Sim Swapping Explained How You Can Easily Avoid It

Sim Swapping Explained Sim swap fraud occurs when scammers take advantage of a weakness in two factor authentication and verification and use your phone number to access your accounts. sim swapping happens when scammers contact your mobile phone’s carrier and trick them into activating a sim card that the fraudsters have. Learn about sim swap fraud, where scammers hijack phone numbers to gain control of personal accounts. discover tactics used, warning signs, and tips to protect yourself.

What Is Sim Swapping And How To Avoid Fraud In this video, josh walks us through what sim swapping is, how it works, and how you prevent it from happening to you. read more about the sim swapping attack here:. Sim swapping involves transferring your legitimate phone number to another sim card through carrier channels. once complete, your original sim card becomes inactive. whereas, sim cloning involves creating an exact duplicate of your existing sim card without deactivating the original. Sim swapping lets attackers hijack your phone number to access accounts and bypass 2fa. they use phishing, data breaches, or insider help to trick carriers into switching your sim. signs include lost service, account lockouts, and unauthorized transactions. How should you respond to a sim swapping attack? sim swapping is a method hackers use to bypass two factor authentication (2fa) by tricking phone companies into transferring a phone number to a new sim card.
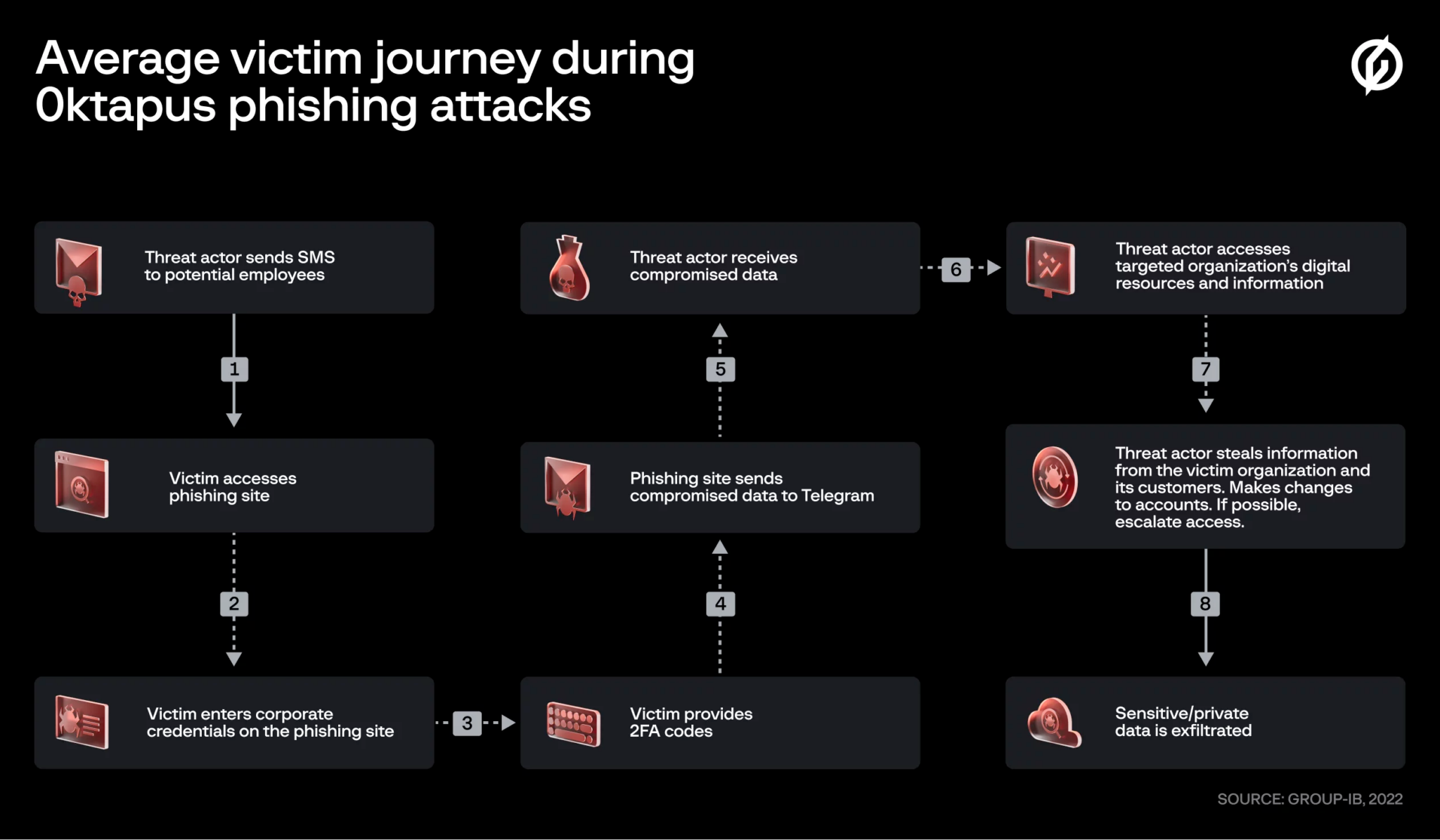
Sim Swapping An Overview Occamsec Sim swapping lets attackers hijack your phone number to access accounts and bypass 2fa. they use phishing, data breaches, or insider help to trick carriers into switching your sim. signs include lost service, account lockouts, and unauthorized transactions. How should you respond to a sim swapping attack? sim swapping is a method hackers use to bypass two factor authentication (2fa) by tricking phone companies into transferring a phone number to a new sim card. Here’s how you can avoid sim jacking or sim swap fraud: add a sim lock and other account passcodes. every time your sim card is removed, it locks and requests a pin number. Unauthorized sim changes, sometimes called sim swapping or sim hijacking attacks, occur when a customer’s phone number is transferred to a different sim card or esim profile under the control of a criminal. To convince the operator to perform this operation, he will use personal information about you on the internet or by other means (address, date of birth, etc.). if the operator’s customer service considers that it is you, it will reallocate your telephone number on the fraudster card. Learn more about your sim (subscriber identity module), what this sim swap fraud looks like, and how you can avoid it here. sim swapping can be done remotely without needing physical access to your phone. it’s surprisingly easy for customer service agents to fall victim to social engineering attacks by hackers.
What Is Sim Swapping How To Protect From Sim Swap Attacks Here’s how you can avoid sim jacking or sim swap fraud: add a sim lock and other account passcodes. every time your sim card is removed, it locks and requests a pin number. Unauthorized sim changes, sometimes called sim swapping or sim hijacking attacks, occur when a customer’s phone number is transferred to a different sim card or esim profile under the control of a criminal. To convince the operator to perform this operation, he will use personal information about you on the internet or by other means (address, date of birth, etc.). if the operator’s customer service considers that it is you, it will reallocate your telephone number on the fraudster card. Learn more about your sim (subscriber identity module), what this sim swap fraud looks like, and how you can avoid it here. sim swapping can be done remotely without needing physical access to your phone. it’s surprisingly easy for customer service agents to fall victim to social engineering attacks by hackers.
Comments are closed.