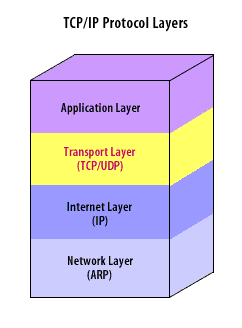
Transport Layer Udp And Tcp Network
Identify Transport Layer Tcp Udp JVM datagram sockets rely on the UDP transport layer protocol, while stream sockets use the TCP transport layer protocol As shown in Figure 10-19, pJava 118 provides support for the client and “SRT blends the resilience of TCP/IP transmission with the performance of UDP,” says Maag, “and adds in security, network-health monitoring, and simplified firewall traversal” The market approach for
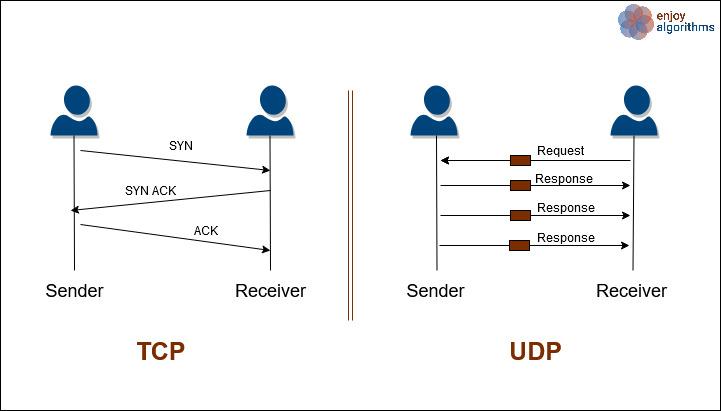
Networking Transport Layer Tcp Vs Udp Protocols RFC-908, dating from way back in 1984, is a good example Essentially, RDP (reliable data protocol) was proposed as a transport layer protocol; it was positioned in the stack as a peer to UDP and TCP IPv6 The current IP address scheme of 32-bit words is fast becoming inadequate It would appear that 2 32 = 4 294 967 296 combinations of addresses should be enough for everybody, but in practice this For a more detailed description of how TCP and UDP fit into the overall VoIP communications scheme, you might want to check out Tony’s tutorial presentation, “Transport Protocols for For example, BitTorrent now tries to run a protocol called LEDBAT (Low Extra Delay Background Transport) on top of UDP It's still reliable, it's still a bidirectional byte-stream, but it's not TCP

Configuration For Transport Layer Experiments Tcp Udp Download Scientific Diagram For a more detailed description of how TCP and UDP fit into the overall VoIP communications scheme, you might want to check out Tony’s tutorial presentation, “Transport Protocols for For example, BitTorrent now tries to run a protocol called LEDBAT (Low Extra Delay Background Transport) on top of UDP It's still reliable, it's still a bidirectional byte-stream, but it's not TCP Software implementations of UDP-based application protocols DNS, NTP, TFTP, Echo (RFC862), Chargen (RFC864), and QOTD (RFC865) were specifically found to be vulnerable to such network loops Click to enlarge The other type of traffic looked at (and this may be of some interest when troubleshooting network issues) is DNS traffic DNS uses port 53 and uses UDP for the transport layer
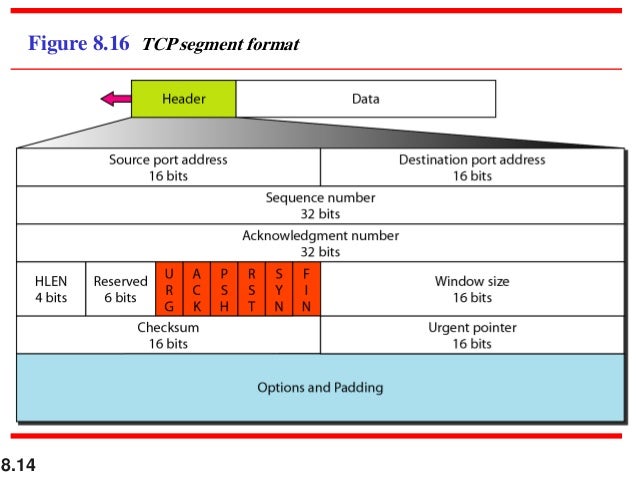
Transport Layer Udp And Tcp Network Software implementations of UDP-based application protocols DNS, NTP, TFTP, Echo (RFC862), Chargen (RFC864), and QOTD (RFC865) were specifically found to be vulnerable to such network loops Click to enlarge The other type of traffic looked at (and this may be of some interest when troubleshooting network issues) is DNS traffic DNS uses port 53 and uses UDP for the transport layer

Transport Layer And Protocols Tcp Udp
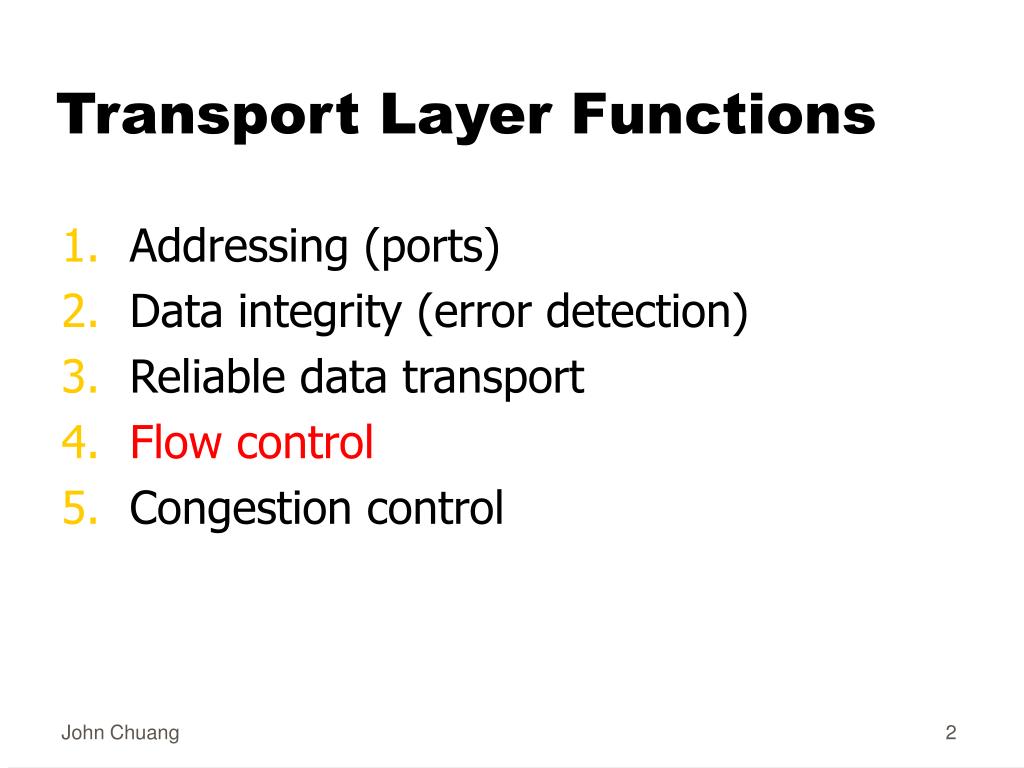
Ppt Transport Layer Tcp And Udp Powerpoint Presentation Free Download Id 3723650
Comments are closed.