What Is An Intrusion Detection System Type Of Ids Intrusion Detection System Ids
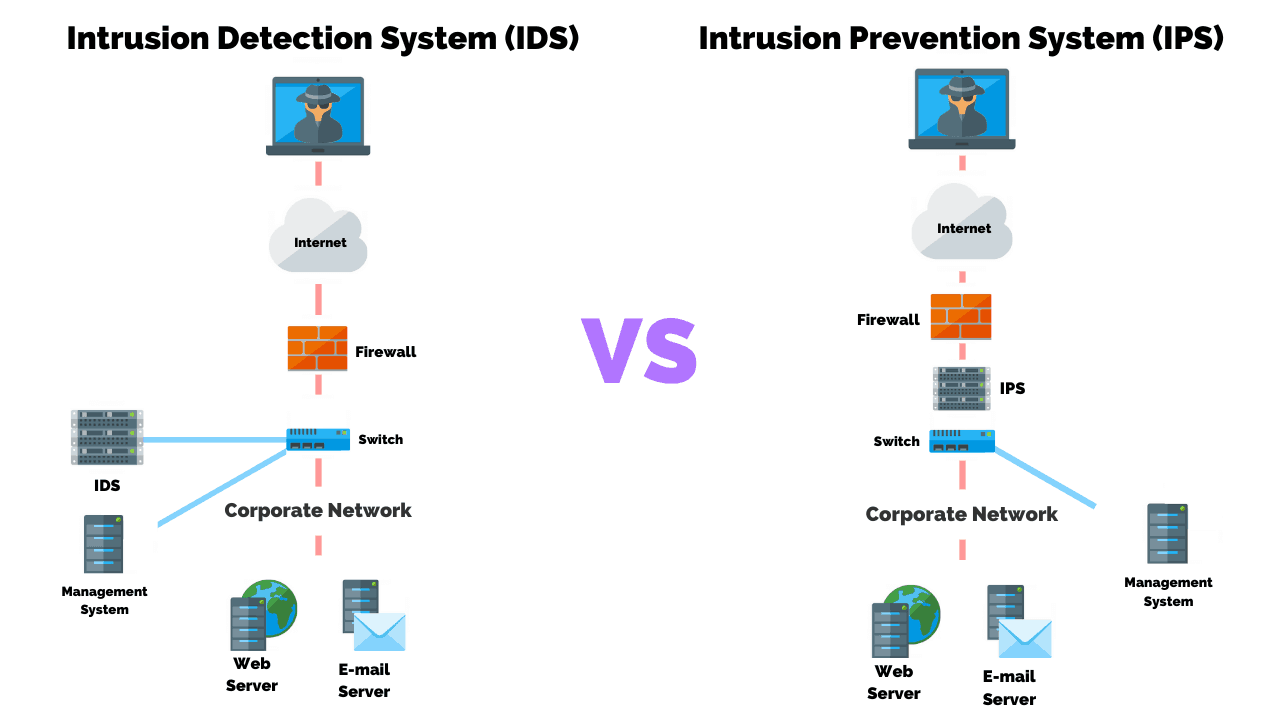
Intrusion Detection Vs Prevention Systems What S The Difference Intrusion detection system (ids) observes network traffic for malicious transactions and sends immediate alerts when it is observed. it is software that checks a network or system for malicious activities or policy violations. What is an ids? an intrusion detection system (ids) is a network security tool that monitors network traffic and devices for known malicious activity, suspicious activity or security policy violations.
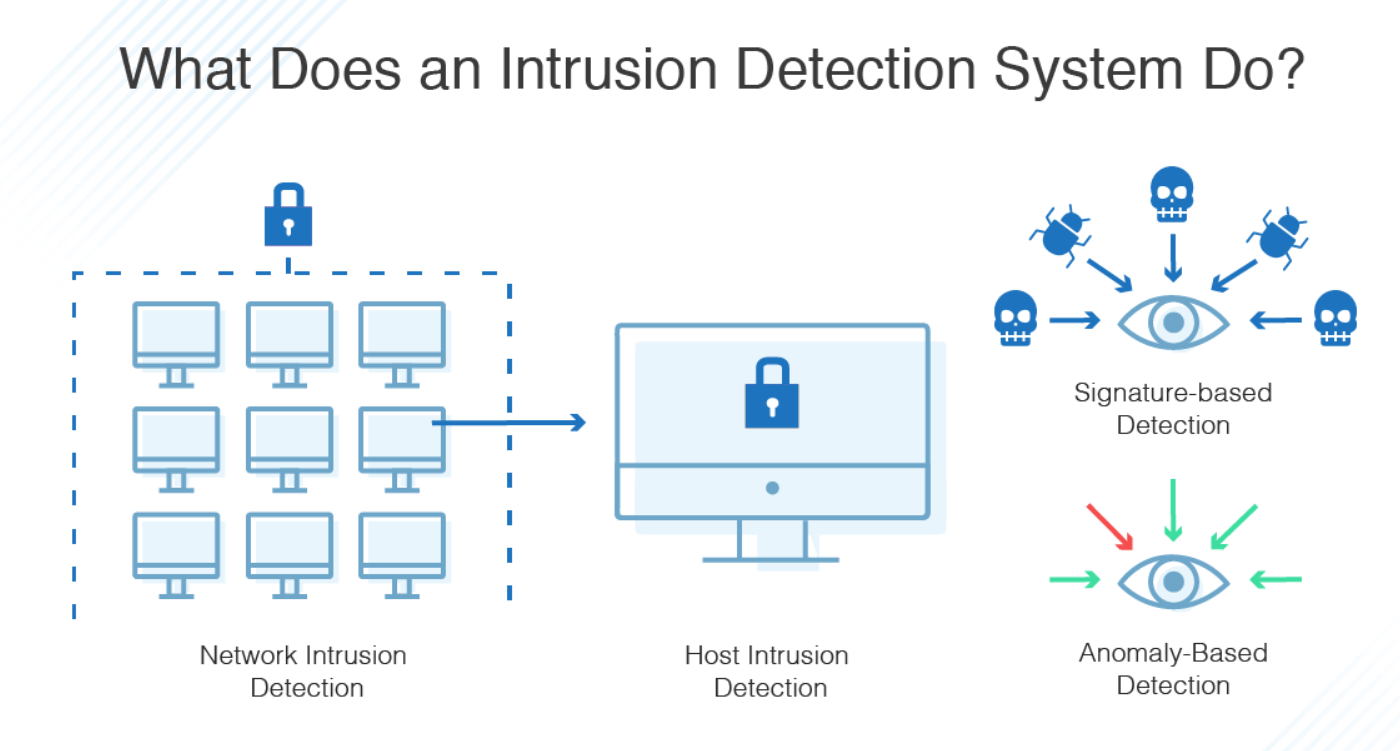
Ids Intrusion Detection System Network intrusion detection systems are used to detect suspicious activity to catch hackers before damage is done to the network. there are network based and host based intrusion detection systems. host based idses are installed on client computers; network based idses are on the network itself. One of these essential tools is an intrusion detection system (ids), which allows companies to identify security breaches in an instant so that they can create a response plan to respond to an attack. An intrusion detection system (ids) monitors network traffic or host activity to identify suspicious patterns, anomalies, or known attack signatures. it continuously analyzes data to detect signs of intrusions or policy violations. Intrusion detection systems are primarily categorized into two main types: network based ids (nids) and host based ids (hids). nids can detect threats at the network perimeter, while hids can identify threats that have already infiltrated the network and are operating on individual devices.

Ids Intrusion Detection System Acronym Technology Concept Background Stock Illustration An intrusion detection system (ids) monitors network traffic or host activity to identify suspicious patterns, anomalies, or known attack signatures. it continuously analyzes data to detect signs of intrusions or policy violations. Intrusion detection systems are primarily categorized into two main types: network based ids (nids) and host based ids (hids). nids can detect threats at the network perimeter, while hids can identify threats that have already infiltrated the network and are operating on individual devices. What is an intrusion detection system (ids)? an intrusion detection system is a network of security devices designed to observe access points for unusual activities and intrusion events. Unlike firewalls that block traffic, ids tools alert analysts to suspicious behavior—supporting threat detection, compliance, and investigation. ids tools remain a foundational element of layered network defense, even though they may not directly stop attacks alone. Ids, short for intrusion detection system, is a network security technology designed to monitor network traffic and detect suspicious or malicious activity. simply put, it acts as your first line of defense, keeping an eye out for unauthorized attempts to access or compromise your systems. There are several types of intrusion detection systems (ids), each designed to protect different aspects of a network or host system. the two most common types of ids are: host based intrusion detection system (hids) monitors activity on a specific device or host, such as a server or workstation.

Intrusion Detection System Ids In Cyber Security What is an intrusion detection system (ids)? an intrusion detection system is a network of security devices designed to observe access points for unusual activities and intrusion events. Unlike firewalls that block traffic, ids tools alert analysts to suspicious behavior—supporting threat detection, compliance, and investigation. ids tools remain a foundational element of layered network defense, even though they may not directly stop attacks alone. Ids, short for intrusion detection system, is a network security technology designed to monitor network traffic and detect suspicious or malicious activity. simply put, it acts as your first line of defense, keeping an eye out for unauthorized attempts to access or compromise your systems. There are several types of intrusion detection systems (ids), each designed to protect different aspects of a network or host system. the two most common types of ids are: host based intrusion detection system (hids) monitors activity on a specific device or host, such as a server or workstation.
Intrusion Detection System Ids Vs Intrusion Prevention System Ips Ids, short for intrusion detection system, is a network security technology designed to monitor network traffic and detect suspicious or malicious activity. simply put, it acts as your first line of defense, keeping an eye out for unauthorized attempts to access or compromise your systems. There are several types of intrusion detection systems (ids), each designed to protect different aspects of a network or host system. the two most common types of ids are: host based intrusion detection system (hids) monitors activity on a specific device or host, such as a server or workstation.
Comments are closed.