What Is A Ddos Attack The Complete Guide

Ddos Quick Guide Pdf Denial Of Service Attack Proxy Server This comprehensive guide delves into the intricacies of ddos attacks, their mechanisms, common types, and effective mitigation strategies, empowering enterprise businesses to safeguard their online presence. Distributed denial of service attacks are a way of attacking online infrastructure, including websites and online applications, by overwhelming the host servers. this prevents legitimate users from accessing the services.

Ddos Quick Guide Pdf Denial Of Service Attack Computer Network Ddos attacks are a primary concern in internet security today. explore details about how ddos attacks function, and how they can be stopped. Ddos (distributed denial of service) attack is an attempt to overload and disrupt the normal functioning of a server, service, or network by overwhelming it with traffic from multiple sources. This guide breaks down what a ddos attack is, how it works, and how to protect against it, with real world examples and prevention tips tailored for beginners and professionals alike. whether you’re in nepal or globally, understanding ddos attacks is crucial for staying secure online. How does a ddos attack work? a ddos attack is when many hacked computers are used to send traffic to a website or server, making it difficult for the site or server to function. this can be done by remotely controlling these computers using a botnet, which is a collection of bots.

What Is Ddos Attack Tpoint Tech Denial Of Service Attack Ddos Attack Cybersecurity Infographic This guide breaks down what a ddos attack is, how it works, and how to protect against it, with real world examples and prevention tips tailored for beginners and professionals alike. whether you’re in nepal or globally, understanding ddos attacks is crucial for staying secure online. How does a ddos attack work? a ddos attack is when many hacked computers are used to send traffic to a website or server, making it difficult for the site or server to function. this can be done by remotely controlling these computers using a botnet, which is a collection of bots. Distributed denial of service (ddos) is a type of dos attack where multiple systems, which are trojan infected, target a particular system which causes a dos attack. a ddos attack uses multiple servers and internet connections to flood the targeted resource. a ddos attack is one of the most powerful weapons on the cyber platform. A distributed denial of service attack is a subcategory of the more general denial of service (dos) attack. in a dos attack, the attacker uses a single internet connection to barrage a target with fake requests or to try and exploit a cybersecurity vulnerability. Distributed denial of service (ddos) attacks remain a severe cyberthreat to businesses and organizations as increasing volumes continue disrupting operations. this comprehensive overview chronicles the inner workings of the 16 most common ddos vectors that security teams defend against daily. During a ddos attack, a series of bots, or botnet, floods a website or service with http requests and traffic. essentially, multiple computers storm one computer during an attack, pushing out legitimate users. as a result, service can be delayed or otherwise disrupted for a length of time.

Guide To Ddos Attacks November 2017 Pdf Denial Of Service Attack Transmission Control Protocol Distributed denial of service (ddos) is a type of dos attack where multiple systems, which are trojan infected, target a particular system which causes a dos attack. a ddos attack uses multiple servers and internet connections to flood the targeted resource. a ddos attack is one of the most powerful weapons on the cyber platform. A distributed denial of service attack is a subcategory of the more general denial of service (dos) attack. in a dos attack, the attacker uses a single internet connection to barrage a target with fake requests or to try and exploit a cybersecurity vulnerability. Distributed denial of service (ddos) attacks remain a severe cyberthreat to businesses and organizations as increasing volumes continue disrupting operations. this comprehensive overview chronicles the inner workings of the 16 most common ddos vectors that security teams defend against daily. During a ddos attack, a series of bots, or botnet, floods a website or service with http requests and traffic. essentially, multiple computers storm one computer during an attack, pushing out legitimate users. as a result, service can be delayed or otherwise disrupted for a length of time.

Introduction To Ddos Attacks Pdf Denial Of Service Attack Amazon Web Services Distributed denial of service (ddos) attacks remain a severe cyberthreat to businesses and organizations as increasing volumes continue disrupting operations. this comprehensive overview chronicles the inner workings of the 16 most common ddos vectors that security teams defend against daily. During a ddos attack, a series of bots, or botnet, floods a website or service with http requests and traffic. essentially, multiple computers storm one computer during an attack, pushing out legitimate users. as a result, service can be delayed or otherwise disrupted for a length of time.
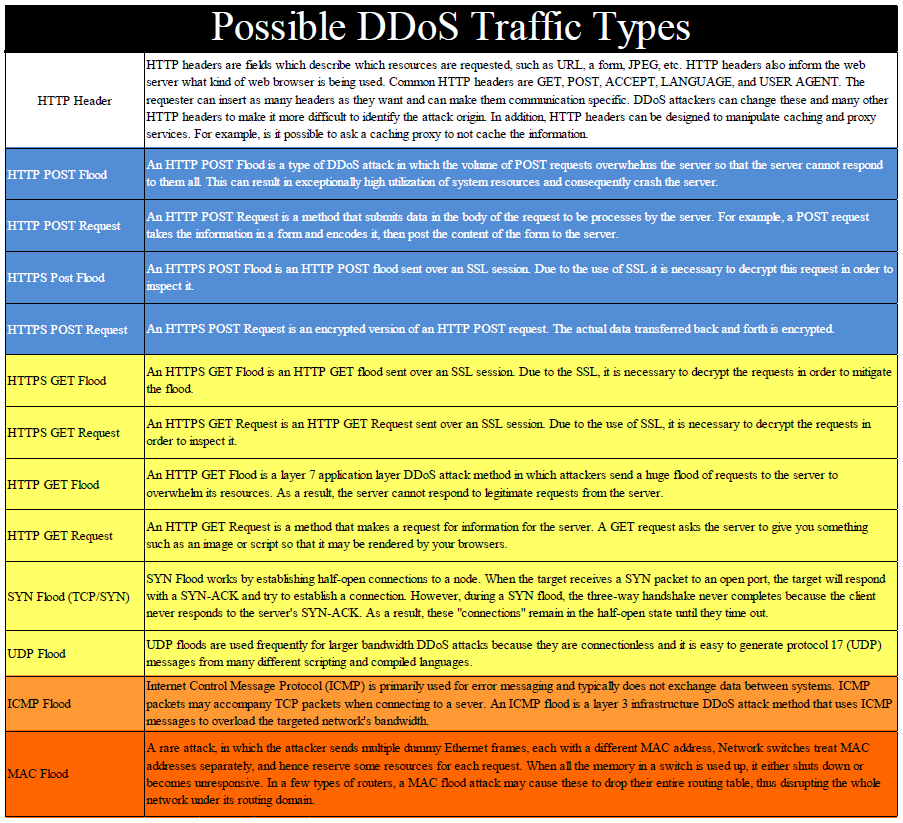
Dhs National Cybersecurity And Communications Integration Center Ddos Quick Guide Public
Comments are closed.