What Is Intrusion Detection System Ids Working Types Best Tools
.jpg)
Types Of Intrusion Detection System Ids We'll show you the best network intrusion detection software & tools for the job. an intrusion detection system (ids) monitors network traffic for unusual or suspicious activity and sends an alert to the administrator. Hids and nids are the two types that are based on how the market is segmented. services that the ids market can be categorized into are managed services, design and integration services, consultancy services, and training & education.

Instrumentation Tools On Linkedin Intrusion Detection System Ids And Intrusion Prevention Intrusion detection system (ids) observes network traffic for malicious transactions and sends immediate alerts when it is observed. it is software that checks a network or system for malicious activities or policy violations. Ids solutions come in a range of different types and varying capabilities. common types of intrusion detection systems (ids) include: network intrusion detection system (nids): a nids solution is deployed at strategic points within an organization’s network to monitor incoming and outgoing traffic. We examine the top six tools, explain the different approaches and form factors used, and compare how intrusion prevention fits into the overall security marketplace. An intrusion detection system (ids) is a key component of modern cybersecurity architecture. by continuously monitoring and analyzing network or system activity, ids provides numerous benefits that enhance threat detection, incident response, and compliance.
Five Major Types Of Intrusion Detection System Ids We examine the top six tools, explain the different approaches and form factors used, and compare how intrusion prevention fits into the overall security marketplace. An intrusion detection system (ids) is a key component of modern cybersecurity architecture. by continuously monitoring and analyzing network or system activity, ids provides numerous benefits that enhance threat detection, incident response, and compliance. Intrusion detection systems (ids) are critical security tools that monitor network or host activity for malicious actions or policy violations, enabling organizations to detect and respond to potential threats in real time. An intrusion detection system (ids) is a software application or hardware device that detects vulnerability exploits, malicious activity, or policy violations. idss place sensors on network devices like firewalls, servers, and routers, or at a host level. Learn everything you need to know about intrusion detection systems. discover the meaning of ids, different types of systems, key considerations & more. Ids operates at the monitoring and detection layer, sitting between perimeter security (firewalls, vpns) and reactive tools like siem or soar. it passively observes traffic or system logs, without interfering with data flows—unlike an ips, which actively blocks threats.
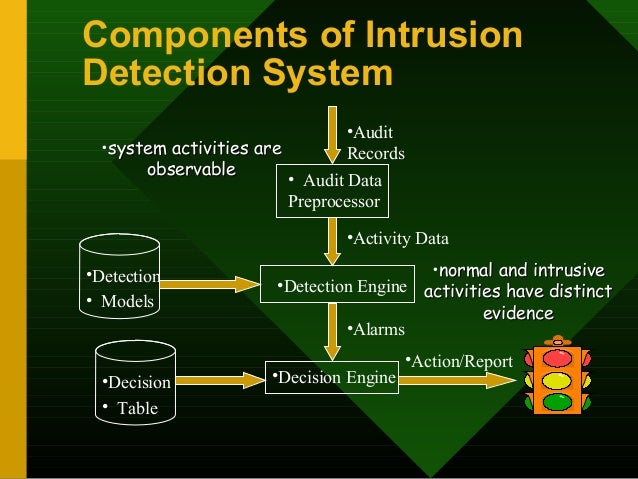
Intrusion Detection System Ids Intrusion detection systems (ids) are critical security tools that monitor network or host activity for malicious actions or policy violations, enabling organizations to detect and respond to potential threats in real time. An intrusion detection system (ids) is a software application or hardware device that detects vulnerability exploits, malicious activity, or policy violations. idss place sensors on network devices like firewalls, servers, and routers, or at a host level. Learn everything you need to know about intrusion detection systems. discover the meaning of ids, different types of systems, key considerations & more. Ids operates at the monitoring and detection layer, sitting between perimeter security (firewalls, vpns) and reactive tools like siem or soar. it passively observes traffic or system logs, without interfering with data flows—unlike an ips, which actively blocks threats.

Five Major Types Of Intrusion Detection System Ids Learn everything you need to know about intrusion detection systems. discover the meaning of ids, different types of systems, key considerations & more. Ids operates at the monitoring and detection layer, sitting between perimeter security (firewalls, vpns) and reactive tools like siem or soar. it passively observes traffic or system logs, without interfering with data flows—unlike an ips, which actively blocks threats.

Five Major Types Of Intrusion Detection System Ids
Comments are closed.