Semgrep Findings Range Extends Too Far Issue 7532 Semgrep Semgrep Github
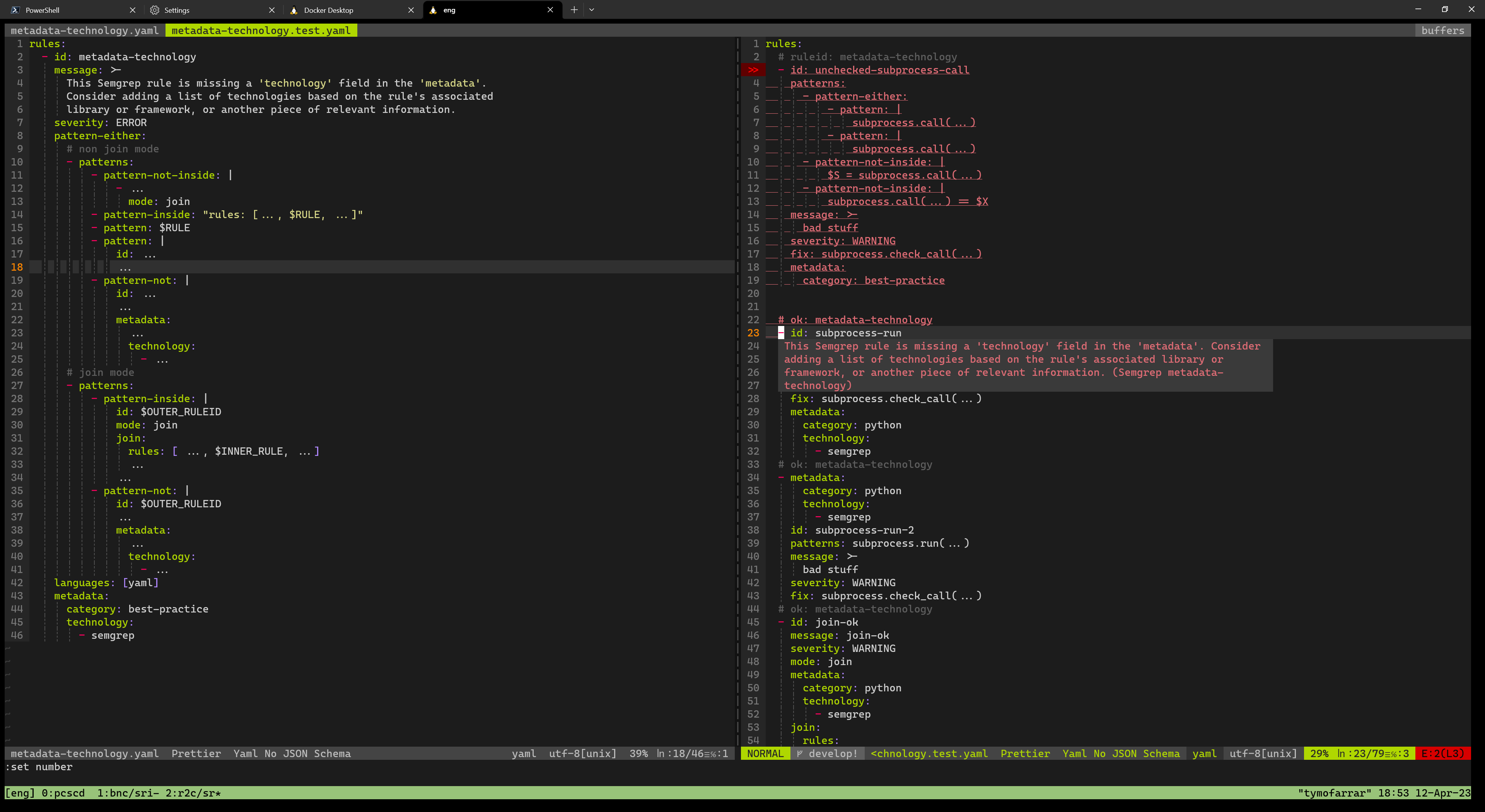
Semgrep Findings Range Extends Too Far Issue 7532 Semgrep Semgrep Github Semgrep runs anywhere you need it, from cli to ci cd. findings can be surfaced in developer workflows, the semgrep appsec platform, or in your existing tools via api. Read the documentation and get started with semgrep. a fast static analysis engine for finding bugs, detecting dependency vulnerabilities, and enforcing code standards at editor, commit, and ci time.
A Bug Issue 7532 Files Community Files Github Learn how to set up semgrep, scan your first project for security issues, and view your findings. a project can be any codebase, repository, or folder within a monorepo. Semgrep code uses rules, which encapsulate pattern matching logic and data flow analysis, to scan your code for security issues, style violations, bugs, and more. semgrep generates and reports findings to you whenever it finds code that matches the patterns defined by rules. Dive into the fundamentals of static code analysis, software supply chain security, and secret scanning with semgrep in this introductory course. Semgrep supply chain's license compliance feature enables you to explicitly allow or disallow (block) a package's use in your repository based on its license. for example, your company policy may disallow the use of packages with the creative commons attribution noncommercial (cc by nc) license.

View Findings Semgrep Dive into the fundamentals of static code analysis, software supply chain security, and secret scanning with semgrep in this introductory course. Semgrep supply chain's license compliance feature enables you to explicitly allow or disallow (block) a package's use in your repository based on its license. for example, your company policy may disallow the use of packages with the creative commons attribution noncommercial (cc by nc) license. A summary of differences between grep, linters, and semgrep. in addition to being a security tool, once customized, semgrep can be used as a linter to help you and your team codify and follow best practices and to detect code smells. Semgrep aims to provide comprehensive and accurate detection of common owasp top 10 issues in source code. semgrep uses rules , which are instructions based on which it detects patterns in code. these rules are usually organized in rulesets. Comparison semgrep vs. snyk. learn how semgrep improves accuracy, saves time, and delivers a superior developer experience. No. semgrep runs either locally or fully in your ci pipeline, and your source code never leaves your computer or your ci environment. only meta data related to semgrep runs (see docs) are sent to semgrep's service.

View Findings Semgrep A summary of differences between grep, linters, and semgrep. in addition to being a security tool, once customized, semgrep can be used as a linter to help you and your team codify and follow best practices and to detect code smells. Semgrep aims to provide comprehensive and accurate detection of common owasp top 10 issues in source code. semgrep uses rules , which are instructions based on which it detects patterns in code. these rules are usually organized in rulesets. Comparison semgrep vs. snyk. learn how semgrep improves accuracy, saves time, and delivers a superior developer experience. No. semgrep runs either locally or fully in your ci pipeline, and your source code never leaves your computer or your ci environment. only meta data related to semgrep runs (see docs) are sent to semgrep's service.
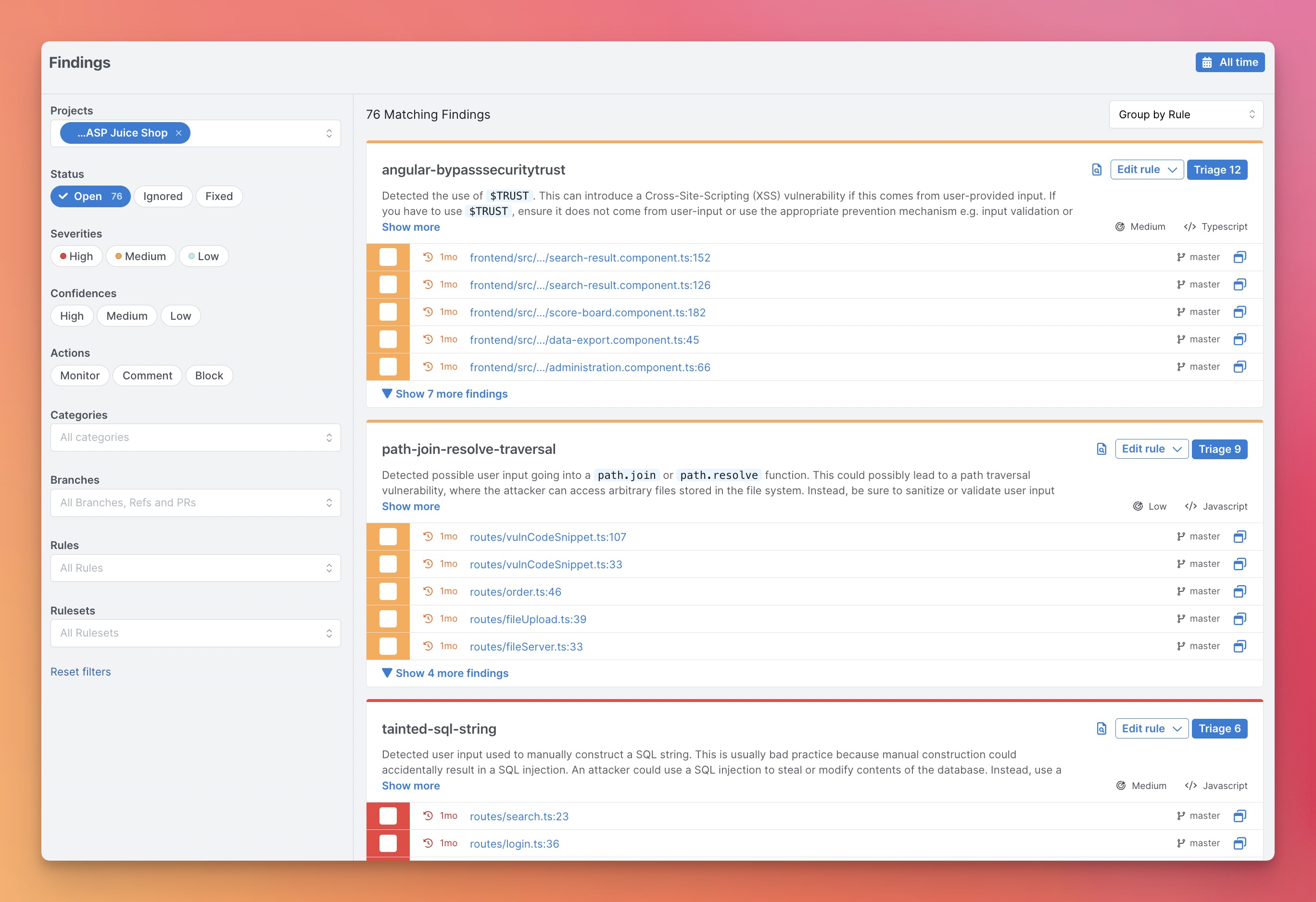
Github Semgrep Semgrep Lightweight Static Analysis For Many Languages Find Bug Variants With Comparison semgrep vs. snyk. learn how semgrep improves accuracy, saves time, and delivers a superior developer experience. No. semgrep runs either locally or fully in your ci pipeline, and your source code never leaves your computer or your ci environment. only meta data related to semgrep runs (see docs) are sent to semgrep's service.
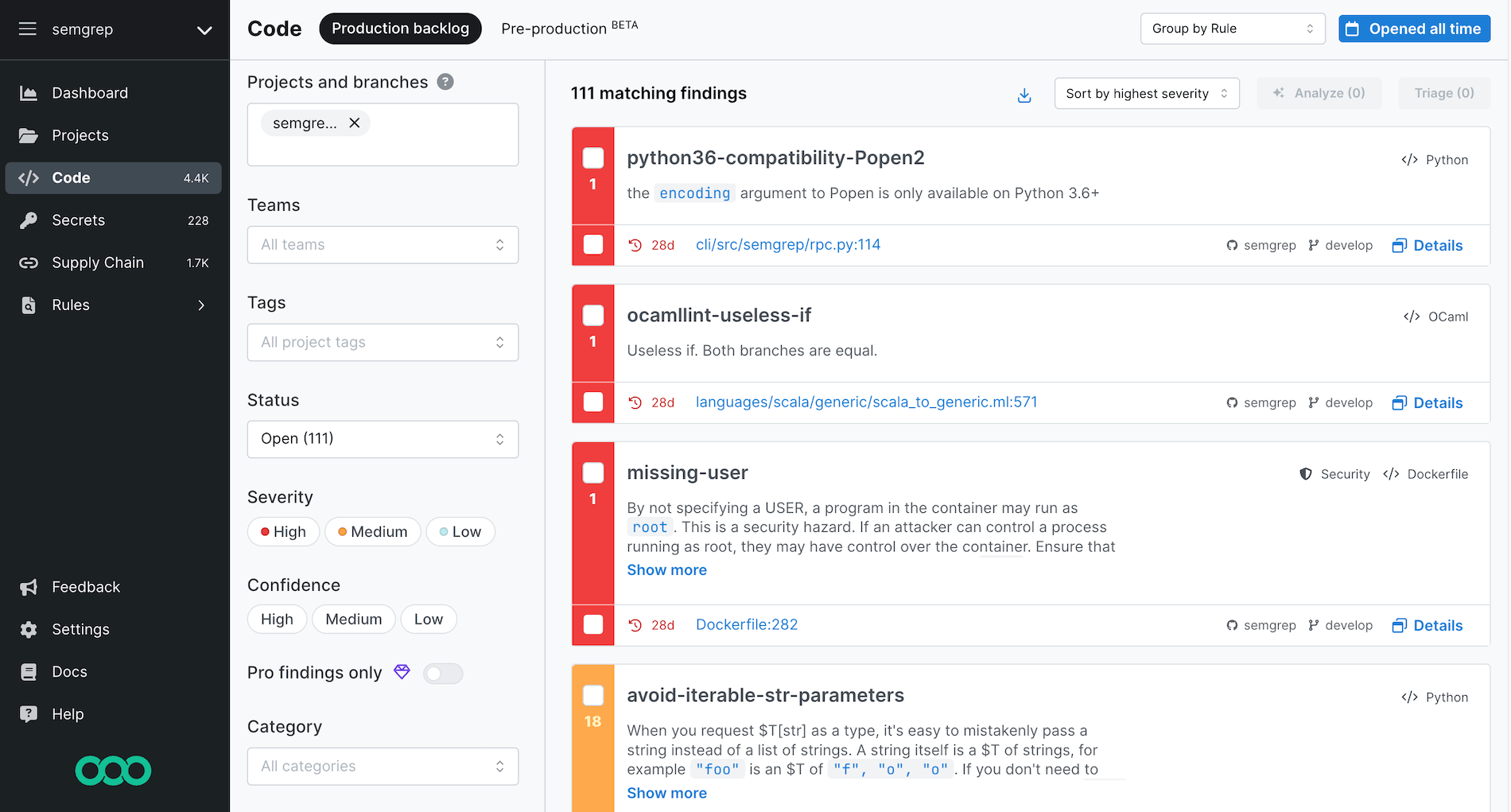
View Findings Semgrep
Comments are closed.