Semgrep Playground Fails To Run From Defined Branch On Page Load Issue 4599 Semgrep Semgrep
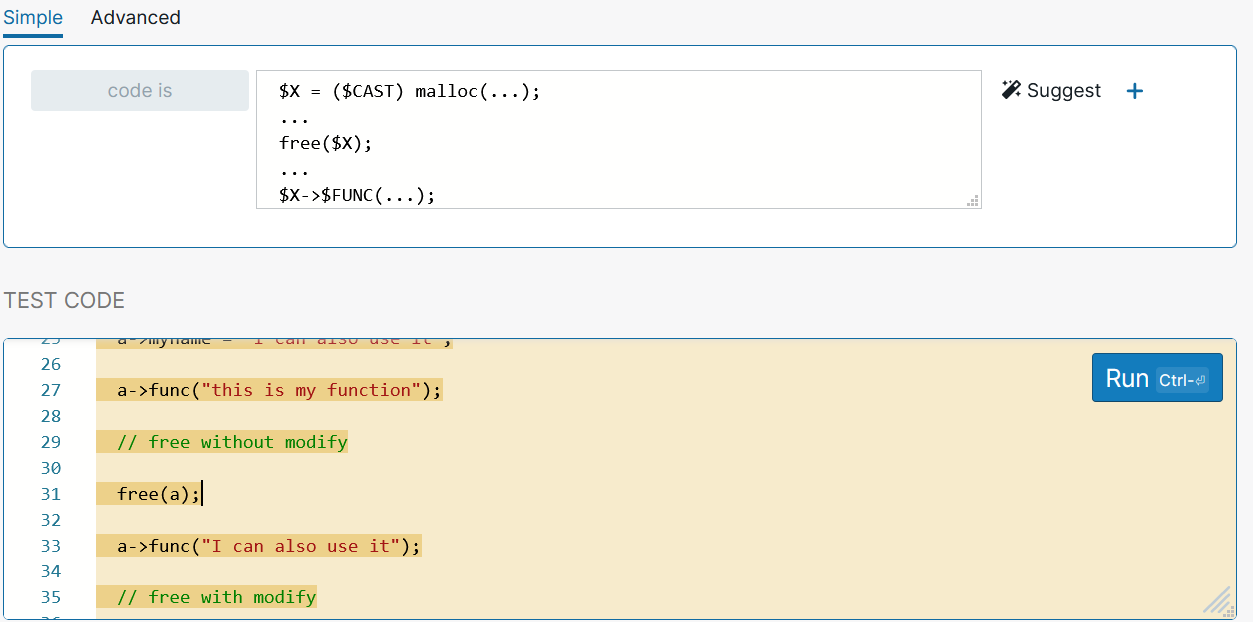
A Brief Introduction To Semgrep Part 2 Trustfoundry I've deployed a fix for this issue, so i'll close it. if you feel like this hasn't been fully addressed or if you see it pop up again, feel free to re open and add more context. This document outlines troubleshooting steps for issues related to semgrep scans in a ci environment. refer to the following sections if you're seeing results reported on files that have not changed since the last scan, frequent timeouts, or other issues.
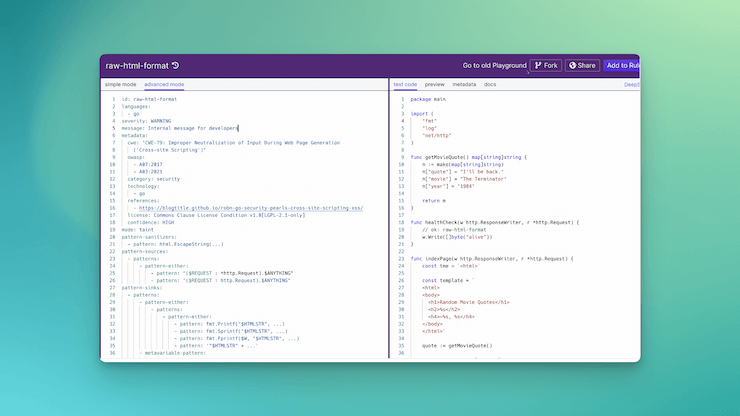
Semgrep How to fix "semgreperror error while running rules: 0 bytes read on a total of 2 expected bytes" error for semgrep analyzer? i am trying to integrate gitlab sast into my pipeline and facing the following error for semgrep analyzer during generation of the report. the error: to disable registry rule metrics, use " metrics=off". Run git submodule update recursive. make sure to follow the development workflow so that pre commit will run on commit. sometimes changes you make will cause pre commit errors in code you haven't touched for example, if you change a function's return type. The fix has been merged and will be included in our next release. i'm going to keep this issue open until the next version is published to pypi and i've verified the fix fully end to end. Hi, i've setup semgrep agent in my gitlab and it works fine (without setting the semgrep rules variable). but as soon as i add the semgrep rules variable in my .gitlab ci.yml file, the semgrep agent step fails with the following error: cannot run semgrep ci while logged in and with explicit config. use semgrep.dev to configure rules to run.
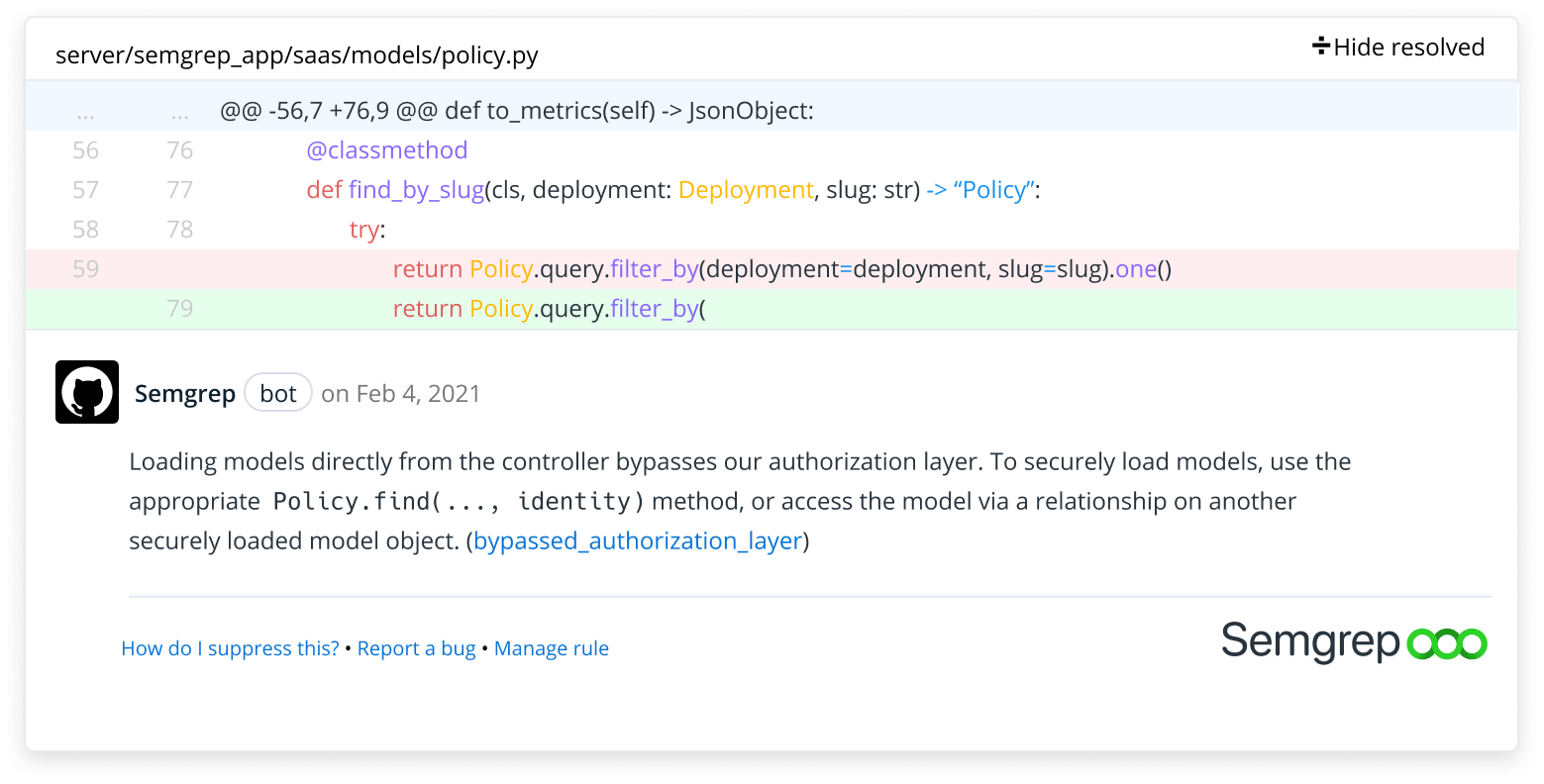
Semgrep The fix has been merged and will be included in our next release. i'm going to keep this issue open until the next version is published to pypi and i've verified the fix fully end to end. Hi, i've setup semgrep agent in my gitlab and it works fine (without setting the semgrep rules variable). but as soon as i add the semgrep rules variable in my .gitlab ci.yml file, the semgrep agent step fails with the following error: cannot run semgrep ci while logged in and with explicit config. use semgrep.dev to configure rules to run. The same config file with the same source files and same semgrep version is working is expected when semgrep is installed with brew or running inside a container. When we run semgrep sast on java projects, we see a stack overflow error. we have checked out runner config and they have 8.5gb memory capacity, the container for semgrep is not getting close to that capacity. You can safely ignore these warnings as they have no impact on the scan performance or efficacy – the logs are a result of the false positive detection step that executes after the semgrep scan. Deployment handling blocking findings and errors this article documents how semgrep handles blocking findings and errors and how you can change semgrep's default behavior. blocking findings blocking findings are those identified by semgrep code using rules defined in semgrep appsec platform's policies page and are set to block mode.

Semgrep The same config file with the same source files and same semgrep version is working is expected when semgrep is installed with brew or running inside a container. When we run semgrep sast on java projects, we see a stack overflow error. we have checked out runner config and they have 8.5gb memory capacity, the container for semgrep is not getting close to that capacity. You can safely ignore these warnings as they have no impact on the scan performance or efficacy – the logs are a result of the false positive detection step that executes after the semgrep scan. Deployment handling blocking findings and errors this article documents how semgrep handles blocking findings and errors and how you can change semgrep's default behavior. blocking findings blocking findings are those identified by semgrep code using rules defined in semgrep appsec platform's policies page and are set to block mode.
Comments are closed.