Scans Failing On V0 94 0 Issue 5320 Semgrep Semgrep Github
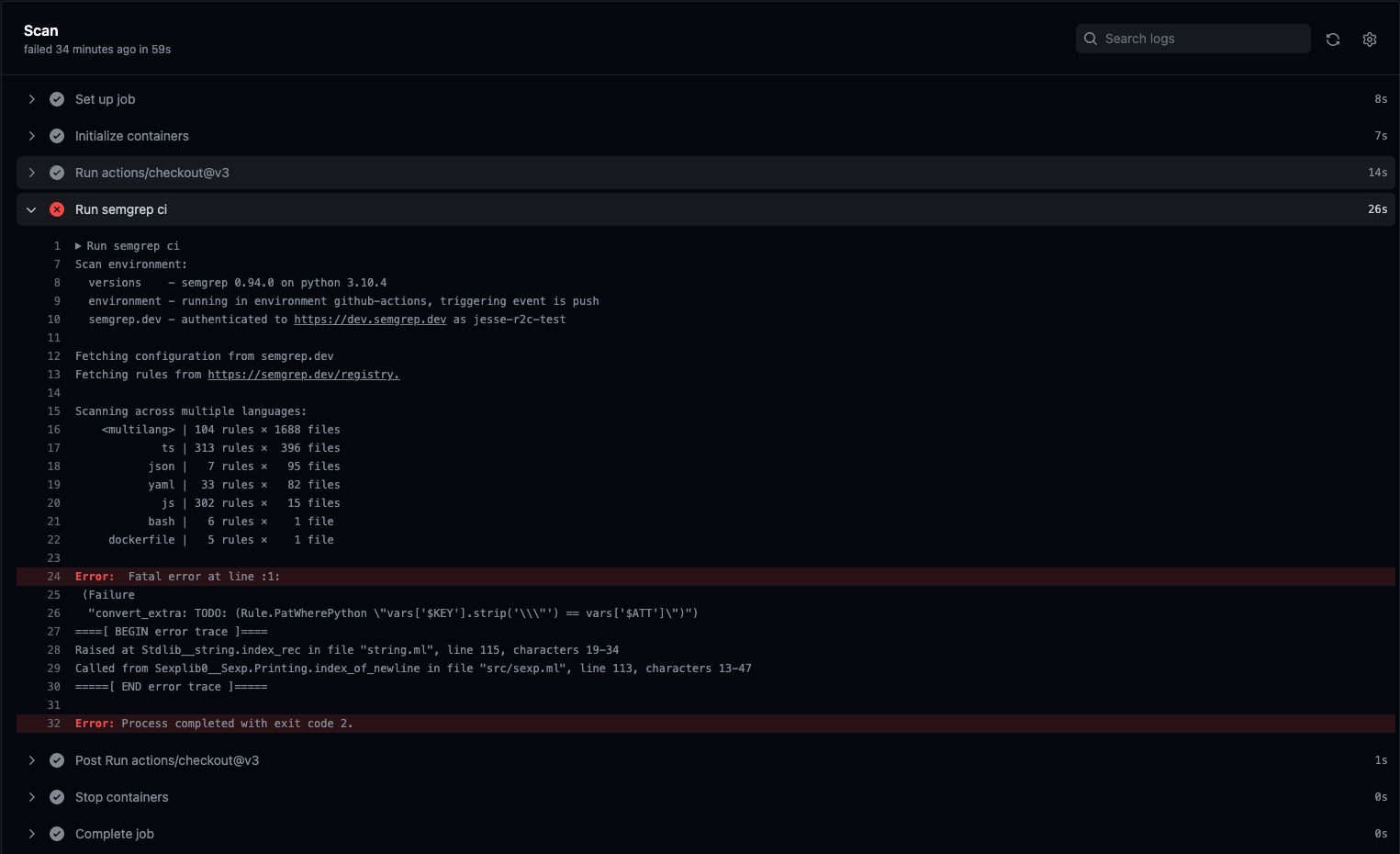
Scans Failing On V0 94 0 Issue 5320 Semgrep Semgrep Github Describe the bug semgrep is failing to run scans against a test repo (juice shop) relevant scan: github jesse r2c test juice shop runs 6611340414?check suite focus=true to reproduce for. If a semgrep scan is failing or running slowly, try the following steps to investigate: update semgrep to the latest version, if you are not currently running the latest version. some errors result from an older version of semgrep being used with newer rules.
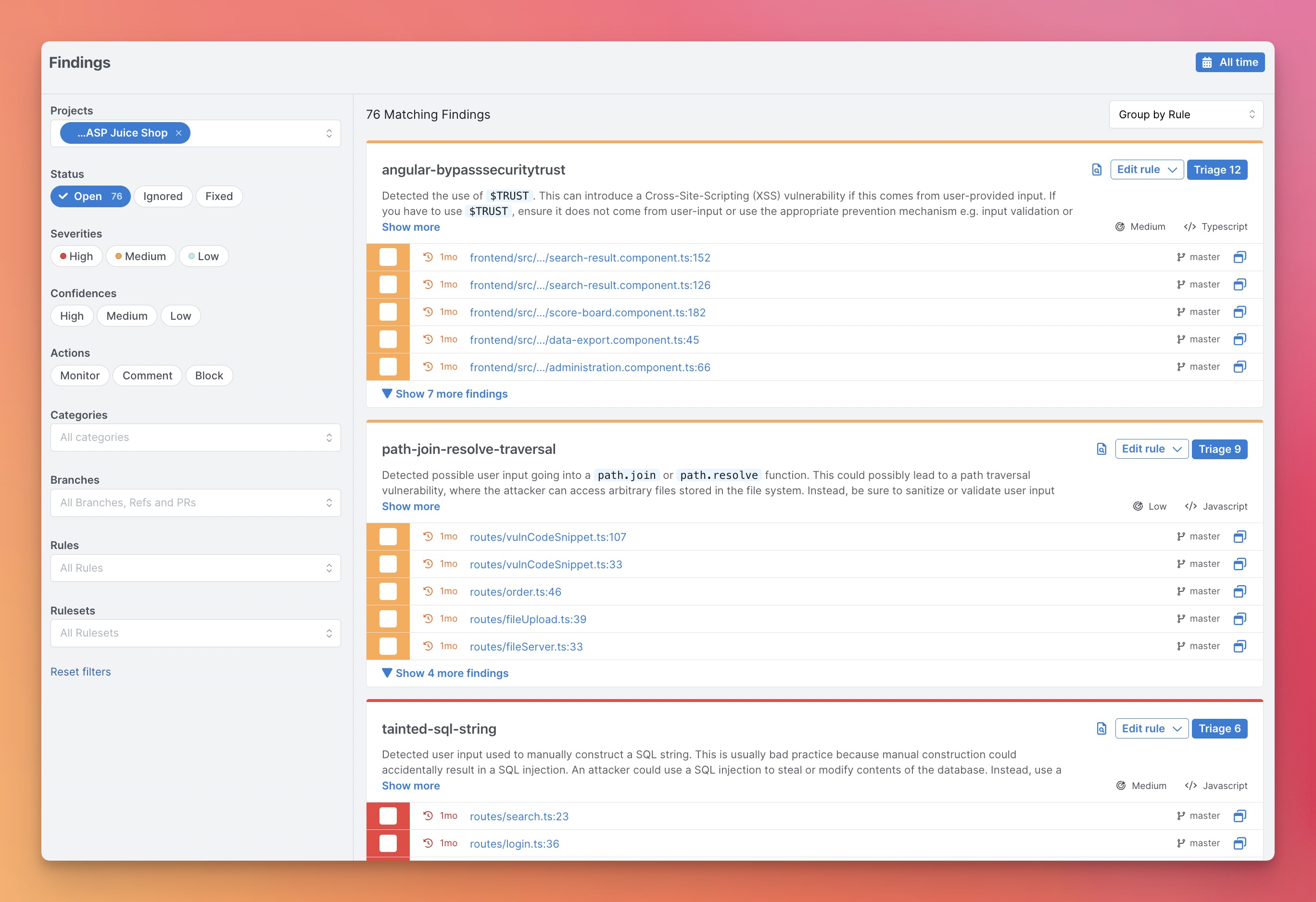
Github Semgrep Semgrep Lightweight Static Analysis For Many Languages Find Bug Variants With When pressing scan all files in the workspace the extension generates semgrep processes and then they die within 5 10 secs of working. it can scan very small files this way but can't handle large ones (will attach one for example). How to fix "semgreperror error while running rules: 0 bytes read on a total of 2 expected bytes" error for semgrep analyzer? i am trying to integrate gitlab sast into my pipeline and facing the following error for semgrep analyzer during generation of the report. Learn how to set up semgrep, scan your first project for security issues, and view your findings in the cli. To do that, we will take one application security activity which is sast scans, discuss two ways to “shift it left”, and illustrate its benefits with a real world example using semgrep.
Github Semgrep Semgrep Lightweight Static Analysis For Many Languages Find Bug Variants With Learn how to set up semgrep, scan your first project for security issues, and view your findings in the cli. To do that, we will take one application security activity which is sast scans, discuss two ways to “shift it left”, and illustrate its benefits with a real world example using semgrep. Grype can scan a variety of sources beyond those found in docker. # scan a container image archive (from the result of `docker image save …`, `podman save …`, or `skopeo copy` commands) grype path to image.tar # scan a directory grype dir:path to dir . the output format for grype is configurable as well: grype
Offline Execution Issue 8793 Semgrep Semgrep Github Grype can scan a variety of sources beyond those found in docker. # scan a container image archive (from the result of `docker image save …`, `podman save …`, or `skopeo copy` commands) grype path to image.tar # scan a directory grype dir:path to dir . the output format for grype is configurable as well: grype
Github Semgrep Semgrep Vscode Semgrep Extension For Visual Studio Code For me, it looks like any semgrep scan test run using versions 1.99 or 1.101 (i've tested those two) results in the issue. unfortunately, i don't have a minimal reproducible rule file to share at the moment. When integrated into ci and configured to scan pull requests, semgrep will only report issues introduced by that pull request; this lets you start using semgrep without fixing or ignoring pre existing issues!.
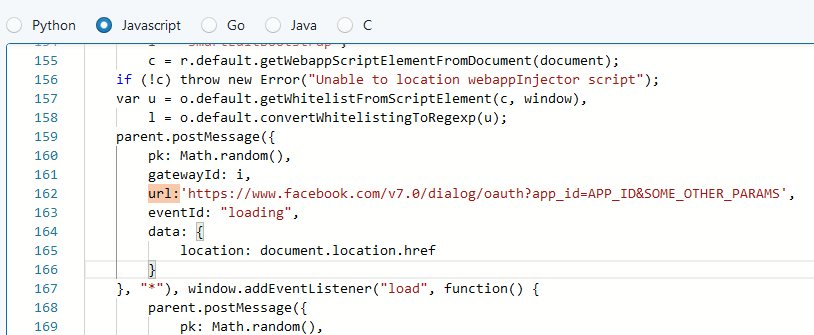
Semgrep Postmessage Detection Issue 810 Semgrep Semgrep Github
Comments are closed.