Unprotected Infected How To Secure Your Tcp Ip Ports Page 3 Techradar
How To Secure Your Tcp Ip Ports Techradar Beyond staying up to date, the key to keeping your pc secure is to ensure that your firewall is closed to all traffic other than to the ports you know should be open. because some malicious. Close them off: closing the ports you don't need is a good place to start on the road to a secure pc. the tcp ip system running on the internet today uses a series of handshakes to ensure.
How To Secure Your Tcp Ip Ports Techradar Learn how to secure your open ports on your computer or network and protect yourself from cyber attacks. understand open ports: think of open ports as digital doorways into your computer or network. while necessary for certain services, they can be entry points for hackers if left unsecured. Open ports themselves are not inherently dangerous, but they can be exploited by hackers to gain unauthorized access to sensitive data. vulnerable, unpatched, misconfigured, or infected services running on open ports can provide an entry point for hackers to move through a network. Many tcp ip vulnerabilities from ip address spoofing to packet sequence prediction can lead to man in the middle or denial of service attacks. learn how to keep from falling victim. Cyber security; google; automotive; hobbies; science submenu. space; cutting edge; news; reviews; buying guides; deals; sign in; newsletter.
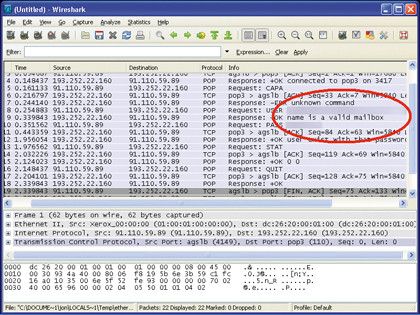
Tcp Ip S Vulnerabilities How To Secure Your Tcp Ip Ports Page 2 Techradar Many tcp ip vulnerabilities from ip address spoofing to packet sequence prediction can lead to man in the middle or denial of service attacks. learn how to keep from falling victim. Cyber security; google; automotive; hobbies; science submenu. space; cutting edge; news; reviews; buying guides; deals; sign in; newsletter. First, we need to know how to use nmap to scan for open ports. here’s a very brief overview: verify the installation by typing nmap v in the command line. for a basic port scan, use nmap
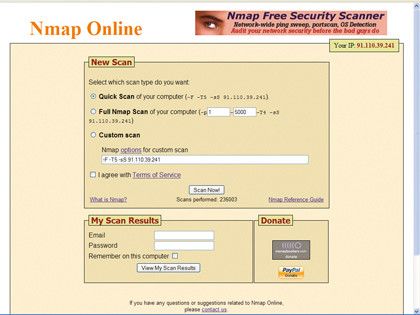
Unprotected Infected How To Secure Your Tcp Ip Ports Page 3 Techradar First, we need to know how to use nmap to scan for open ports. here’s a very brief overview: verify the installation by typing nmap v in the command line. for a basic port scan, use nmap

How To Check Open Tcp Ip Ports In Windows En Buradabiliyorum Com Using transport layer protocols such as transmission control protocol (tcp port) and user diagram protocol (udp), devices can exchange data across the internet. udp ports rely on a separate protocol, designed for faster data transfer, which can introduce risks if not secured properly. Unfortunately, tcp ip was conceived to send and receive data reliably, not to secure it. that's the job of the applications listening and sending on specific ports.
Comments are closed.