Protect Your Data And Enhance Security Trusted Computing Group
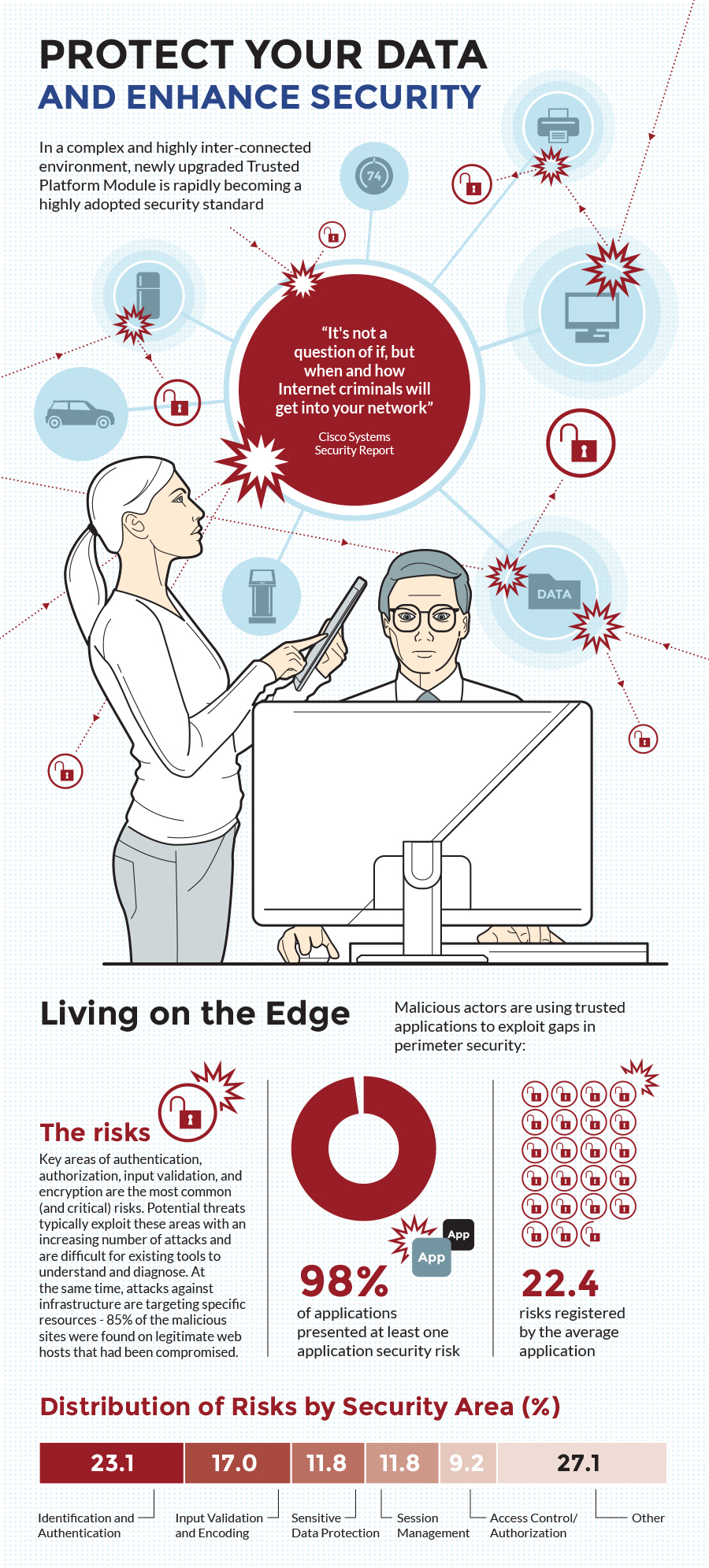
Protect Your Data And Enhance Security Trusted Computing Group Tpm, the trusted platform module, created by trusted computing group. tpm is kind of a digital fingerprint, a microcontroller that stores keys, passwords and digital certificates, enabling: protect your entire digital environment technologies already supporting tpm 2.0 integrity checks of systems with the tpm authentication cryptographic. To preserve the privacy of attestation responders, direct anonymous attestation has been proposed as a solution, which uses a group signature scheme to prevent revealing the identity of individual signers.
Trusted Computing Group Protect Your Data Microsoft enables trustworthy ai by prioritizing security, privacy, and safety. learn more about the commitments we’ve made to ensure your data is safeguarded, our practices are transparent, and your rights are protected. our advanced safety tools and proactive measures are designed to protect you. The trusted computing group (tcg) is instrumental in setting industry wide standards and specifications that address cybersecurity challenges and promote the use of technologies like the trusted platform module (tpm). To this end, the data center work group at tcg has been formed to establish trust within systems and components within a data center, focusing primarily on developing protective measures. Ensuring trusted computing for over twenty years, the tpm is a low cost, secure crypto processor which is attached to a device to establish secure operations and protect a user’s identity and sensitive data.

Tpm 2 0 The New Standard For Secure Firmware Help Net Security To this end, the data center work group at tcg has been formed to establish trust within systems and components within a data center, focusing primarily on developing protective measures. Ensuring trusted computing for over twenty years, the tpm is a low cost, secure crypto processor which is attached to a device to establish secure operations and protect a user’s identity and sensitive data. Tcg provides a wideranging set of network security standards called trusted network connect (tnc). the tnc standards include support for endpoint assessment with continuous monitoring, network access control (nac), and security automation. Ensuring the concept of trusted computing for 25 years now, the tpm is a secure crypto processor which is attached to a device for secure operations. using a tpm helps to protect a user’s identity and sensitive data by storing the keys crucial to encryption, decryption and authentication. The trusted computing group is a non profit group of companies formed for promoting trust and security in computing platforms (tcg, 2015a). the group has developed a trusted platform module (tpm) specification to support trusted computing. Benefits of tcg technologies include protection of business critical data and systems, secure authentication and strong protection of user identities, and the establishment of strong machine identity and network integrity.

Ppt Security Privacy And Data Protection For Trusted Cloud Computing Powerpoint Presentation Tcg provides a wideranging set of network security standards called trusted network connect (tnc). the tnc standards include support for endpoint assessment with continuous monitoring, network access control (nac), and security automation. Ensuring the concept of trusted computing for 25 years now, the tpm is a secure crypto processor which is attached to a device for secure operations. using a tpm helps to protect a user’s identity and sensitive data by storing the keys crucial to encryption, decryption and authentication. The trusted computing group is a non profit group of companies formed for promoting trust and security in computing platforms (tcg, 2015a). the group has developed a trusted platform module (tpm) specification to support trusted computing. Benefits of tcg technologies include protection of business critical data and systems, secure authentication and strong protection of user identities, and the establishment of strong machine identity and network integrity.
Comments are closed.