Why Regular Cloud Security Checks Are A Must

Cloud Security Checklist 221216 134458 Pdf Cloud Computing Securities Essential skills and responsibilities of a cloud security engineer. learn how this role is crucial in safeguarding your cloud infrastructure from cyber threats. Without a standardized cloud security checklist, gaps in configuration, access control, and data security can go unnoticed, increasing the risk of security incidents and regulatory non compliance.

The Importance Of Regular Cloud Security Audits From ensuring proper encryption, and monitoring access, to maintaining compliance, this checklist keeps your cloud environment resilient and compliant with emerging threats. without it, your business risks falling victim to easily avoidable security lapses. A well structured cloud security checklist can help teams proactively identify vulnerabilities and implement effective safeguards. this guide explores what cloud security entails, why a checklist is essential, and how to implement best practices effectively. Effective cloud security not only helps reduce risks and maintain regulatory compliance, it also improves operational resilience, fosters innovation, and builds trust with customers. choosing the right cloud security solution is essential. Aligning security checks with it changes is crucial to reduce vulnerabilities and safeguard digital assets, especially as it environments evolve frequently.
Cloud Security Let S Tech It Easy Effective cloud security not only helps reduce risks and maintain regulatory compliance, it also improves operational resilience, fosters innovation, and builds trust with customers. choosing the right cloud security solution is essential. Aligning security checks with it changes is crucial to reduce vulnerabilities and safeguard digital assets, especially as it environments evolve frequently. Regular security audits are essential to maintain visibility and control over rapidly evolving cloud ecosystems. key reasons why cloud security audits matter: evolving threat landscape: cyberattacks targeting cloud environments increased by 48% in 2023 alone. Strong passwords, multi factor authentication, data encryption, and proper access control are just a few of the critical practices every user must follow to secure their cloud based resources. as the digital landscape evolves, so too must our approach to cloud security. Regular assessments ensure your cloud setup follows industry standards and best practices. “misconfigurations and weak access controls contribute to cloud security vulnerabilities. regularly review and update your security settings to reduce these risks.” – danny tehrani, ceo of computers made easy. Audits are key for spotting deviations from established baselines by helping organizations identify unauthorized changes or misconfigurations that could lead to security risks. regularly identifying these deviations ensures that systems are secure, compliant, and optimized.

Cloud Security Validation Regular security audits are essential to maintain visibility and control over rapidly evolving cloud ecosystems. key reasons why cloud security audits matter: evolving threat landscape: cyberattacks targeting cloud environments increased by 48% in 2023 alone. Strong passwords, multi factor authentication, data encryption, and proper access control are just a few of the critical practices every user must follow to secure their cloud based resources. as the digital landscape evolves, so too must our approach to cloud security. Regular assessments ensure your cloud setup follows industry standards and best practices. “misconfigurations and weak access controls contribute to cloud security vulnerabilities. regularly review and update your security settings to reduce these risks.” – danny tehrani, ceo of computers made easy. Audits are key for spotting deviations from established baselines by helping organizations identify unauthorized changes or misconfigurations that could lead to security risks. regularly identifying these deviations ensures that systems are secure, compliant, and optimized.

Security In Cloud Computing How To Master It In 2024 Regular assessments ensure your cloud setup follows industry standards and best practices. “misconfigurations and weak access controls contribute to cloud security vulnerabilities. regularly review and update your security settings to reduce these risks.” – danny tehrani, ceo of computers made easy. Audits are key for spotting deviations from established baselines by helping organizations identify unauthorized changes or misconfigurations that could lead to security risks. regularly identifying these deviations ensures that systems are secure, compliant, and optimized.
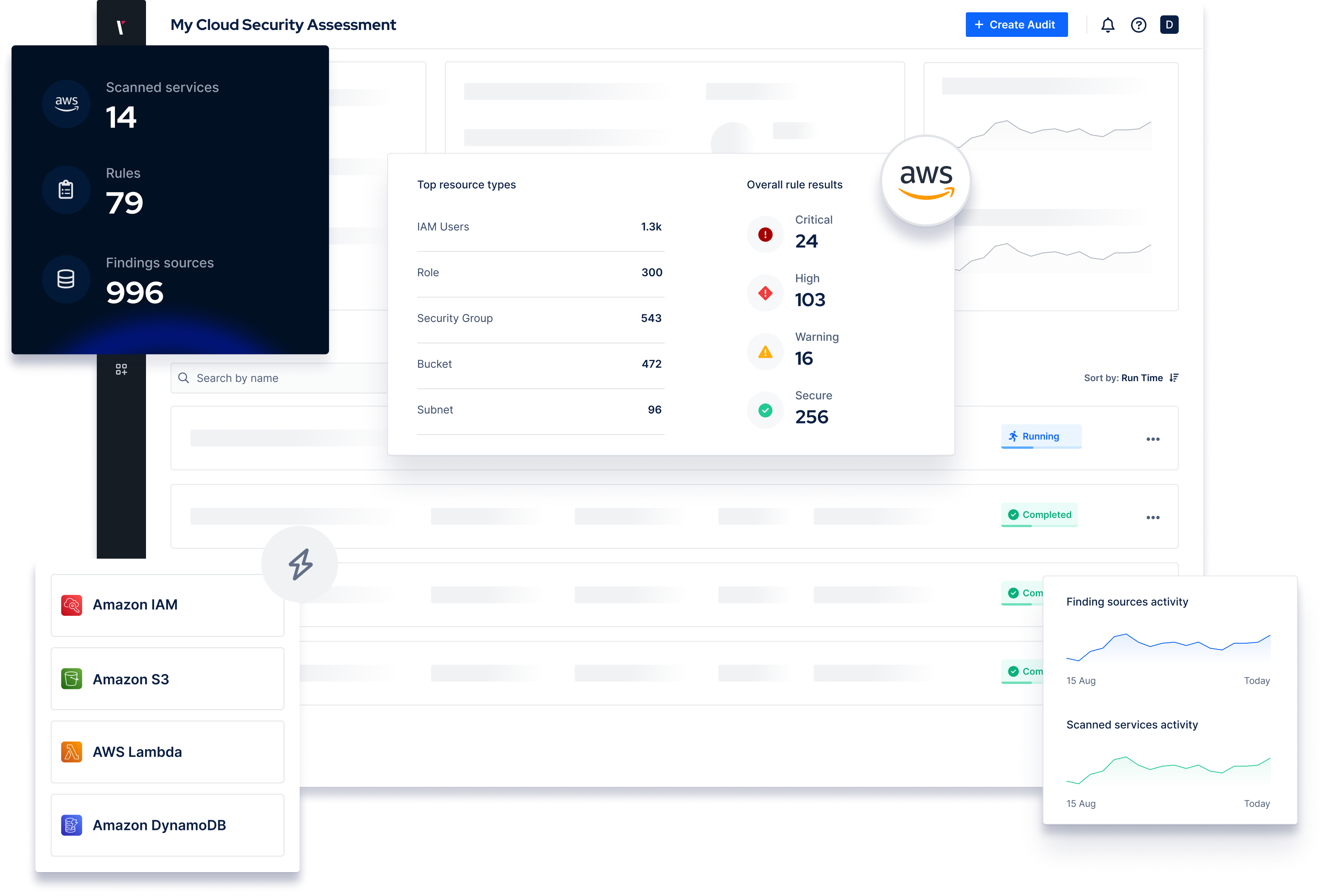
Security Control Validation
Comments are closed.