The Journey From Legacy To Cloud Native Security Principles With Craig Savage

Cloud Security Chapter Pdf Software As A Service Cloud Computing Most information security (infosec) teams have a good handle on the manner in which infosec is designed and managed for internal or monolithic applications,. Most information security (infosec) teams have a good handle on the manner in which infosec is designed and managed for internal or monolithic applications, but what about the cloud?.

Csa Uk Agm 2019 Craig Savage Safe As Clouds The Journey From Legacy To Cloud Native Security Organizations are transitioning from monolithic, legacy systems to agile, cloud native architectures to meet growing demands for scalability, flexibility, and innovation. however, this. In this interview, we highlight one such approach, where lincoln financial group transitioned its sizable legacy footprint to cloud within two years. This detailed blog explores the principles of cloud native, the core tenets driving its adoption, the benefits it brings to modern application development, and how organizations and developers can transition legacy systems into cloud native architectures. With cyberattacks growing in sophistication, enterprises across industries are recognizing that cloud native security is not just an option but a necessity.

Cloud Native Security Onug Onug This detailed blog explores the principles of cloud native, the core tenets driving its adoption, the benefits it brings to modern application development, and how organizations and developers can transition legacy systems into cloud native architectures. With cyberattacks growing in sophistication, enterprises across industries are recognizing that cloud native security is not just an option but a necessity. Continued automation of audit log analysis and correlation is of paramount importance to security teams, as cloud native architectures are capable of generating more granular audit con figuration and filtering than traditional legacy systems for workloads. Maintaining robust security and continuous monitoring remains essential regardless of your chosen approach. best practices help ensure the application remains resilient, safeguarded against threats, and aligned with performance expectations in a constantly evolving digital landscape. Adopting these principles is fundamental to building a robust security posture in the cloud native landscape. they provide a framework for making informed security decisions and integrating security seamlessly into your cloud journey. This blog post explores the shift from legacy pam systems, which focus on the network perimeter, to modern, cloud native pam systems that prioritize the identity perimeter.
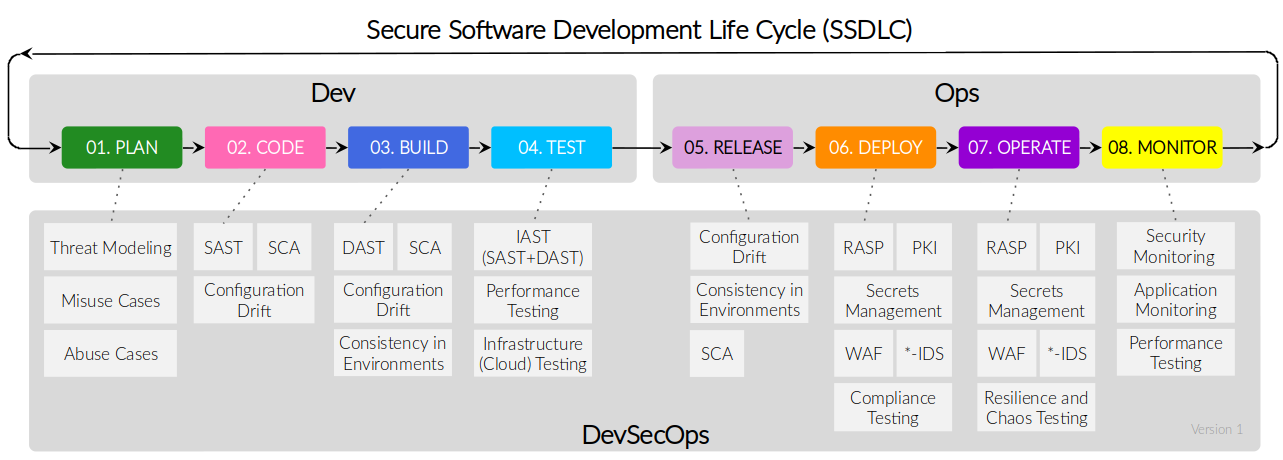
Security Cloud Native Workshop Workshop Cloud Native Security Continued automation of audit log analysis and correlation is of paramount importance to security teams, as cloud native architectures are capable of generating more granular audit con figuration and filtering than traditional legacy systems for workloads. Maintaining robust security and continuous monitoring remains essential regardless of your chosen approach. best practices help ensure the application remains resilient, safeguarded against threats, and aligned with performance expectations in a constantly evolving digital landscape. Adopting these principles is fundamental to building a robust security posture in the cloud native landscape. they provide a framework for making informed security decisions and integrating security seamlessly into your cloud journey. This blog post explores the shift from legacy pam systems, which focus on the network perimeter, to modern, cloud native pam systems that prioritize the identity perimeter.
Comments are closed.