Introduction To Cyber Security Chapter 3 Quiz Answers 100 Correct Answers Cisco 2021 Netacad

Ccna Security Chapter 3 Quiz Pdf Radius Internet Protocols Explanation: a wireless router can be configured to not allow the ssid to be broadcast, but that configuration is not considered to be adequate security for a wireless network. Cisco – introduction to cybersecurity chapter 3 quiz exam answers 2021 question 1: which technology removes direct equipment and maintenance costs from the user for data backups?.
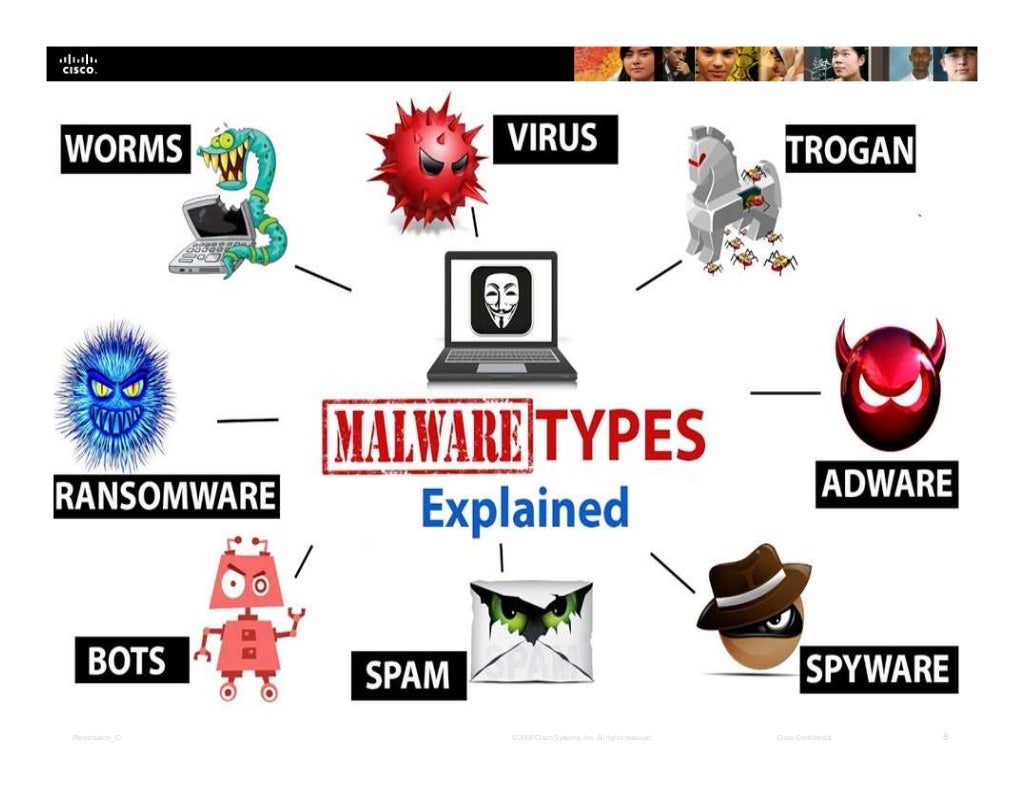
Cisco Cybersecurity Essentials Chapter 3 Which technology removes direct equipment and maintenance costs from the user for data backups? a user is surfing the internet using a laptop from a public wifi cafe. what should be checked first when the user connects to the public network?. Introduction to cybersecurity final quiz answers, 100% correct answers, cisco certified course 2021, cyber security free course with free certificate, networ. These answers are updated recently and are 100% correct answers of all week, assessment, and final exam answers of introduction to cybersecurity chapter 3 from cisco free certification course. Contribute to kmnaim cisco introduction to cybersecurity development by creating an account on github.

Solved Cis 135 Introduction To Cybersecurity Chapter 3 Chegg These answers are updated recently and are 100% correct answers of all week, assessment, and final exam answers of introduction to cybersecurity chapter 3 from cisco free certification course. Contribute to kmnaim cisco introduction to cybersecurity development by creating an account on github. Intro to cybersecurity quiz 3 a virus that attaches itself to an executable program can do anything that the program is permitted to do. (true or false). 3.1.2.5 lab – who owns your data? (answers). This quiz covers content from chapter 3 of an introduction to cybersecurity course. it contains 12 multiple choice questions to test knowledge of topics like password management, wireless security, cloud backups, iot risks, private browsing, and single sign on authentication. In this article, we will explore the common themes found in chapter 3 of "introduction to cybersecurity," what types of questions you might encounter in a quiz, and the rationale behind each topic covered.

Cybersecurity Essentials 1 1 Chapter 3 Quiz Docx Cybersecurity Essentials 1 1 Chapter 3 Quiz 1 Intro to cybersecurity quiz 3 a virus that attaches itself to an executable program can do anything that the program is permitted to do. (true or false). 3.1.2.5 lab – who owns your data? (answers). This quiz covers content from chapter 3 of an introduction to cybersecurity course. it contains 12 multiple choice questions to test knowledge of topics like password management, wireless security, cloud backups, iot risks, private browsing, and single sign on authentication. In this article, we will explore the common themes found in chapter 3 of "introduction to cybersecurity," what types of questions you might encounter in a quiz, and the rationale behind each topic covered.

Cisco Ccna Security Chapter 1 Exam Answers Pdf Denial Of Service Attack Computer Virus This quiz covers content from chapter 3 of an introduction to cybersecurity course. it contains 12 multiple choice questions to test knowledge of topics like password management, wireless security, cloud backups, iot risks, private browsing, and single sign on authentication. In this article, we will explore the common themes found in chapter 3 of "introduction to cybersecurity," what types of questions you might encounter in a quiz, and the rationale behind each topic covered.

Chapter 3 Pdf Computer Security Security
Comments are closed.