Xss Bug Bounty Learn Cross Site Scripting For Bounties
Exploiting Cross Site Scripting Xss Vulnerabilities For Bug Bounty Portswigger 2024 Hacklido Learn about cross site scripting (xss) on bugbountyhunter and test your skills against our challenges. For github we set content security policy (csp) http headers to prevent the execution of arbitrary javascript within the github domain. additionally, we set the x xss protection header to instruct the browsers to activate proactive xss mitigation.

Cross Site Scripting Xss Github Bug Bounty As a bug bounty hunter or security researcher, understanding various xss techniques is crucial for identifying and exploiting these vulnerabilities. in this article, we’ll explore ten xss. Cross site scripting (xss) attacks are a type of injection, where malicious contents are injected into in any case harmless, and confided in sites. xss attacks happen when an attacker utilizes a web application to send noxious malicious code, by and large as program side content, to an alternate end client. Cross site scripting (xss) is a type of security vulnerability that allows attackers to inject malicious code, usually in the form of scripts, into web applications. this can lead to a wide range of harmful consequences, such as stealing sensitive data, defacing websites, or spreading malware. The point of this article is not to teach you about hacking, but to get you started with bug bounty. learning how to hack is going to require that you start looking into resources (link here). the next step for you is to start learning about what vulnerabilities exist and how to find them.
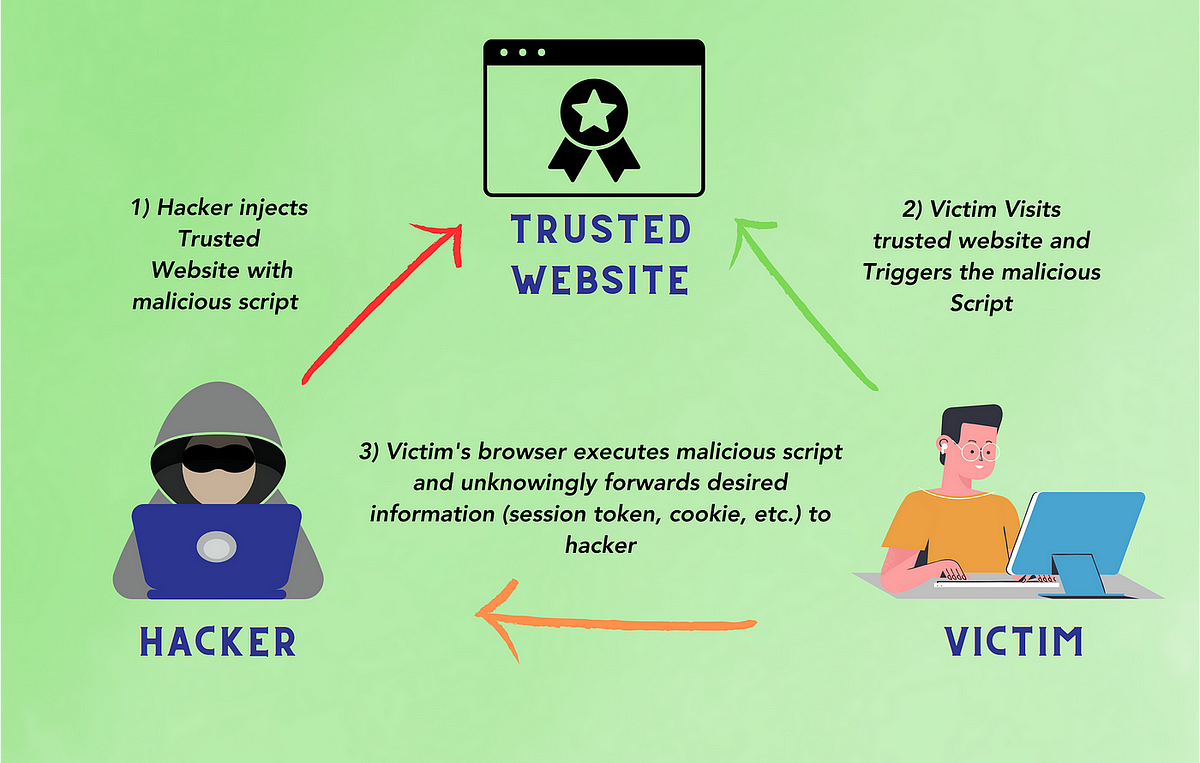
Cross Site Scripting Xss Vulnerabilities Automation Scanner For Bug Bounty By Cross site scripting (xss) is a type of security vulnerability that allows attackers to inject malicious code, usually in the form of scripts, into web applications. this can lead to a wide range of harmful consequences, such as stealing sensitive data, defacing websites, or spreading malware. The point of this article is not to teach you about hacking, but to get you started with bug bounty. learning how to hack is going to require that you start looking into resources (link here). the next step for you is to start learning about what vulnerabilities exist and how to find them. If you’re diving into the world of bug bounty hunting or ethical hacking, there’s one vulnerability you must master: cross site scripting (xss). it’s everywhere — and if you know how to. This cross site scripting (xss) cheat sheet contains many vectors that can help you bypass wafs and filters. you can select vectors by the event, tag or browser and a proof of concept is included for every vector. you can download a pdf version of the xss cheat sheet. this is a portswigger research project. follow us on twitter to receive updates. Stored (or persistent) xss occurs when an injected payload is saved on the server (e.g., in a database) and later displayed to users. since the malicious script is stored, every user who visits the affected page runs the payload, making this one of the most dangerous xss vulnerabilities. example payloads:. Companies with a lot of attack surface and with old infrastructure have higher probability to have cross site scripting vulnerabilities. the bug bounty game is about calculating where potential vulnerabilities could occur.
Comments are closed.