Windows Applocker Driver Elevation Of Privilege Cve 2024 21338 Nero22k S Blog

Windows Applocker Driver Elevation Of Privilege Cve 2024 21338 Nero22k S Blog On february 13th, 2024, during patch tuesday, microsoft security response center (msrc) disclosed an elevation of privilege vulnerability that was exploited in the wild by the lazarus hacking group. the group used this previously unknown vulnerability (zero day) in their attack to gain kernel access for their user mode rootkit. In depth analysis of cve 2024 21338, a windows kernel elevation of privileges vulnerability, its root cause, exploitation challenges and poc.

Windows Applocker Driver Elevation Of Privilege Cve 2024 21338 Nero22k S Blog In conclusion, the cve 2024 21338 vulnerability presents a significant elevation of privilege threat in windows systems, notably exploited by the lazarus group to bypass conventional security measures such as edrs and antiviruses. Tracked as cve 2024 21338, the security flaw was found by avast senior malware researcher jan vojtěšek in the appid.sys windows applocker driver and reported to microsoft last august as. Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. In this post, we'll break down what cve 2024 21338 is, how it works, and how attackers might exploit it, with code samples and references to original research. what is cve 2024 21338? cve 2024 21338 is an elevation of privilege vulnerability in the windows graphical subsystem driver, win32k.sys.

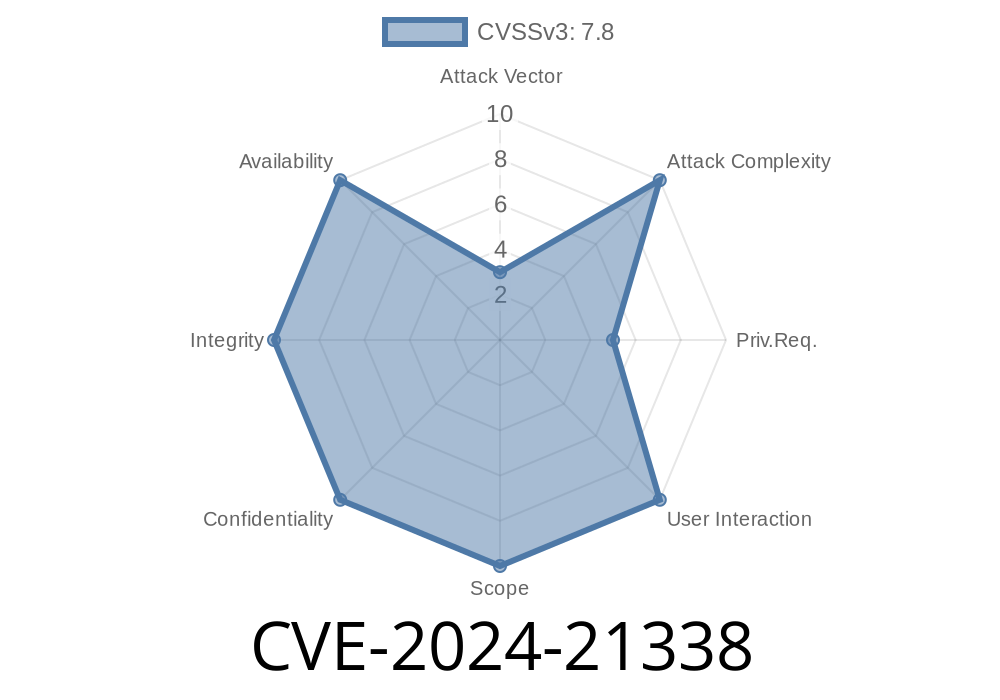
Windows Applocker Driver Elevation Of Privilege Cve 2024 21338 Nero22k S Blog Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. In this post, we'll break down what cve 2024 21338 is, how it works, and how attackers might exploit it, with code samples and references to original research. what is cve 2024 21338? cve 2024 21338 is an elevation of privilege vulnerability in the windows graphical subsystem driver, win32k.sys. Local privilege escalation from admin to kernel vulnerability on windows 10 and windows 11 operating systems with hvci enabled. use microsoft visual studio with the c package to successfully compile the poc on both release and debug modes. The vulnerability occurs at certain ioctl of “appid.sys” known as applocker ‘s driver, one of the windows feature. the threat actor can read and write on a random kernel memory by exploiting the vulnerability, and can either disable security products or gain system privilege. Understand the critical aspects of cve 2024 21338 with a detailed vulnerability assessment, exploitation potential, affected technologies, and remediation guidance. The vulnerability affects the ‘appid.sys’ driver associated with microsoft’s applocker security feature. exploitation of cve 2024 21338 allows for a fileless kernel attack. threat actors are then able to evade the detection mechanism and escalate privileges.

Windows Applocker Driver Elevation Of Privilege Cve 2024 21338 Nero22k S Blog Local privilege escalation from admin to kernel vulnerability on windows 10 and windows 11 operating systems with hvci enabled. use microsoft visual studio with the c package to successfully compile the poc on both release and debug modes. The vulnerability occurs at certain ioctl of “appid.sys” known as applocker ‘s driver, one of the windows feature. the threat actor can read and write on a random kernel memory by exploiting the vulnerability, and can either disable security products or gain system privilege. Understand the critical aspects of cve 2024 21338 with a detailed vulnerability assessment, exploitation potential, affected technologies, and remediation guidance. The vulnerability affects the ‘appid.sys’ driver associated with microsoft’s applocker security feature. exploitation of cve 2024 21338 allows for a fileless kernel attack. threat actors are then able to evade the detection mechanism and escalate privileges.

Windows Applocker Driver Elevation Of Privilege Cve 2024 21338 Nero22k S Blog Understand the critical aspects of cve 2024 21338 with a detailed vulnerability assessment, exploitation potential, affected technologies, and remediation guidance. The vulnerability affects the ‘appid.sys’ driver associated with microsoft’s applocker security feature. exploitation of cve 2024 21338 allows for a fileless kernel attack. threat actors are then able to evade the detection mechanism and escalate privileges.
Cve 2024 21338 Deep Dive Into The Windows Kernel Elevation Of Privilege Vulnerability
Comments are closed.