Network Security

How To Ensure Network Security Logsign Securing a network involves continuous monitoring, assessments, and mitigation across various interrelated components, including servers, the cloud, internet of things (iot), internet connections and the many physical assets used to access networks. cisa’s role. Sse is a collection of cloud security capabilities that enable safe browsing, more secure software as a service (saas) application, and an easy approach to validating users accessing network data. moreover, sse is a comprehensive approach to network security, combining networking, security practices and policies, and services to a single platform.

Network Security Professionals Needed Now Ecpi University Bypass network monitoring and security controls and may result in data loss or provide an unsecured network entry point for an attacker. • unauthorized association – an ap to ap association that can violate the security perimeter of the network. • ad hoc connections – a peer to peer network connection that can violate the security. Disable secure shell (ssh) version 1. ensure only ssh version 2.0 is used with the following cryptographic considerations [2]. for more information on acceptable algorithms, see nsa’s network infrastructure security guide. configure with minimally a 3072 bit rsa key. configure with minimally a 4096 diffie hellman key size (group 16). An effective technique to strengthen security, network segmentation is a physical or virtual architectural approach dividing a network into multiple segments, each acting as its own subnetwork providing additional security and control. Demilitarized zone (dmz): in networking, a dmz is a physical or logical subnet that separates a local area network from other untrusted networks. since 2015, the cybersecurity and infrastructure security agency identified boundary protection as the most prevalent discovery in network security architecture assessments across multiple industries.

Network Security Structures Hanatech An effective technique to strengthen security, network segmentation is a physical or virtual architectural approach dividing a network into multiple segments, each acting as its own subnetwork providing additional security and control. Demilitarized zone (dmz): in networking, a dmz is a physical or logical subnet that separates a local area network from other untrusted networks. since 2015, the cybersecurity and infrastructure security agency identified boundary protection as the most prevalent discovery in network security architecture assessments across multiple industries. Developed by the enduring security framework (esf), a cross sector, public private working group, the guidance focuses on addressing some identified threats to 5g standalone network slicing, and provides industry recognized practices for the design, deployment, operation, and maintenance of a hardened 5g standalone network slice(s). This set of guidance, led by international cybersecurity authorities, is intended to help organizations protect their network edge devices and appliances, such as firewalls, routers, virtual private networks (vpn) gateways, internet of things (iot) devices, internet facing servers, and internet facing operational technology (ot) systems. Home network security refers to the protection of a network that connects devices—such as routers, computers, smartphones, and wi fi enabled baby monitors and cameras—to each other and to the internet within a home. many home users share two common misconceptions about the security of their networks: their home network is too small to be at. Use security tools such as endpoint detection and response (edr), web application firewalls, and network protocol analyzers. ask your software providers to discuss their secure by design program, provide links to information about how they are working to remove classes of vulnerabilities, and to set secure default settings. purpose.
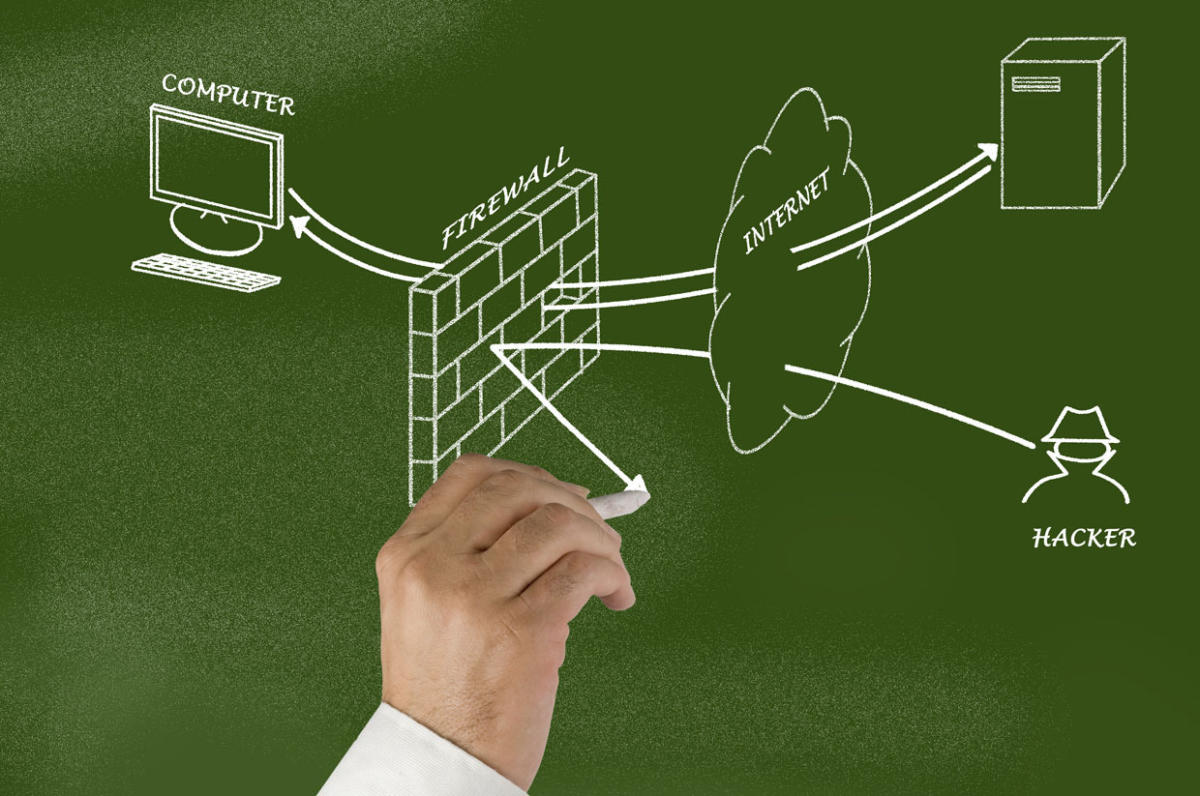
Secure Your Home Network And Every Device Attached To It In 3 Steps Pcworld Developed by the enduring security framework (esf), a cross sector, public private working group, the guidance focuses on addressing some identified threats to 5g standalone network slicing, and provides industry recognized practices for the design, deployment, operation, and maintenance of a hardened 5g standalone network slice(s). This set of guidance, led by international cybersecurity authorities, is intended to help organizations protect their network edge devices and appliances, such as firewalls, routers, virtual private networks (vpn) gateways, internet of things (iot) devices, internet facing servers, and internet facing operational technology (ot) systems. Home network security refers to the protection of a network that connects devices—such as routers, computers, smartphones, and wi fi enabled baby monitors and cameras—to each other and to the internet within a home. many home users share two common misconceptions about the security of their networks: their home network is too small to be at. Use security tools such as endpoint detection and response (edr), web application firewalls, and network protocol analyzers. ask your software providers to discuss their secure by design program, provide links to information about how they are working to remove classes of vulnerabilities, and to set secure default settings. purpose.
Comments are closed.