Network Security Defense Depth Cstor
Network Security Defense Depth Cstor Copyright 2002 2023 cstor a microage company. all rights reserved. privacy policy state of az network equipment website. The cstor series is the industry’s leading packet capture node with up to 100gbps capture to disk rate and extensible onboard secure (encrypted) storage. reliable network data provides historical and transactional data for application performance, latency, and tcp analysis.
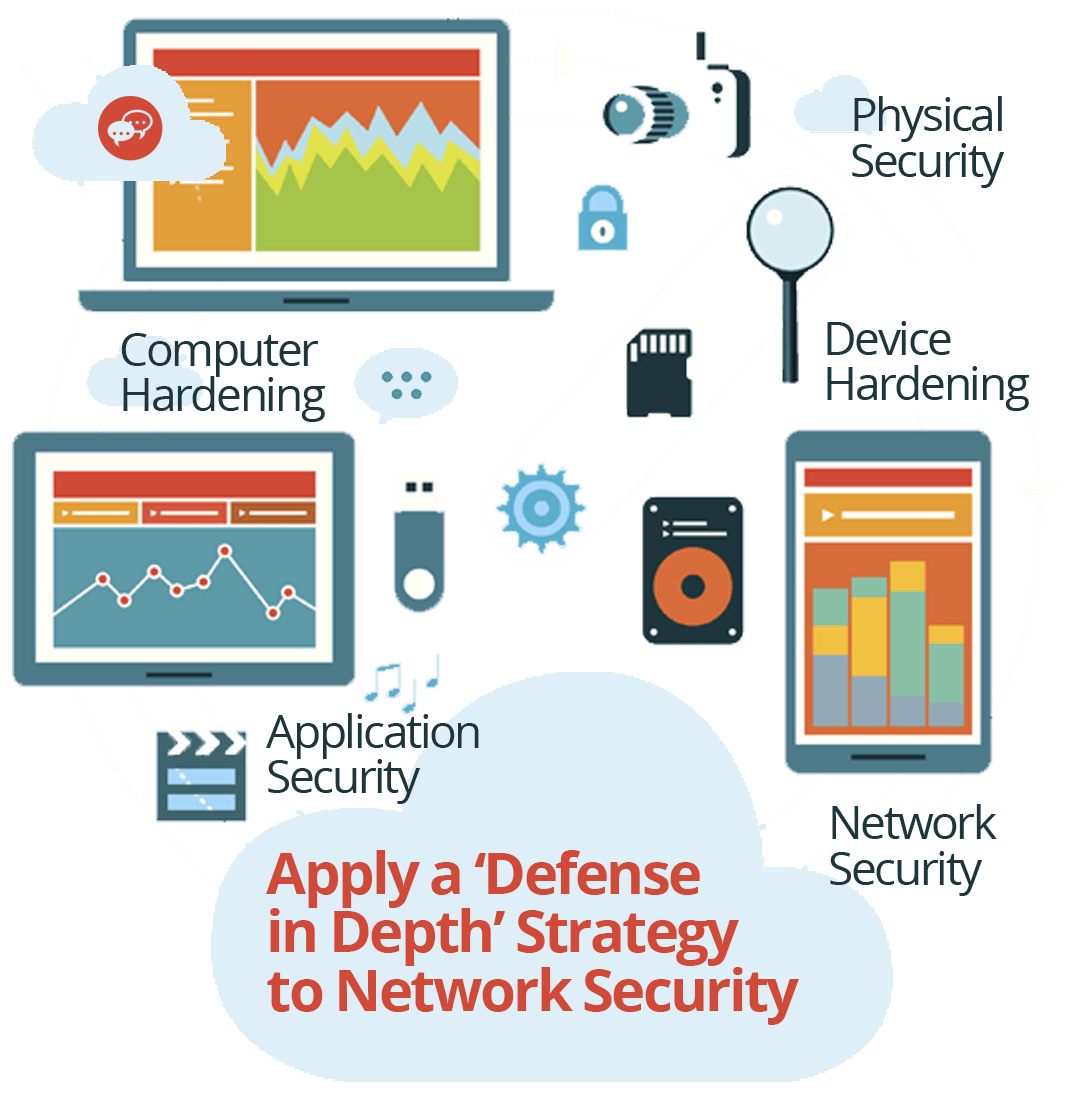
Network Security Layers Cstor Capture and analyze network packet data at line rate me, continuous change and unceasing vigilance against risks. to deliver on those requirements, enterprises need an obser. Summary defense in depth provides redundancy and strength by layering security controls. no single tool or process is enough—each layer reinforces the others. for a video on this topic, visit our az 900 video course for real world demos and expert explanations – or go back to the az 900 list of topics. The cpacket cstor series packet capture appliances are high performance solutions designed for comprehensive network monitoring, security forensics, and regulatory compliance. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in tandem on the assumption that if one fails, another will hold.

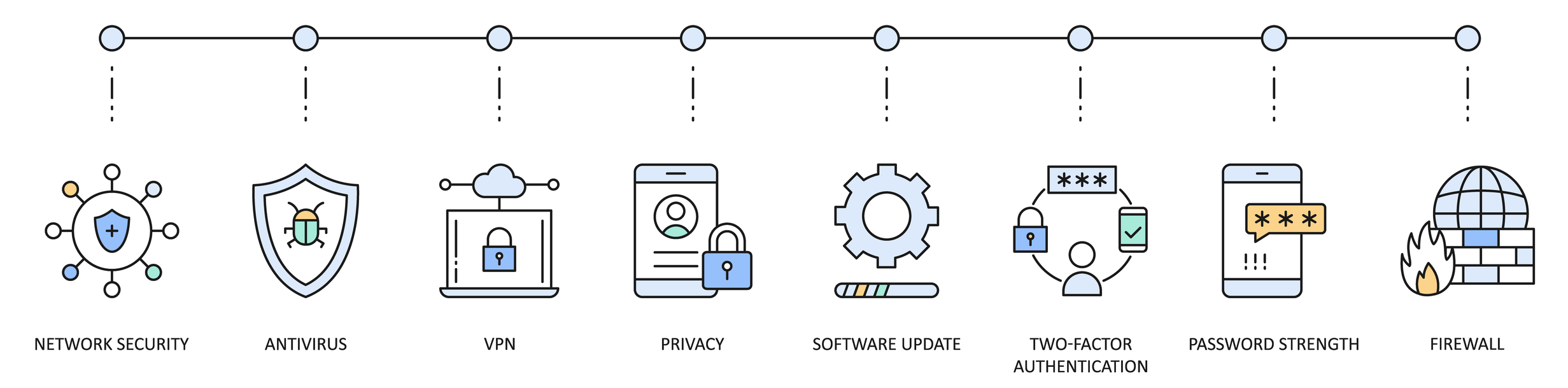
Defense In Depth Network Security Best Practices In 2024 Email Security Network Security The cpacket cstor series packet capture appliances are high performance solutions designed for comprehensive network monitoring, security forensics, and regulatory compliance. Defense in depth is a security strategy in which multiple security tools, mechanisms, and policies are deployed in tandem on the assumption that if one fails, another will hold. One of the most effective strategies to enhance network security is "defense in depth." this concept extends beyond simple perimeter protection, creating a robust framework that integrates various security measures across different layers of an it infrastructure. Streamed and stored network packet data is vital for maximising security posture and observability of your network, it infrastructure, and application workloads. Defense in depth: multiple layers of protection fortifying your cyber defenses webcast 4 of 5 in our special series—explore the full lineup here. in today’s complex threat landscape, no single security solution is enough. The result is an easy to manage, cost optimized solution that makes the best use of rack space; while providing the breadth and depth of packet data analysis to drive analytics, security forensics, application, user, and network performance.
Comments are closed.