Vulnerability Management
Vulnerability Management Meaning Tools And Process Vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from cyberattacks and data breaches. What is vulnerability management? vulnerability management is the ongoing, regular process of identifying, assessing, reporting on, managing and remediating cyber vulnerabilities across endpoints, workloads, and systems.

What Is Vulnerability Management Microsoft defender vulnerability management uses a risk based approach to the discovery, prioritization, and remediation of endpoint vulnerabilities and misconfigurations. Vulnerability management is the process of identifying, assessing, remediating and mitigating security vulnerabilities in software and computer systems. it's a critical part of managing cybersecurity risk in it environments, as vulnerabilities that are not found and fixed can expose an organization to damaging cyberattacks and data breaches. Vulnerability management, a subdomain of it risk management, is the continuous discovery, prioritization and resolution of security vulnerabilities in an organization’s it infrastructure and software. Vulnerability management is the continuous process of identifying, assessing, prioritizing, and remediating vulnerabilities across an organization’s it infrastructure by leveraging threat intelligence and automation. this helps protect against cyberattacks while reducing overall risk exposure.

Vulnerability Management Vulnerability management, a subdomain of it risk management, is the continuous discovery, prioritization and resolution of security vulnerabilities in an organization’s it infrastructure and software. Vulnerability management is the continuous process of identifying, assessing, prioritizing, and remediating vulnerabilities across an organization’s it infrastructure by leveraging threat intelligence and automation. this helps protect against cyberattacks while reducing overall risk exposure. Vulnerability management mission: reduce the prevalence and impact of vulnerabilities and exploitable conditions across enterprises and technologies, including through assessments and coordinated disclosure of vulnerabilities reported by trusted partners. Vulnerability management is the "cyclical practice of identifying, classifying, prioritizing, remediating, and mitigating" software vulnerabilities. [1] vulnerability management is integral to computer security and network security, and must not be confused with vulnerability assessment. Vulnerability management is an important component of cybersecurity that allows organizations to identify, assess, prioritize, and eliminate security weaknesses before they harm your operations and steal data. Vulnerability management focuses on the systematic identification, classification, prioritization, and remediation of security weaknesses across an organization's digital landscape.

The Vulnerability Management Lifecycle 5 Steps Crowdstrike Vulnerability management mission: reduce the prevalence and impact of vulnerabilities and exploitable conditions across enterprises and technologies, including through assessments and coordinated disclosure of vulnerabilities reported by trusted partners. Vulnerability management is the "cyclical practice of identifying, classifying, prioritizing, remediating, and mitigating" software vulnerabilities. [1] vulnerability management is integral to computer security and network security, and must not be confused with vulnerability assessment. Vulnerability management is an important component of cybersecurity that allows organizations to identify, assess, prioritize, and eliminate security weaknesses before they harm your operations and steal data. Vulnerability management focuses on the systematic identification, classification, prioritization, and remediation of security weaknesses across an organization's digital landscape. Vulnerability management seeks to help organizations identify such weaknesses in its security posture so that they can be rectified before they are exploited by attackers. Vulnerability management is the process of continuously identifying, categorizing, and remediating technology system security vulnerabilities. vulnerability management is a critical component of maintaining security. Vulnerability management is a cybersecurity strategy that enables organizations to identify, prioritize and mitigate security risks across their it environment on an ongoing basis. without vulnerability management, businesses are susceptible to security attacks that can prove to be very costly. Join the upcoming tenable webinar titled “tenable announces ai powered breakthrough in vulnerability prioritization” on august 19, 2025 at 10 am bst and 11 am et. about tenable tenable® is the exposure management company, exposing and closing the cybersecurity gaps that erode business value, reputation and trust.

Vulnerability Management Frsecure Vulnerability management is an important component of cybersecurity that allows organizations to identify, assess, prioritize, and eliminate security weaknesses before they harm your operations and steal data. Vulnerability management focuses on the systematic identification, classification, prioritization, and remediation of security weaknesses across an organization's digital landscape. Vulnerability management seeks to help organizations identify such weaknesses in its security posture so that they can be rectified before they are exploited by attackers. Vulnerability management is the process of continuously identifying, categorizing, and remediating technology system security vulnerabilities. vulnerability management is a critical component of maintaining security. Vulnerability management is a cybersecurity strategy that enables organizations to identify, prioritize and mitigate security risks across their it environment on an ongoing basis. without vulnerability management, businesses are susceptible to security attacks that can prove to be very costly. Join the upcoming tenable webinar titled “tenable announces ai powered breakthrough in vulnerability prioritization” on august 19, 2025 at 10 am bst and 11 am et. about tenable tenable® is the exposure management company, exposing and closing the cybersecurity gaps that erode business value, reputation and trust. Vulnerability management proactively identifies, prioritizes, and fixes security weaknesses to reduce an organization’s exposure to threats. its goal is to lower the risks these vulnerabilities pose to an organization. Vulnerability management is an ongoing, systematic process of identifying, categorizing, prioritizing, and addressing risks to an organization’s it infrastructure. There are five main stages in the vulnerability management lifecycle include: assess, prioritize, act, reassess, improve. learn more here. Service teams use vulnerability scan results to validate security patch deployment on applicable system components. any overdue vulnerabilities are reported daily and reviewed by management monthly to measure the breadth and depth of patch coverage across the environment and hold ourselves accountable for timely patching.

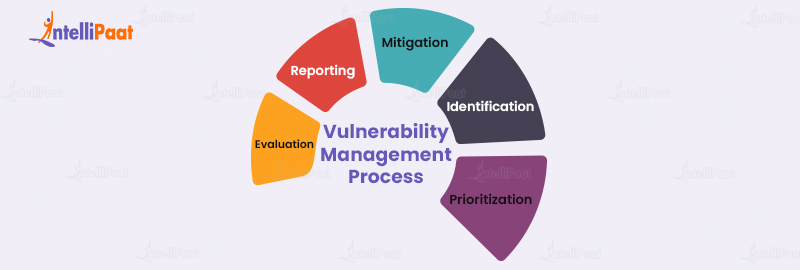
Vulnerability Management Vulnerability management seeks to help organizations identify such weaknesses in its security posture so that they can be rectified before they are exploited by attackers. Vulnerability management is the process of continuously identifying, categorizing, and remediating technology system security vulnerabilities. vulnerability management is a critical component of maintaining security. Vulnerability management is a cybersecurity strategy that enables organizations to identify, prioritize and mitigate security risks across their it environment on an ongoing basis. without vulnerability management, businesses are susceptible to security attacks that can prove to be very costly. Join the upcoming tenable webinar titled “tenable announces ai powered breakthrough in vulnerability prioritization” on august 19, 2025 at 10 am bst and 11 am et. about tenable tenable® is the exposure management company, exposing and closing the cybersecurity gaps that erode business value, reputation and trust. Vulnerability management proactively identifies, prioritizes, and fixes security weaknesses to reduce an organization’s exposure to threats. its goal is to lower the risks these vulnerabilities pose to an organization. Vulnerability management is an ongoing, systematic process of identifying, categorizing, prioritizing, and addressing risks to an organization’s it infrastructure. There are five main stages in the vulnerability management lifecycle include: assess, prioritize, act, reassess, improve. learn more here. Service teams use vulnerability scan results to validate security patch deployment on applicable system components. any overdue vulnerabilities are reported daily and reviewed by management monthly to measure the breadth and depth of patch coverage across the environment and hold ourselves accountable for timely patching. Vulnerability management (vm) is the process of identifying and assessing vulnerabilities, reporting on them, and managing or mitigating them. the process covers an organization's endpoints, systems, and workloads. Vulnerability management is defined as a proactive approach to identify, manage, and mitigate network vulnerabilities to improve the security of enterprise applications, software, and devices. Discover how ctem, vm, and asm work together to enhance cybersecurity, providing real time visibility and proactive threat management. Vulnerability management identifies and mitigates cyber exposure risks, securing an organization's infrastructure and resources across various technologies.
Comments are closed.