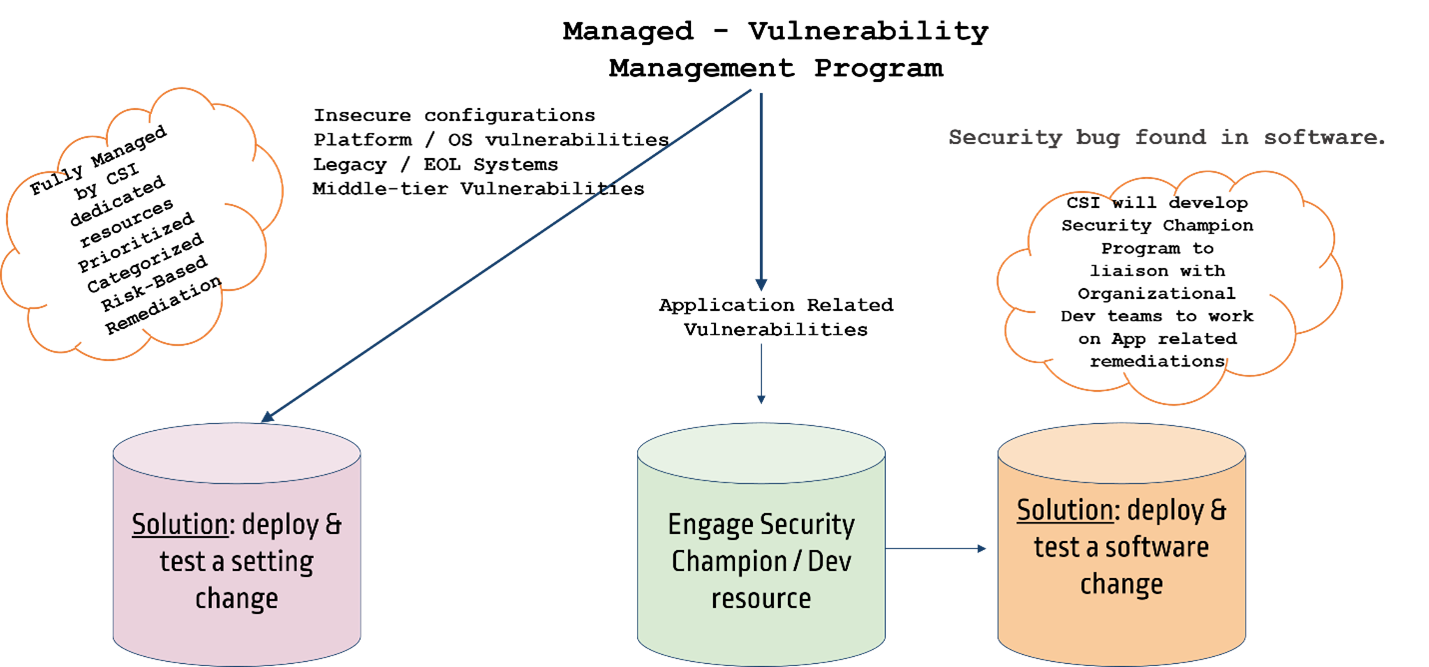
Managed Vulnerability Management Program Cybersecurityinc Vulnerability management is an ongoing process that involves identifying, assessing, prioritizing, and remediating or mitigating security exposures within it infrastructure and software. Vulnerability management is the ongoing, regular process of identifying, assessing, reporting on, managing and remediating cyber vulnerabilities across endpoints, workloads, and systems. typically, a security team will leverage a vulnerability management tool to detect vulnerabilities and utilize different processes to patch or remediate them. Vulnerabilities are software code or architecture weaknesses that attackers could exploit to launch attacks on systems and data. vulnerability management is the process of finding, understanding, and resolving those vulnerabilities before security threats find them. Vulnerability management (vm) refers to the systematic process of identifying, assessing, prioritizing, treating, and monitoring security weaknesses in an organization’s it environment.
Managed Vulnerability Management Secops24 Your Trusted Cybersecurity Services Partner Vulnerabilities are software code or architecture weaknesses that attackers could exploit to launch attacks on systems and data. vulnerability management is the process of finding, understanding, and resolving those vulnerabilities before security threats find them. Vulnerability management (vm) refers to the systematic process of identifying, assessing, prioritizing, treating, and monitoring security weaknesses in an organization’s it environment. Managed vulnerability management or mvm is the systematic and routinely identification, categorization, remediation, and mitigation of vulnerabilities in network infrastructure and applications. Vulnerability management is a systematic process designed to identify, assess, prioritize, remediate, and monitor security flaws across an organization’s information technology (it) infrastructure. vulnerabilities can exist in software, hardware, network configurations, or even operational processes. Vulnerability management focuses on identifying and helping fix security weaknesses across your cloud environments. it covers risks such as exposures, unapplied patches, vulnerable software versions, and gaps in network coverage, while also recommending remediation steps for security teams. Vulnerability management helps ensure business continuity by minimizing the risk of such incidents. the vulnerability management process typically involves several key steps: 1. asset inventory. before vulnerabilities can be managed, organizations need to have a clear understanding of their it assets.

Vulnerability Management Service Video Securityhq Managed vulnerability management or mvm is the systematic and routinely identification, categorization, remediation, and mitigation of vulnerabilities in network infrastructure and applications. Vulnerability management is a systematic process designed to identify, assess, prioritize, remediate, and monitor security flaws across an organization’s information technology (it) infrastructure. vulnerabilities can exist in software, hardware, network configurations, or even operational processes. Vulnerability management focuses on identifying and helping fix security weaknesses across your cloud environments. it covers risks such as exposures, unapplied patches, vulnerable software versions, and gaps in network coverage, while also recommending remediation steps for security teams. Vulnerability management helps ensure business continuity by minimizing the risk of such incidents. the vulnerability management process typically involves several key steps: 1. asset inventory. before vulnerabilities can be managed, organizations need to have a clear understanding of their it assets.

Vulnerability Management Explained Tac Security Vulnerability management focuses on identifying and helping fix security weaknesses across your cloud environments. it covers risks such as exposures, unapplied patches, vulnerable software versions, and gaps in network coverage, while also recommending remediation steps for security teams. Vulnerability management helps ensure business continuity by minimizing the risk of such incidents. the vulnerability management process typically involves several key steps: 1. asset inventory. before vulnerabilities can be managed, organizations need to have a clear understanding of their it assets.
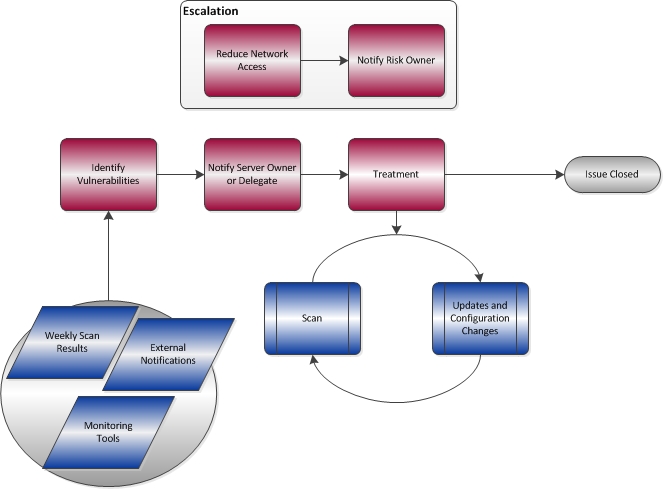
Vulnerability Management Information Technology Security
Comments are closed.