Vulnerability Management Lifecycle Remediating Threats Patch Management
What Is Vulnerability Management Lifecycle Scan On Computer Explore the vulnerability management lifecycle, from discovery to remediation. learn its five key steps, challenges, and best practices for cybersecurity. The vulnerability management lifecycle has six key phases. organizations looking to implement or improve their vulnerability management program can follow these steps.
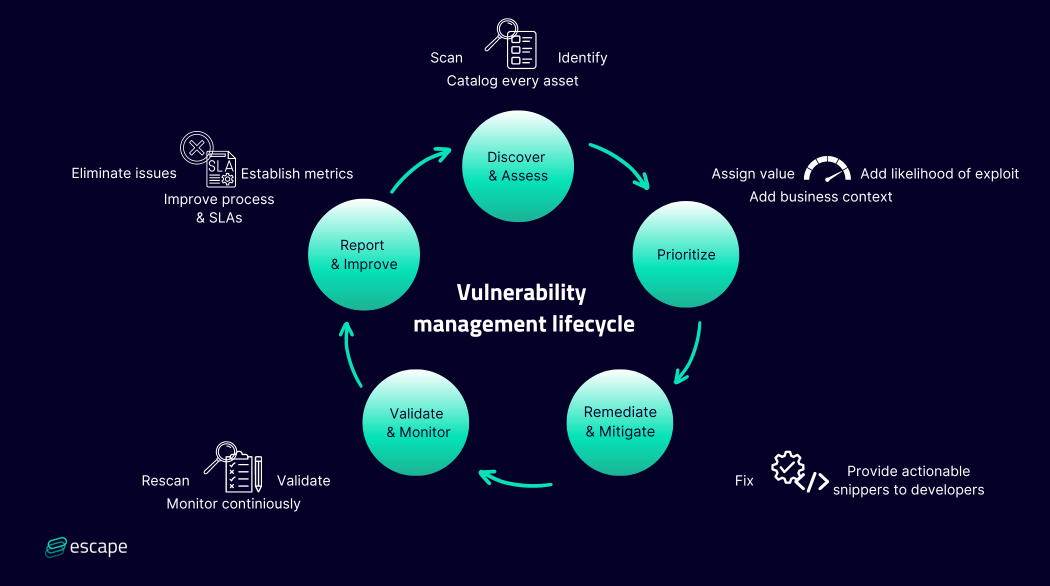
Vulnerability Management Lifecycle A Comprehensive Guide A more consistent vulnerability management process: the vulnerability management lifecycle gives security teams a repeatable process to follow, from vulnerability discovery to remediation and beyond. Moving from reactive patching to a structured vulnerability management lifecycle transforms security from tactical firefighting to strategic resilience engineering. There are five main stages in the vulnerability management lifecycle include: assess, prioritize, act, reassess, improve. learn more here. Compare patch management vs. vulnerability management and learn why it's important to have dedicated software and processes to manage both.

Patch Management Vs Vulnerability Management Syncro There are five main stages in the vulnerability management lifecycle include: assess, prioritize, act, reassess, improve. learn more here. Compare patch management vs. vulnerability management and learn why it's important to have dedicated software and processes to manage both. The guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification scanning phase, the reporting phase, and remediation phase. Vulnerability management covers the complete cycle of identifying, classifying, analyzing and mitigating security vulnerabilities in an organization’s it environment (computer systems, devices, applications), with the end goal of closing security gaps and reducing cyber risk. Our vulnerability management services help organizations stay ahead of evolving threats through continuous scanning and risk assessment. we prioritize vulnerabilities using real time threat intelligence, enabling efficient remediation and patch management. What is vulnerability management lifecycle? the vulnerability management lifecycle is the key process for finding and remediating security weaknesses before they are exploited. policy definition, assessment, shielding, mitigation and monitoring are required.

Vulnerability Patch Management Ridge It Cyber The guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification scanning phase, the reporting phase, and remediation phase. Vulnerability management covers the complete cycle of identifying, classifying, analyzing and mitigating security vulnerabilities in an organization’s it environment (computer systems, devices, applications), with the end goal of closing security gaps and reducing cyber risk. Our vulnerability management services help organizations stay ahead of evolving threats through continuous scanning and risk assessment. we prioritize vulnerabilities using real time threat intelligence, enabling efficient remediation and patch management. What is vulnerability management lifecycle? the vulnerability management lifecycle is the key process for finding and remediating security weaknesses before they are exploited. policy definition, assessment, shielding, mitigation and monitoring are required.
The Vulnerability Management Lifecycle In 6 Stages Wiz Our vulnerability management services help organizations stay ahead of evolving threats through continuous scanning and risk assessment. we prioritize vulnerabilities using real time threat intelligence, enabling efficient remediation and patch management. What is vulnerability management lifecycle? the vulnerability management lifecycle is the key process for finding and remediating security weaknesses before they are exploited. policy definition, assessment, shielding, mitigation and monitoring are required.
Comments are closed.