Otp Bots What They Are And How To Prevent Attacks Logto Blog
Otp Bots What They Are And How To Prevent Attacks Logto Blog Learn what otp bots are, how they exploit one time passwords with real cases, and strategies to protect your business from these cyber threats. this guide offers actionable tips for professionals in product development and enterprise management. Summary: learn how otp bots steal one time passwords, the growing risks for businesses, and practical steps to block attacks before they compromise your network.
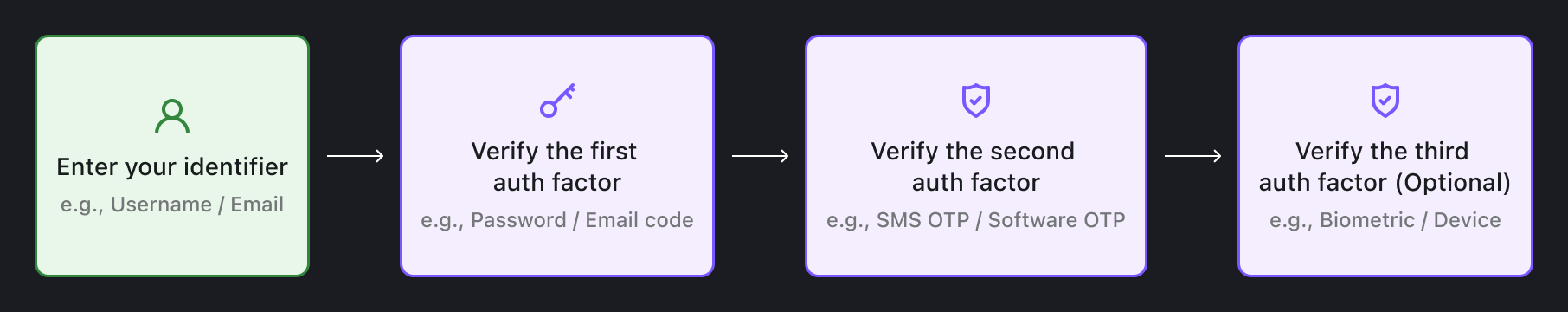
Otp Bots What They Are And How To Prevent Attacks Logto Blog Otp bots are automated software programs that are designed to bypass two factor authentication (2fa) systems. otp bots are typically used for financial gain, such as accessing and draining bank accounts or making fraudulent transactions. To stay ahead of these threats, it’s crucial to understand how otp bots operate, who they target, and the best practices for stopping them. in this article, we’ll cover all these points and provide actionable strategies to help you safeguard your accounts. Explore how otp bots bypass two factor authentication (2fa), their growing threats, and strategies to protect your application using tools like supertokens. Attackers are increasingly using specialized otp bots to intercept codes. digital businesses must take urgent steps for bot detection and to prevent otp bots from causing damage to business and consumer interests.

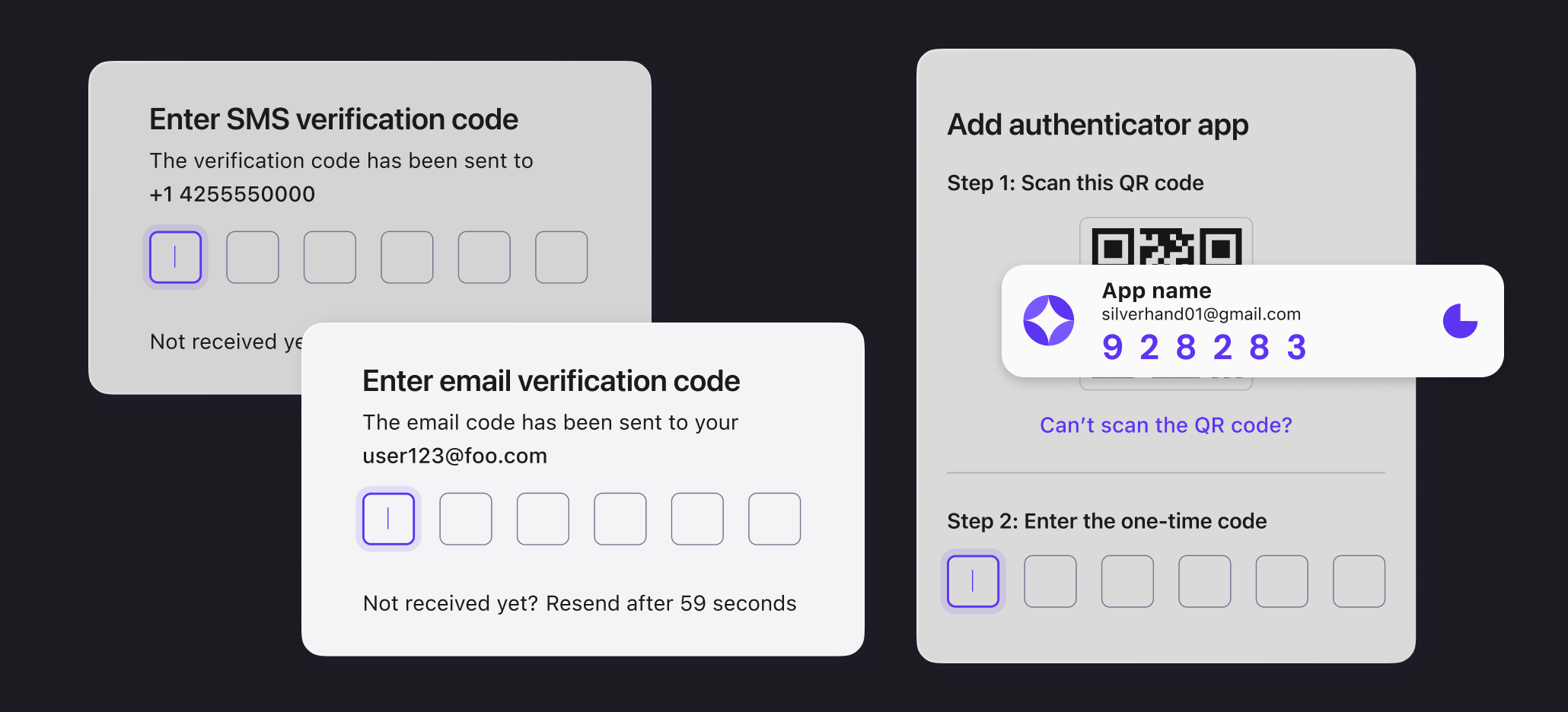
Otp Bots What They Are And How To Prevent Attacks Logto Blog Explore how otp bots bypass two factor authentication (2fa), their growing threats, and strategies to protect your application using tools like supertokens. Attackers are increasingly using specialized otp bots to intercept codes. digital businesses must take urgent steps for bot detection and to prevent otp bots from causing damage to business and consumer interests. The most effective fraud prevention doesn’t just react to bots at the otp step; it stops them before they trigger otps in the first place. but to do that, you need to understand how modern bots operate and how our bot detection solutions, powered by neuroid, fight back. Otp bots are sophisticated automated programs that are designed to intercept and steal one time authentication codes. they exploit the trust that people place in mfa systems, tricking them into sharing temporary verification codes sent via email, sms, or authentication apps. This article aims to demystify otp bots—explaining what they are, how they function, and how individuals and organizations can protect themselves against these threats. These automated systems are designed to intercept and steal otps by tricking target users to disclose this sensitive information either through an automated phone call or messages. attackers then use these codes to authenticate themselves and gain unauthorized access to take over the target account.

Logto Blog The most effective fraud prevention doesn’t just react to bots at the otp step; it stops them before they trigger otps in the first place. but to do that, you need to understand how modern bots operate and how our bot detection solutions, powered by neuroid, fight back. Otp bots are sophisticated automated programs that are designed to intercept and steal one time authentication codes. they exploit the trust that people place in mfa systems, tricking them into sharing temporary verification codes sent via email, sms, or authentication apps. This article aims to demystify otp bots—explaining what they are, how they function, and how individuals and organizations can protect themselves against these threats. These automated systems are designed to intercept and steal otps by tricking target users to disclose this sensitive information either through an automated phone call or messages. attackers then use these codes to authenticate themselves and gain unauthorized access to take over the target account.

Logto Blog The Content Hub Of The Logto Community This article aims to demystify otp bots—explaining what they are, how they function, and how individuals and organizations can protect themselves against these threats. These automated systems are designed to intercept and steal otps by tricking target users to disclose this sensitive information either through an automated phone call or messages. attackers then use these codes to authenticate themselves and gain unauthorized access to take over the target account.
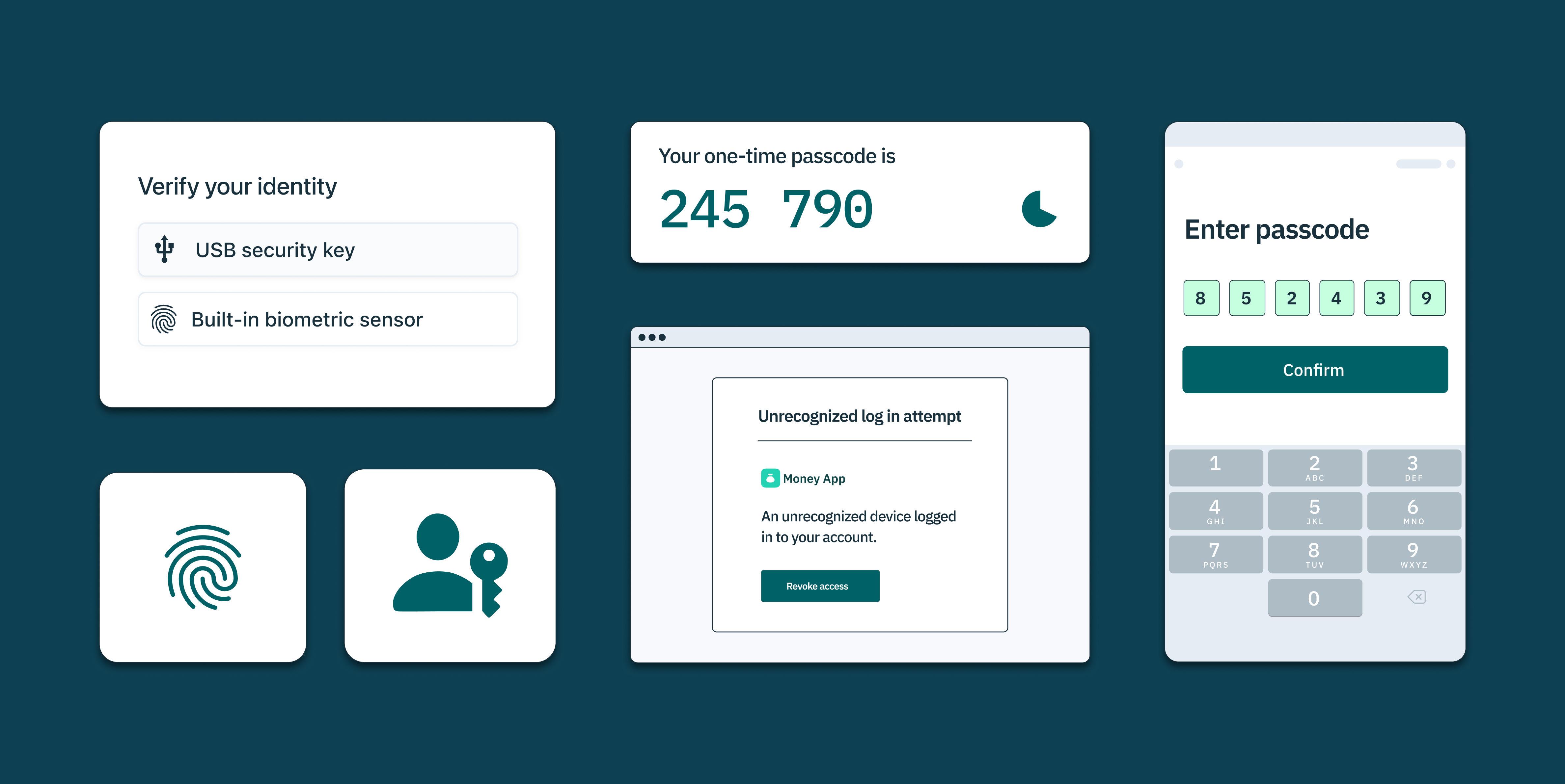
One Time Password Otp Bots What They Are And How To Stop Them
Comments are closed.