Vulnerability Management Best Practices For Strong Security

Guide To Vulnerability Management 1668341881 Pdf Security Computer Security Explore top 10 threat and vulnerability management best practices to detect, assess, and prevent attacks while strengthening security with smart processes. Discover best practices for effective vulnerability management. learn how to identify, assess, and remediate security gaps to boost resilience and compliance.

Vulnerability Management Strategies Types And Tools Effective vulnerability management includes using tools and techniques to monitor systems, perform regular assessments, and apply timely updates and patches to reduce risks. it involves continuous monitoring and improvement to maintain security posture against evolving threats. • identifies and describes key practices for vulnerability analysis and resolution and vulnerability management • provides examples and guidance to organizations wishing to implement these practices. Over the past several months, i spoke to a dozen security executives to find out. while i have pages and pages of written notes on the subject, their answers boiled down to 10 best practices . When designing and implementing a vulnerability management process, consider the following best practices. #1. perform regular vulnerability scans. vulnerability scanners are automated tools used to identify potential vulnerabilities and other security risks within an application.
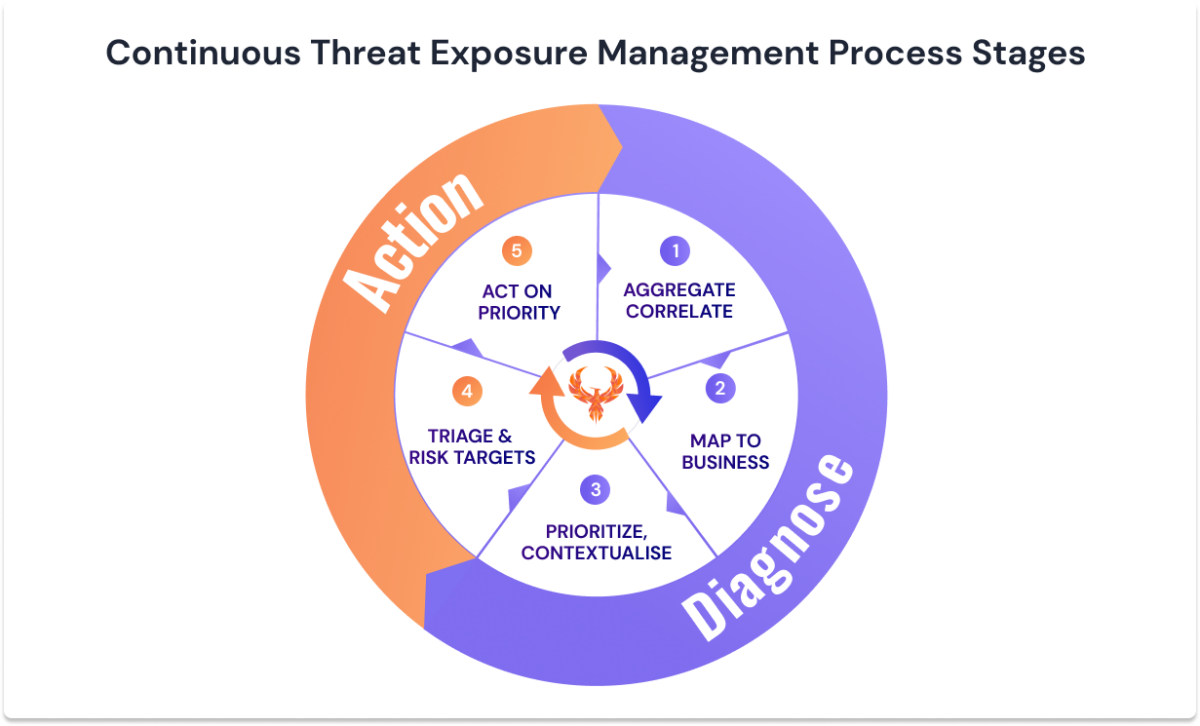
Vulnerability Management Strategies Types And Tools Over the past several months, i spoke to a dozen security executives to find out. while i have pages and pages of written notes on the subject, their answers boiled down to 10 best practices . When designing and implementing a vulnerability management process, consider the following best practices. #1. perform regular vulnerability scans. vulnerability scanners are automated tools used to identify potential vulnerabilities and other security risks within an application. The guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification scanning phase, the reporting phase, and remediation phase. Employing a robust vulnerability management process is one way to rectify the situation. a typical vulnerability management process features a five step lifecycle: discover, prioritize, remediate, validate, and report. Learn top vulnerability management, scanning, and remediation best practices to protect your systems and reduce security risks effectively. read today!. Learn essential vulnerability management best practices to reduce noise, assign ownership, and fix real risks faster. discover devocean.
Comments are closed.